update
This commit is contained in:
parent
e6c312a1ec
commit
a7aaccd2d5
9 changed files with 164 additions and 10 deletions
|
|
@ -1,3 +1,6 @@
|
|||
# brendan.mcdevitt.tech
|
||||
|
||||
this is the git repository for where i store my website files for brendan.mcdevitt.tech
|
||||
|
||||
# youtube-player guide:
|
||||
https://github.com/nathancy/jekyll-embed-video/blob/master/README.md
|
||||
|
|
|
|||
|
|
@ -1 +1,9 @@
|
|||
<iframe width="560" height="315" src="https://www.youtube.com/embed/{{ include.id }}" frameborder="0" allowfullscreen></iframe>
|
||||
<div class="embed-container">
|
||||
<iframe
|
||||
src="https://www.youtube.com/embed/{{ include.id }}"
|
||||
width="700"
|
||||
height="480"
|
||||
frameborder="0"
|
||||
allowfullscreen="true">
|
||||
</iframe>
|
||||
</div>
|
||||
|
|
|
|||
65
_posts/2023-1-22-st-brendans-fair-isle.markdown
Normal file
65
_posts/2023-1-22-st-brendans-fair-isle.markdown
Normal file
|
|
@ -0,0 +1,65 @@
|
|||
---
|
||||
layout: post
|
||||
title: "st. brendan's fair isle"
|
||||
date: 2023-01-22
|
||||
categories: misc
|
||||
youtubeId: 5Y5Gk8EQlIA
|
||||
---
|
||||
My father named me after St. Brendan the Navigator. I listen to this song every
|
||||
now and then and it makes me think of him. Here's to you dad:
|
||||
|
||||
{% include youtubePlayer.html id=page.youtubeId %}
|
||||
|
||||
```
|
||||
When I was a lad on the Emerald Isle
|
||||
I heard many stories both wondrous and wild
|
||||
About the great monsters and dragons that be
|
||||
That follow the ships as they sail on the sea
|
||||
Now I being an artist with canvas and paint
|
||||
I sailed with St. Brendan and his jolly saints
|
||||
We told all the people good-bye for a while
|
||||
We sailed to St. Brendan's fair Isle, fair Isle
|
||||
We sailed to St. Brendan's fair Isle
|
||||
|
||||
We being on the ocean for ninety-four days
|
||||
We came to a spot where the sea was ablaze
|
||||
Those demons from Hades were dancing with glee
|
||||
And burning the sailors alive on the sea
|
||||
Then St. Brendan walked on the blistering waves
|
||||
He threw all the demons back into their caves
|
||||
And all of the saints wore a heavenly smile
|
||||
We sailed to St. Brendan's fair Isle, fair Isle
|
||||
We sailed to St. Brendan's fair Isle
|
||||
|
||||
That night when the brethren were lying asleep
|
||||
A great dragon came up from under the deep
|
||||
He thundered and lightninged and made a great din
|
||||
He awakened St. Brendan and all of his men
|
||||
The dragon came on with his mouth open wide
|
||||
We threw in a cross and the great dragon died
|
||||
We skinned him and cooked him and feasted a while
|
||||
We sailed to St. Brendan's fair Isle, fair Isle
|
||||
We sailed to St. Brendan's fair Isle
|
||||
|
||||
At last we came to a beautiful land
|
||||
We all went ashore and we walked on the strand
|
||||
We took our long bows and we killed us some food
|
||||
Then we roasted it up and had pot-barbeque
|
||||
Then after a while we were singing a song
|
||||
We noticed the island was moving along
|
||||
We ate and we drank and we rode in great style
|
||||
We sailed to St. Brendan's fair Isle, fair Isle
|
||||
We sailed to St. Brendan's fair Isle
|
||||
|
||||
Oh, Brendan said, "boys, this is much to my wish
|
||||
We sail on the back of the world's biggest fish"
|
||||
"Hold tight to the rope now that pulls our oul ship
|
||||
For we'll need it me boys if this fish takes a dip"
|
||||
We sailed every ocean, we sailed every sea
|
||||
We sailed every spot that a sailor could be
|
||||
In forty-four days we sailed ten million miles
|
||||
We sailed to St. Brendan's fair Isle, fair Isle
|
||||
We sailed to St. Brendan's fair Isle
|
||||
|
||||
-- Jimmy Driftwood
|
||||
```
|
||||
|
|
@ -6,7 +6,7 @@ categories: security
|
|||
---
|
||||
# cve.org CNA Security Advisories
|
||||
## The data:
|
||||
The website hosted at cve.org has recently been revamped. They host the source
|
||||
The website hosted at [cve.org](https://www.cve.org/) has recently been revamped. They host the source
|
||||
code for the site at the following
|
||||
[url](https://github.com/CVEProject/cve-website).
|
||||
|
||||
|
|
@ -14,8 +14,8 @@ I wanted to know the organization names of each CNA and if possible, where they
|
|||
vendor security advisories. I was looking for a URL to each advisory for each
|
||||
vendor. This is so I can look into what
|
||||
the actual vendor is saying when they are being notified of security
|
||||
vulnerabilities. To obtain this infromation, we can look through the source
|
||||
code used in the CVE Project website.
|
||||
vulnerabilities. To obtain this information, we can look through the source
|
||||
code used in the CVE Project website.
|
||||
|
||||
On the website itself if you search the 'List of
|
||||
Partners' found [here](https://www.cve.org/PartnerInformation/ListofPartners)
|
||||
|
|
@ -34,7 +34,7 @@ Because of this, I can quickly pull this information that I want by writing a
|
|||
little bit of code. It's just your standard GET request and parse a JSON file.
|
||||
I like Ruby and both Python but I have been using Ruby longer, so I use that
|
||||
more for pulling data quickly like the JSON data we are working with today. You
|
||||
can find a [JSON
|
||||
can find the [JSON
|
||||
file](https://github.com/CVEProject/cve-website/blob/dev/src/assets/data/CNAsList.json) that the website uses to load the CNA information. We can write code that downloads this json file and parses it...like this!
|
||||
|
||||
```
|
||||
|
|
|
|||
42
_security/2022-05-18-cve-searcher.markdown
Normal file
42
_security/2022-05-18-cve-searcher.markdown
Normal file
|
|
@ -0,0 +1,42 @@
|
|||
---
|
||||
layout: security
|
||||
title: "Firefox add-on Cve Searcher"
|
||||
date: 2022-05-18
|
||||
categories: security
|
||||
---
|
||||
|
||||
# Firefox Add-on: [Cve Searcher](https://addons.mozilla.org/en-US/firefox/addon/cve-searcher/)
|
||||
## Problem:
|
||||
Whenever I would be reading a security blog or a security advisory you see
|
||||
cve-ids. cve-ids everywhere. SO many times I would pull up a new tab and search
|
||||
the cve-id, only to click the nvd and mitre links as the very first step,
|
||||
almost without fail every. single. time. I want to know the details about the
|
||||
cve-id, so it is only natural to want to see what nvd/mitre has to say about
|
||||
them. Opening new tabs and searching for a cve-id only to go to the same
|
||||
website each time becomes tedious. Maybe there is a way we can speed it up in the
|
||||
browser to make the experience less annoying.
|
||||
|
||||
## Solution:
|
||||
A firefox add-on that will allow you to highlight the cve-id text in the page and right click -> contextMenu will pop
|
||||
up that will allow you to view the cve-ids details at either [nvd](https://nvd.nist.gov/)
|
||||
or [mitre](https://cve.mitre.org/) websites. You can find the program [here](https://addons.mozilla.org/en-US/firefox/addon/cve-searcher/) in the firefox add-on store.
|
||||
#### Example screenshot
|
||||
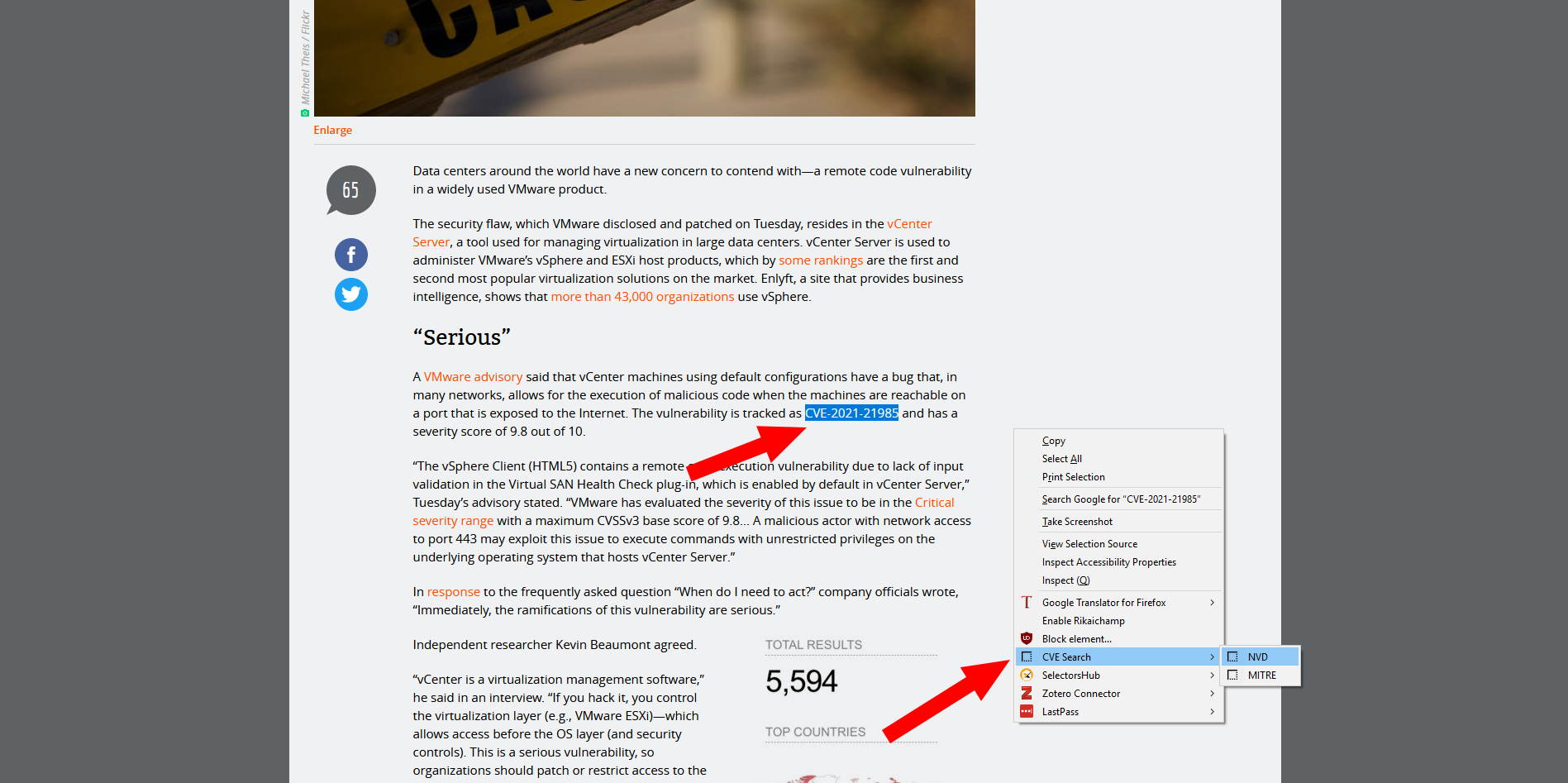
|
||||
Open this image in a new tab if you wish to see more detail.
|
||||
|
||||
## Improving workflow
|
||||
*My previous workflow*:
|
||||
1. highlight the cve-id mentioned in the advisory/blog and copy it to my copy buffer.
|
||||
2. open a new tab in my browser and google the cve-id.
|
||||
3. click the nvd/mitre links to pull up the content of the vulnerability like
|
||||
description and cpe data.
|
||||
|
||||
*My new workflow*:
|
||||
1. highlight the cve-id mentioned in the advisory/blog and right click
|
||||
2. click the nvd or mitre button from the contextMenu that appears for cve
|
||||
searcher and be taken directly to the appropriate page.
|
||||
|
||||
I hope this program can speed up your workflow like it has mine since I have
|
||||
started using it.
|
||||
I am learning about Manifest v3 so I will be able to port this for usage on
|
||||
Firefox when it supports v3 and also Chrome.
|
||||
|
|
@ -428,11 +428,19 @@ ul.security {
|
|||
background-color: #f1f1f1;
|
||||
}
|
||||
|
||||
@media only screen and (min-width: 481px) {
|
||||
/*@media only screen and (max-width: 481px) {
|
||||
body {
|
||||
padding-top: 24px;
|
||||
padding-right: 24px;
|
||||
padding-left: 24px;
|
||||
padding-bottom: 24px;
|
||||
padding: 24px;
|
||||
}
|
||||
|
||||
/
|
||||
*/
|
||||
|
||||
@import "minima";
|
||||
|
||||
@media screen and (max-width: 900px) {
|
||||
.site-nav {
|
||||
position: absolute;
|
||||
right: 90px;
|
||||
}
|
||||
}
|
||||
|
|
|
|||
19
css/video-embed.css
Normal file
19
css/video-embed.css
Normal file
|
|
@ -0,0 +1,19 @@
|
|||
/* Nathan Lam
|
||||
June 2, 2017
|
||||
Add this css for responsive embedded videos in your .css file. */
|
||||
|
||||
.embed-container {
|
||||
position: relative;
|
||||
padding-bottom: 56.25%;
|
||||
height: 0;
|
||||
overflow: hidden;
|
||||
max-width: 100%;
|
||||
}
|
||||
|
||||
.embed-container iframe, .embed-container object, .embed-container embed {
|
||||
position: absolute;
|
||||
top: 0;
|
||||
left: 0;
|
||||
width: 100%;
|
||||
height: 100%;
|
||||
}
|
||||
BIN
data/results.jpg
Executable file
BIN
data/results.jpg
Executable file
Binary file not shown.
|
After Width: | Height: | Size: 1.2 MiB |
|
|
@ -39,3 +39,12 @@ title: brendan mcdevitt
|
|||
{% endunless %}
|
||||
{% endfor %}
|
||||
</ul>
|
||||
|
||||
<h1>Endurance Training</h1>
|
||||
<ul class="endurance_training">
|
||||
{% for post in site.endurance_training %}
|
||||
{% unless post.title == 'endurance_training index' %}
|
||||
<li><span>{{ post.date | date_to_string }}</span> » <a href="{{ post.url }}"> {{ post.title }}</a></li>
|
||||
{% endunless %}
|
||||
{% endfor %}
|
||||
</ul>
|
||||
|
|
|
|||
Loading…
Add table
Reference in a new issue